Phishing and Cryptocurrencies : Uncovering the infrastructure of a network of scams

Every day, hundreds, if not thousands, of emails, text messages and social network posts are sent across the web as part of phishing campaigns, targeting innocent users with malicious intent. The popularisation of cryptocurrencies has led cybercriminals to adapt their techniques, devising increasingly sophisticated campaigns to extract these virtual assets from their victims.
In this article, I’ll take a closer look at the complex infrastructure behind one of these cryptocurrency scams, revealing some of the mechanisms used by cybercriminals.
Starting point: A message on WhatsApp
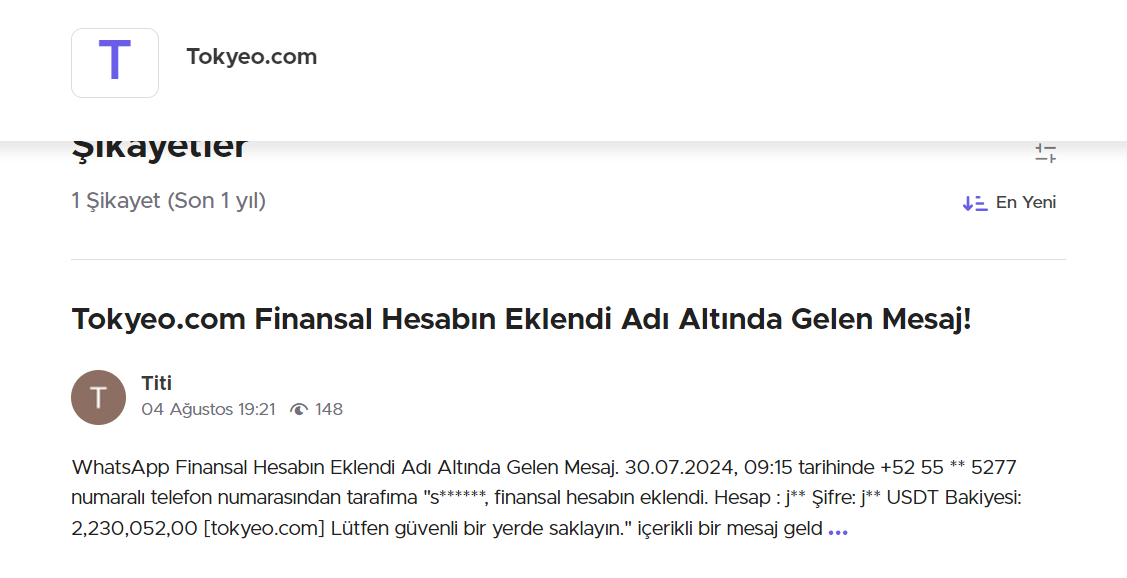
In February 2024, on my WhatsApp account, I received a phishing message claiming to be an automatic notification for the creation of an account on an unknown platform. The message contained login details and the “balance” of an account in USDT, showing an impressive amount of more than one million dollars. The scammer wanted me to believe that I had just received the details of a rather wealthy account by mistake and advised me, of course, to keep these identifiers in a safe place.

At first, I paid no attention to this phishing message and simply ignored it without deleting it. However, in July 2024, I received another phishing message on another WhatsApp account. Similar to the previous one, this message was written in a different language, contained a different URL and originated from an Indonesian number. This recurrence caught my attention and prompted me to take a closer look at this scam.
The numbers used, the countries of origin and the WhatsApp aliases present in the two phishing messages are not very relevant. It is highly likely that they come from numbers purchased en masse or obtained through SIM swapping. We’re going to take a closer look at the URLs:
- usdtasu[.]com
- aususdt[.]com
At the time of the investigation, the usdtasu domain was still active, whereas aususdt was no longer active. However, this didn’t stop me from continuing to investigate the latter.
Analysis of the platforms
The platform appears to be designed for mobile but also works on PC. It doesn’t have a clearly visible name or logo, but once in the “About Us” section, we learn that they are masquerading as a service called “USDT Wealth Management“. They present themselves as a one-stop service centre for VIP users, where you can discover all the ‘tailored wealth management opportunities’.

Using urlscan.io, we can see that aususdt and usdtasu are identical. The screenshot from 19 July shows the same interface. As the two platforms look identical, I concentrated first on the one that is still online: usdtasu.

The platform does not have a very complex design, with Bootstrap for the front-end and the ThinkPHP framework for the back-end.
It is also important to note that the platform uses 51LA (51.la). 51LA is a Chinese data collection and web traffic analysis service, comparable to Google Analytics, but specifically designed for the Chinese market. It offers tools for monitoring and analysing website visitors, as well as gathering statistics on site usage. In fact, as we explore the platform, we observe communications to “sdk.51.la” and “collect-v6.51.la”, which indicates that the site uses this service to monitor and analyse user traffic.
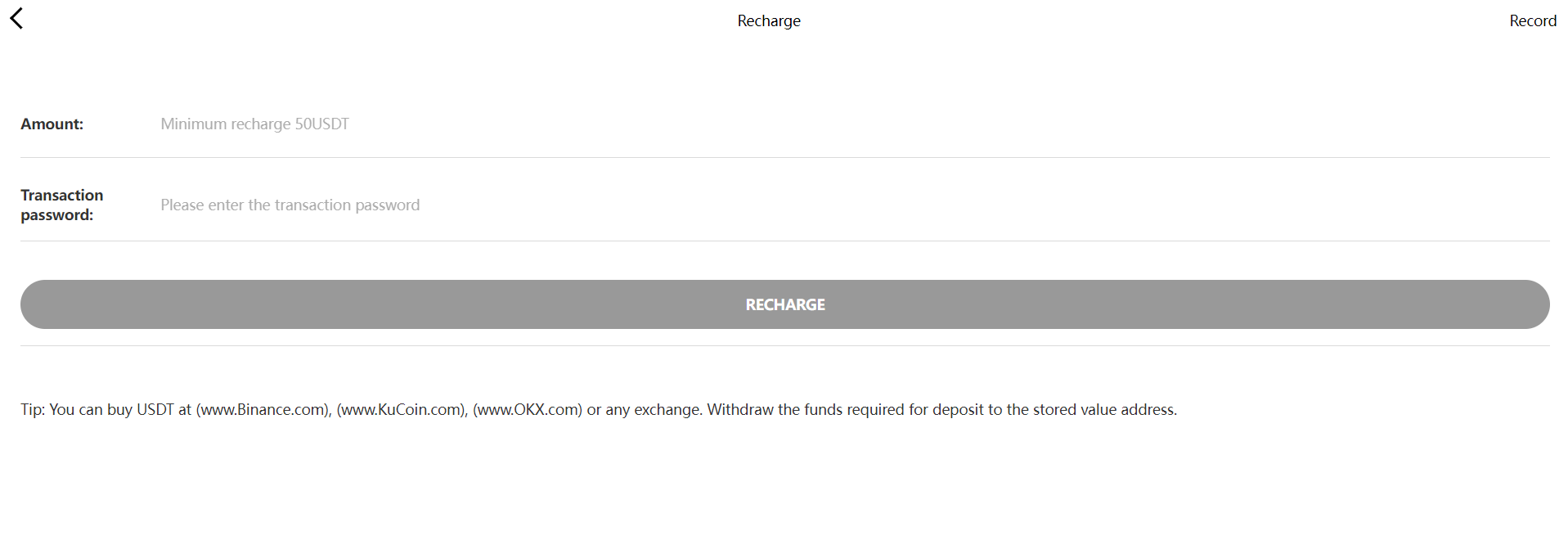
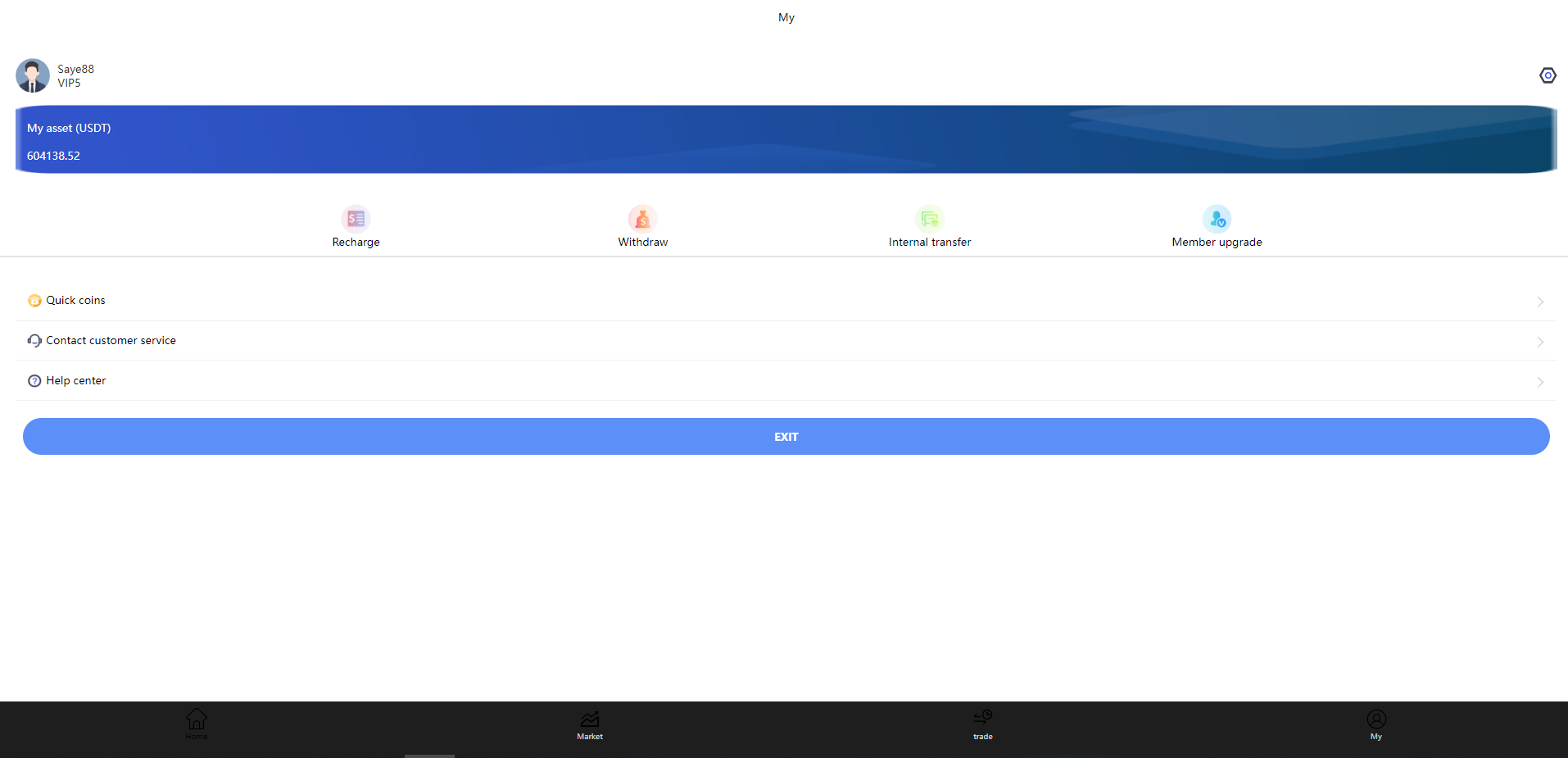
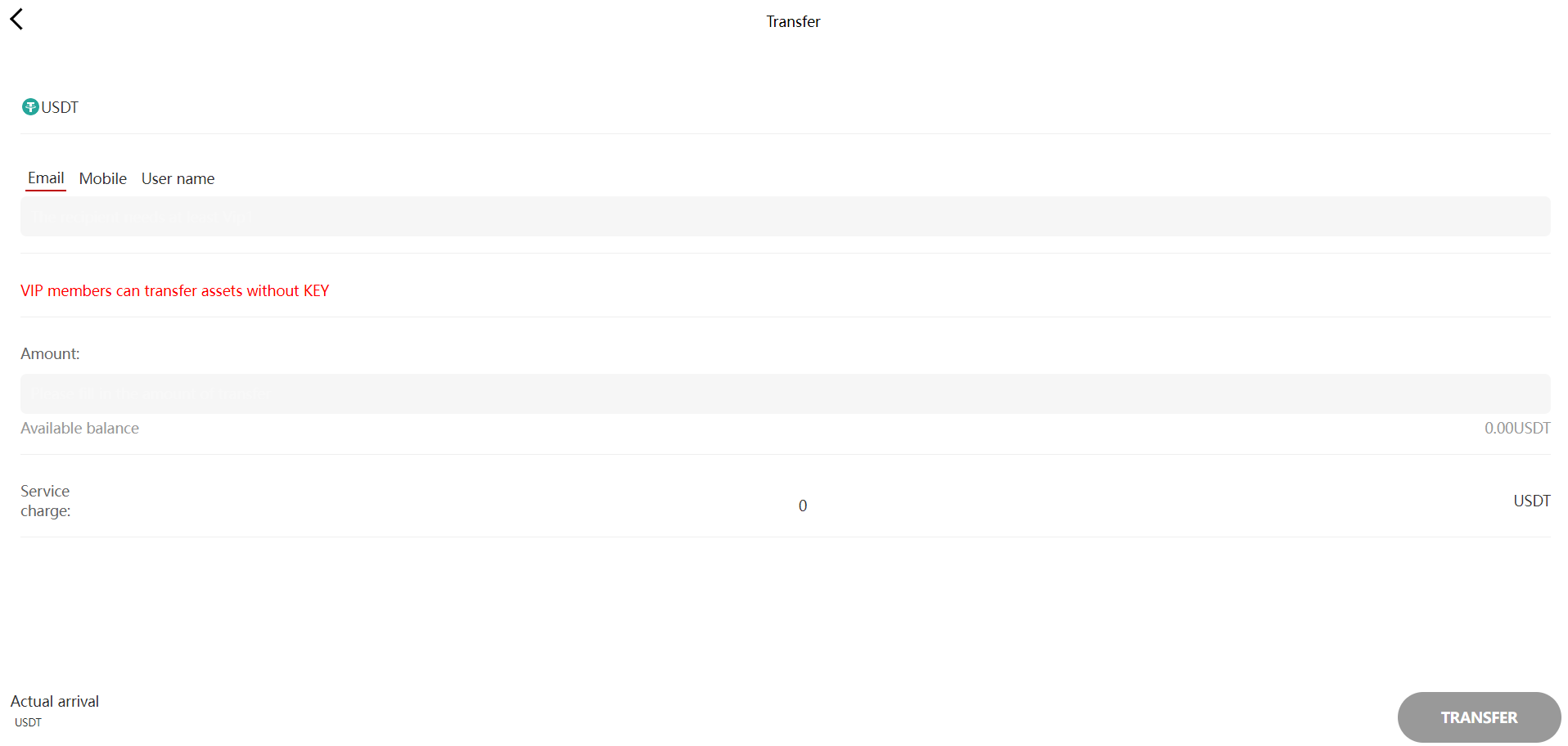
As mentioned earlier, it appears to have been designed primarily for mobile and not PCs. The platform doesn’t have very advanced features: it has a home page with a list of the various cryptocurrencies and their prices in US dollars. Similarly, in the “Market” section, there is this list of cryptocurrencies and their prices in US dollars, similar to what is displayed on the home page. The platform also includes a “Trade” section where users can purportedly top up their USDT account, withdraw money, make internal transfers on the platform and buy VIP ranks. Finally, there is a section for managing your account, allowing you to log in, create an account, and once logged in, access your account balance as well as a few settings.
In the “Trade” section, we also discover that the platform states that it cooperates with various cryptocurrency exchange platforms such as Binance and the discredited FTX.

In addition, on this same page, in order to simulate high activity on the platform, withdrawal or reload transactions by anonymised users appear randomly each time the page is refreshed.

In the account management section, you can also contact Customer Services. This option leads to a Gmail address: [email protected]. Unfortunately, when we used the Epeios tool to investigate this address, we found very little information, apart from the Google account linked to this address.
Slightly modifying the platform URL leads to error pages for non-existent pages. It would appear that the site is in debug mode, as ThinkPHP displays fragments of backend code. There are also several comments in Chinese.
ThinkPHP is a web development framework widely used in China, renowned for its ability to create fast, efficient web applications. The presence of this framework in the backend code, coupled with the use of 51.la for data collection and traffic analysis, as explained above, reinforces the hypothesis that the platform was probably developed by a team in China or East Asia, or that it was designed using tools popular in that region.
It is also interesting to note that the languages available on the platform include English, Arabic, Spanish, Turkish, Portuguese, Korean, French, German, Persian, as well as traditional Chinese, which is mainly used in Hong Kong and Taiwan. In China, simplified Chinese is the most widely used. This gives an idea of the countries potentially targeted by this phishing campaign.
Exploring the platform further, I discovered that when an account is created, an inactive wallet on the TRON blockchain (TRC20) is automatically generated. It is to this wallet that users must transfer cryptocurrency to top up their account. Each user is allocated a different wallet, but of course no one has the private keys to these wallets.
On the account provided to me, the transfer history on the platform shows that likely victims have already reloaded cryptocurrency to this account. However, as I do not have the “Transaction Password”, I cannot access the wallet address to check to which central wallet the cryptocurrency is being transferred by the cybercriminals behind this operation.
Let’s move on to the more technical aspect. A search of the DNS records for the usdtasu domain and a repeat of the old search on urlscan.io for the aususdt domain reveals these two IP addresses:
- 154.82.84.233
- 154.211.96.158
These two IPs are located in Hong Kong, according to a whois search, and belong to the same AS (Autonomous System) : Tcloudnet.

Using bgp.tools, we learn that Tcloudnet, AS399077, is associated with the AS name “TERAEXCH”. In addition, Tcloudnet says it is registered in the United States, in California, more specifically at 14252 Culver Dr #128, Irvine, California. This address corresponds to a UPS centre, which suggests that it is probably just a post office box.
Tcloudnet also has a WordPress site hosted on AWS and not on its own infrastructure: https://tcloudnet[.]com/.
A little research on this AS reveals that several command and control (C2) servers and malware are hosted on it and have been reported by the community, particularly on URLhaus and ThreatFox.
By accessing the two IP addresses directly, we can see that one of them displays an error in simplified Chinese, indicating that the site has not been found. On the other IP, on the other hand, we find a “Request Withdrawal” interface in Chinese. This interface apparently allows you to enter two API keys, a wallet address and the amount to be withdrawn.
When interacting with the interface, we receive an error message indicating access denied due to insufficient permissions. This error message reveals that the server is communicating with the API of the MEXC cryptocurrency exchange platform.
So it seems that the cybercriminals at the head of this network of scams are using the MEXC platform as part of their fraudulent operations.
After exploring the phishing platform, I took a closer look at the entire infrastructure behind it.
Discovery of the phishing infrastructure: A nebula of domain names
From the two domains and two IP addresses in my possession, I used various pivoting techniques, relying on a number of tools such as VirusTotal, Alienvault OTX, Censys and FOFA, to uncover all the elements making up these cybercriminals’ infrastructure.
Thanks to passive DNS replication on VirusTotal, I was able to identify around a hundred domain names linked to the IP address associated with the usdtasu domain. All these domain names were very similar, revealing a vast phishing infrastructure operating under almost identical identities.

The domain names are all very similar, each incorporating the name of a cryptocurrency such as USDT, BTC, BUSD, ETH, etc., followed by random characters. These domain names are probably generated by cybercriminals using a DAG (Domain Generation Algorithm). A DAG is an algorithm that automatically creates a large number of random or pseudo-random domain names. These names can then be used for malicious activities, making it more difficult for authorities to block or track the operations of cybercriminals, as new domains can be activated quickly if old ones are detected or blocked.
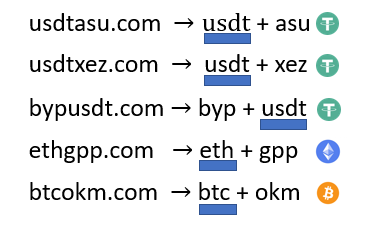
By accessing several of these domains, it is clear that they are all clones of the phishing platform. In fact, all the domain names found through passive DNS replication on VirusTotal, associated with malicious IP addresses dating back to 2023 and 2024, are copies of the same phishing platform. After running a few tests, I also found that all the platforms associated with the same IP generally share the same backend. This means that it is possible to log in with the same account on several platforms sharing the same IP. However, when you try to connect to a platform hosted on another IP, the connection fails and you get a message saying that the account does not exist.
By proceeding in the same way with the IP address linked to the aususdt[.]com domain, I discovered six new domain names, quite similar to those found previously. Unlike aususdt[.]com, these domains are functional and host the phishing platform. While exploring these platforms, I noticed that they display a different contact email address to the one found on the platforms hosted on the other IP.

While I was recovering all the domain names, thanks to the passive DNS history on VirusTotal, I also discovered the old IPs used by some of these malicious domains. In addition, I was able to identify some domain names that had migrated to other IPs, some still under the same AS, Tcloudnet, while others had been transferred to different ASes.
By repeating the same pivoting techniques on the various new IPs found, I finally identified more than 200 malicious domain names and 11 malicious IPs (the list of IoCs is available at the end of the article).
By analysing all the data collected, I noticed that certain platforms, although hosted on different IPs, share the same contact email address. The same principle applies here: all the phishing platforms on the same IP have a common backend and share the same contact email address. This allowed me to set up clusters based on these email addresses. In total, three distinct clusters were identified, each corresponding to a different email address, spread across the servers found. What’s more, when analysing all the clusters, I noticed that one of the three does not use 51.LA for data collection and analysis.

As I investigated further, using other tools such as the Hybrid Analysis sandbox and employing techniques such as pivoting through HTTPS certificates using tools such as crt.sh, I discovered a domain name hosting a different platform to those previously identified: one with similar functionality but a different design.
A network of phishing platform variants
While investigating the domain name “btckjp[.]com“, I came across “btckip[.]com“, a variant of our phishing platform. Although similar in terms of functionality, this platform has a slightly different design. It also appears to have been designed primarily for mobile devices, but remains functional on PCs.
Unlike the previous platform, this one offers users the option of withdrawing their cryptocurrencies directly in US dollars from their bank account, provided they enter their bank details on the platform.
This platform, unlike the previous one which posed as an organisation called “USDT Wealth Management“, this time presents itself as the official team behind Tether (USDT).
Apart from that, I didn’t notice any major differences. The platform works on the same principles as its predecessor, with the creation of a portfolio for each user. It is also developed in ThinkPHP, but unlike the other one, it does not use the 51.LA service for data collection. In addition, it is hosted on the same AS, Tcloudnet.
By repeating the pivot methods as performed previously, I managed to discover several variant clusters of our initial platform. All these clusters have similar characteristics and operate mainly on the same principle: a common backend per IP.

One of the clusters was particularly interesting because it offered a feature that the others did not: a live support service via a website chat. In fact, several phishing platforms, notably those hosted on the IPs “206.238.76.98” and “206.238.77.234“, had this additional functionality. When the support button was clicked, a chat was opened on the “supports-usdts[.]top” domain.
Live chat has a list of commands that can be used to obtain quick answers using a bot. These commands facilitate interaction with the support service by providing automatic answers to common questions.
The bot also occasionally displays a message saying that if customer service does not respond, it is advisable to contact a Gmail address for any urgent requests.

The site also offers several languages, but it seems that the commands available in live chat are only available in English.
Aside from this interesting feature, this cluster includes several notable domain names, including :
– wazirx77[.]com
– wazirx89[.]com
– wazirx77[.]site
– wazirx9[.]com
– wazirx7[.]com
– wazirx89[.]me
– wazirx77[.]live
– wazirx88[.]com
– wazirx99[.]com
These domains appear to be examples of typosquatting, a technique where domain names are designed to imitate legitimate websites and in this case the Indian cryptocurrency exchange platform WazirX (https://wazirx.com). Given that WazirX is mainly used in India, it is likely that this phishing campaign is targeting users in that country.

Unlike the typosquatting techniques used by more skilled cybercriminals, the phishing platforms on these malicious domains bear no resemblance whatsoever to the genuine WazirX platform.
While investigating this network of variants of the phishing platform, I also discovered certain “anomalies”: platforms present on the same IP did not display the same contact email.
On the trail of IoCs: Even more domain names
Although I already have a good number of IoCs (Indicators of Compromise), it is possible to discover more. Further research on platforms such as Censys and FOFA, or using reverse image search techniques on phishing platforms, could identify even more malicious servers and domain names. I have tried to be exhaustive, but it is likely that there are still malicious domain names and IPs that I have not yet detected.
For the purposes of this investigation, I will stop here in the search for IoCs. We have already identified a considerable number of elements, including two phishing platform networks: the initial platform and its variant, as well as several associated clusters. We also have information on old IPs used by cybercriminals. This collection of IoCs should provide a solid basis for other analysts wishing to investigate this campaign in greater depth, as well as guiding corrective action in terms of defences.

Decrypting the phishing campaign
The main aim of the phishing campaign analysed in this article is to trick victims into stealing their cryptocurrencies. At the same time, it also seeks to collect banking information from people unfamiliar with cryptocurrencies but wishing to engage with them, posing as legitimate exchange platforms such as Binance, Swissborg, and others.
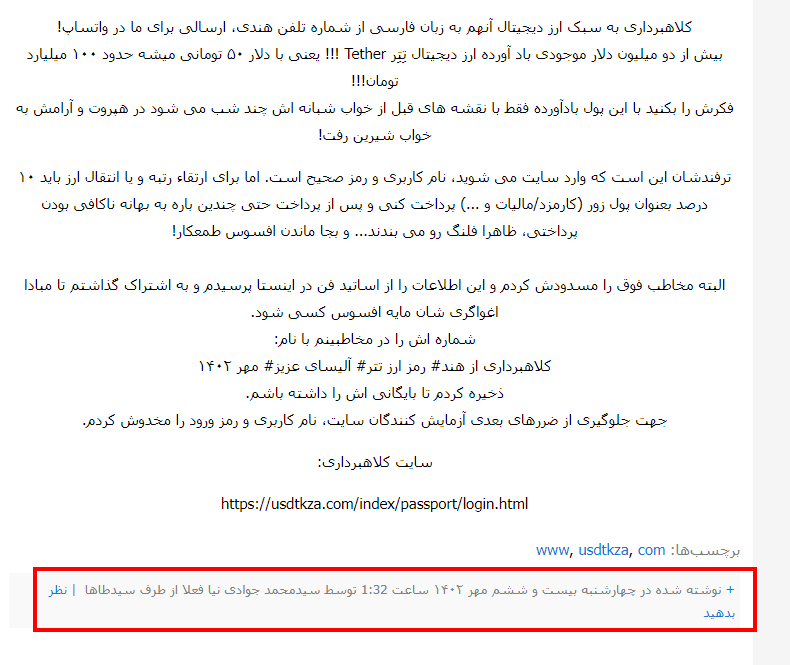
The first hints of this campaign, identified from open sources on the web, date back to October 2023, with victims mainly in Iran.

An article in Persian mentioning the scam linked to one of the domain names identified was spotted. It was therefore crucial to determine the publication date of this article. However, the date was written according to the Persian calendar, which meant that it could not be converted directly to the Gregorian calendar using a simple translation.
To solve this problem, I used an online converter, which enabled me to determine that the article was published in October 2023.
Let’s get back to decrypting the phishing campaign. It’s possible that the campaign began before October 2023, but I haven’t found any open-source elements from users targeted earlier. The campaign then spread and intensified in 2024, increasing the number of victims in various countries.
Open source research revealed that the campaign impacted individuals in several countries, including France, Russia, Iran, Pakistan, India, Italy, Lebanon, the United Arab Emirates, Belgium, the UK, Turkiye and Poland.
It is also important to note that the main distribution vectors for these phishing platforms are WhatsApp, email, Facebook Messenger and public Facebook groups. What’s more, this phishing campaign still appears to be active at the time of publication of this article.
Conclusion
In conclusion, this investigation has revealed a rapidly expanding phishing campaign, spread via WhatsApp, Facebook, and email, targeting cryptocurrency enthusiasts as well as those wishing to get into the business. This campaign, the first traces of which date back to October 2023, could be older and remains active to this day. By analysing the infrastructures using pivot techniques and examining the clues gathered, it is clear that the cybercriminals have set up a complex and well-organised network, aimed at avoiding detection by security tools such as Safe Browsing.
The elements uncovered, such as the use of the ThinkPHP framework, which is widely used in China, the integration of the 51LA service for data collection and analysis into certain platforms, and the predominance of Hong Kong-based servers under AS 399077, Tcloudnet (also known as TERAEXCH), point to a possible Chinese or East Asian origin for the cybercriminals. However, in the absence of further hard evidence, attribution with 100% certainty remains difficult.
Furthermore, it has not been possible to determine with certainty whether this campaign is the result of a Phishing as a Service (PhaaS), with several affiliates involved, or whether it is based on a phishing kit distributed by cybercriminals. It is also plausible that the same threat actor or group of cybercriminals is orchestrating this operation, given the similarities observed in the infrastructures of the various clusters identified.
It is crucial that users of cryptocurrencies, as well as those interested in them, remain vigilant and educate themselves to recognise the signs of a phishing attack. The cyber community continues to monitor these threats closely and will surely share information to better protect users globally. Given that this campaign is still active, it is likely that cybercriminals will continue to perfect their techniques to evade detection, making vigilance and collaboration all the more essential.
– Alb310
IoCs
IPs of servers
- 154.211.96.158
- 154.211.96.199
- 154.211.97.245
- 154.82.84.233
- 154.82.85.30
- 154.91.83.125
- 154.91.83.132
- 154.91.90.120
- 154.91.90.144
- 154.91.90.164
- 168.76.20.106
- 168.76.20.109
- 168.76.20.42
- 168.76.20.45
- 168.76.20.46
- 206.222.71.32
- 206.238.43.84
- 206.238.76.98
- 206.238.77.180
- 206.238.77.234
- 206.238.77.33
Domain names
- abpusdt[.]com
- afpusdt[.]com
- agpusdt[.]com
- ahpusdt[.]com
- ajpusdt[.]com
- aususdt[.]com
- bapusdt[.]com
- bavusdt[.]com
- bcpusdt[.]com
- bdpusdt[.]com
- bepusdt[.]com
- bfpusdt[.]com
- bgpusdt[.]com
- bhpusdt[.]com
- bjpusdt[.]com
- bkpusdt[.]com
- blpusdt[.]com
- bnpusdt[.]com
- bopusdt[.]com
- brpusdt[.]com
- bsceze[.]com
- bscfjr[.]com
- bscfki[.]com
- bscfur[.]com
- bscgth[.]com
- bscgyz[.]com
- bscijp[.]com
- bsckgz[.]com
- bsclny[.]com
- bscmfe[.]com
- bscmza[.]com
- bscnrl[.]com
- bspusdt[.]com
- bstyp[.]com
- btcasn[.]com
- btcbns[.]com
- btccoi[.]com
- btchjg[.]com
- btciee[.]com
- btciuy[.]com
- btckio[.]com
- btckip[.]com
- btckjp[.]com
- btckos[.]com
- btckss[.]com
- btckwe[.]com
- btcllk[.]com
- btcmts[.]com
- btcmui[.]com
- btcnit[.]com
- btcnuo[.]com
- btcnzv[.]com
- btcoaw[.]com
- btcoip[.]com
- btcoit[.]com
- btcokm[.]com
- btcoph[.]com
- btcopv[.]com
- btcoxc[.]com
- btcpai[.]com
- btcqqa[.]com
- btcsdw[.]com
- btcsweb3[.]com
- btctrp[.]com
- btcuio[.]com
- btcuyr[.]com
- btcvui[.]com
- btcwer[.]com
- btcwey[.]com
- btcxou[.]com
- btcyui[.]com
- btczaa[.]com
- btczmm[.]com
- btczqz[.]com
- btczzi[.]com
- btnliu[.]com
- btnpas[.]com
- btnqss[.]com
- btntuu[.]com
- btnybl[.]com
- btnyin[.]com
- btnzzv[.]com
- btofqw[.]com
- btouqw[.]com
- bupusdt[.]com
- busdej[.]com
- busdxu[.]com
- busebf[.]com
- busekt[.]com
- buselz[.]com
- busexs[.]com
- busfoq[.]com
- bushgh[.]com
- busiqo[.]com
- busivq[.]com
- busjtc[.]com
- busjxd[.]com
- buslfk[.]com
- buspdd[.]com
- busqzf[.]com
- busvdd[.]com
- busvmc[.]com
- busvzc[.]com
- busvzu[.]com
- busxna[.]com
- bvpusdt[.]com
- bwpusdt[.]com
- bxpusdt[.]com
- bypusdt[.]com
- bzpusdt[.]com
- cytusdt[.]com
- duausdt[.]com
- ehpusdt[.]com
- enakp[.]com
- eopusdt[.]com
- etchrg[.]com
- ethdhc[.]com
- ethdpo[.]com
- ethdun[.]com
- ethfdk[.]com
- ethfrr[.]com
- ethgpp[.]com
- ethgrr[.]com
- ethhva[.]com
- ethkop[.]com
- ethkpp[.]com
- ethlea[.]com
- ethmet[.]com
- ethrpp[.]com
- ethrse[.]com
- ethsey[.]com
- ethsro[.]com
- ethtev[.]com
- ethtri[.]com
- ethtyu[.]com
- ethyui[.]com
- etokcy[.]com
- etsbf[.]com
- etscz[.]com
- etsdh[.]com
- etsdt[.]com
- etskl[.]com
- etsob[.]com
- etspz[.]com
- etsxd[.]com
- etsxe[.]com
- etvusdt[.]com
- fedusdt[.]com
- gtrsvt[.]com
- imtoke[.]cc
- nasxa[.]com
- ncyvg[.]com
- nexkk[.]com
- nsuew[.]com
- nyeoh[.]com
- pfyhll15[.]com
- pfyhll30[.]com
- pufacd[.]com
- pufacf[.]com
- pufaci[.]com
- pufacl[.]com
- pufacm[.]com
- pufacn[.]com
- pufacp[.]com
- pufacu[.]com
- pufacv[.]com
- pufacx[.]com
- pufacz[.]com
- pufada[.]com
- pufadb[.]com
- pufadc[.]com
- saoix[.]com
- sbawr[.]com
- sdcne[.]com
- sebxn[.]com
- skchc[.]com
- sktxe[.]com
- slqcm[.]com
- ssrxe[.]com
- suports-usdts[.]top
- support-eths[.]top
- support-hk[.]icu
- svdca[.]com
- svpve[.]com
- szeou[.]com
- tokyeo[.]com
- usdcei[.]com
- usdtadae[.]com
- usdtadap[.]com
- usdtadaq[.]com
- usdtadar[.]com
- usdtadas[.]com
- usdtadat[.]com
- usdtadau[.]com
- usdtadff[.]com
- usdtado[.]com
- usdtadoc[.]com
- usdtadop[.]com
- usdtadpe[.]com
- usdtadpp[.]com
- usdtadsd[.]com
- usdtadsp[.]com
- usdtadss[.]com
- usdtadta[.]com
- usdtadtp[.]com
- usdtadtz[.]com
- usdtadxc[.]com
- usdtadzc[.]com
- usdtaear[.]com
- usdtaeas[.]com
- usdtaeba[.]com
- usdtaebb[.]com
- usdtaebd[.]com
- usdtaebq[.]com
- usdtaebr[.]com
- usdtaebs[.]com
- usdtaebw[.]com
- usdtaege[.]com
- usdtaegg[.]com
- usdtaegn[.]com
- usdtaegp[.]com
- usdtaei[.]com
- usdtaeod[.]com
- usdtaeop[.]com
- usdtaeos[.]com
- usdtaeou[.]com
- usdtaeow[.]com
- usdtaepy[.]com
- usdtaess[.]com
- usdtaew[.]com
- usdtagb[.]com
- usdtagd[.]com
- usdtaps[.]com
- usdtapw[.]com
- usdtapy[.]com
- usdtasf[.]com
- usdtasu[.]com
- usdtbbx[.]com
- usdtccab[.]com
- usdteab[.]com
- usdtipo[.]com
- usdtjpg[.]com
- usdtjpo[.]com
- usdtnab[.]com
- usdtskch[.]com
- usdtskcs[.]com
- usdtskdk[.]com
- usdtskib[.]com
- usdtskja[.]com
- usdtskjr[.]com
- usdtsknj[.]com
- usdtskoo[.]com
- usdtskpc[.]com
- usdtskpi[.]com
- usdtskpl[.]com
- usdtskpy[.]com
- usdtskro[.]com
- usdtsksh[.]com
- usdtskta[.]com
- usdtskva[.]com
- usdtskwb[.]com
- usdtskxm[.]com
- usdtskxo[.]com
- usdtskyc[.]com
- usdtssa[.]com
- usdtuab[.]com
- usdtuxb[.]com
- usdtxab[.]com
- usdtxdz[.]com
- usdtxez[.]com
- usdtxhn[.]com
- usdtxhz[.]com
- usdtxkn[.]com
- usdtxkz[.]com
- usdtxnz[.]com
- usdtxsz[.]com
- usdtxtz[.]com
- usdtxyn[.]com
- usdtzab[.]com
- usdtzad[.]com
- usdtzdp[.]com
- usdtzer[.]com
- usdtzop[.]com
- usdtzpo[.]com
- usdtzqo[.]com
- usdtzqp[.]com
- usdtzsw[.]com
- usdtzsx[.]com
- usdtzwu[.]com
- usonkd[.]com
- wazirx7[.]com
- wazirx77[.]com
- wazirx77[.]live
- wazirx77[.]site
- wazirx88[.]com
- wazirx89[.]com
- wazirx89[.]me
- wazirx9[.]com
- wazirx99[.]com
- yqsusdt[.]com
E-mail adresses
- btcioois[@]gmail.com
- btcotrcy[@]gmail.com
- ibtc333[@]gmail.com
- loyalancient1[@]gmail.com
- usdt8880[@]outlook.com
- usdtaa008[@]gmail.com
- usdtabb001[@]gmail.com
- usdtgrp[@]hotmail.com
- usdtreboot[@]gmail.com
- usdts486[@]gmail.com
- usdtsyz[@]gmail.com
- usdtyab[@]gmail.com