Dive into the shadows of an Iranian cybersecurity organization

Over the past decade, Iran has established itself as a major player in cyberspace by developing a structured and coordinated offensive apparatus, supported by a hybrid cyber ecosystem that blends state institutions, front companies, cyber-offensive groups, and academic structures. This ecosystem is based on close integration between the Ministry of Intelligence (MOIS), the Islamic Revolutionary Guard Corps (IRGC), and a network of civilian actors operating in direct support of the regime’s strategic objectives. It enables Iran to carry out espionage, sabotage, internal surveillance operations, and large-scale information manipulation campaigns, while maintaining a degree of plausible deniability on the international stage.
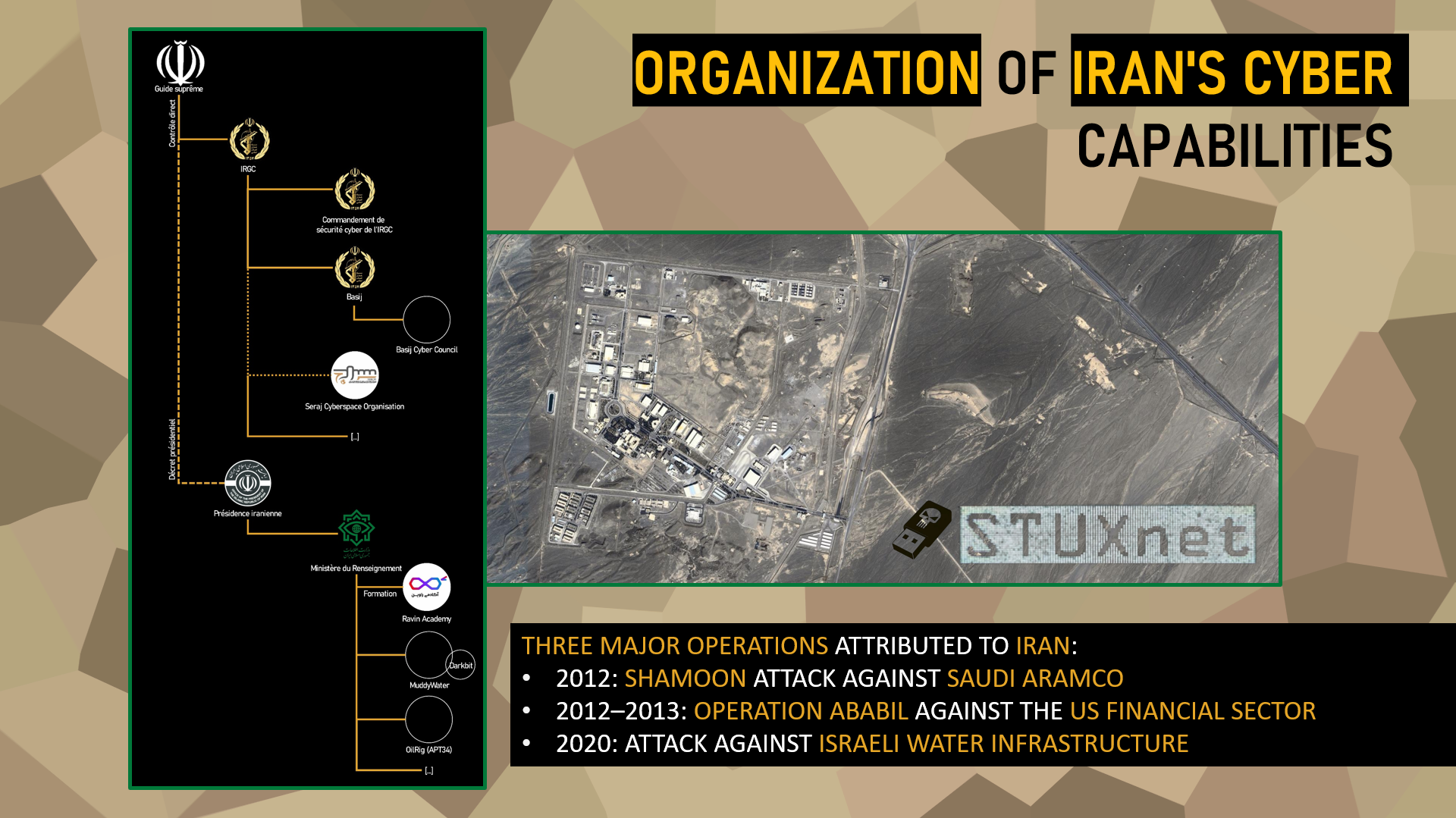
The organization of Iran’s cyber capabilities is not the result of isolated initiatives but is part of a centralized architecture designed to serve the regime’s strategic goals. This progressive structuring has been shaped by several major events.
Organization of Iran’s Cyber Capabilities
Iran’s cyber history took a decisive turn in 2010, when the Stuxnet computer worm, attributed to Israeli and American intelligence services, targeted its nuclear program, specifically the sensitive facilities at Natanz. This sophisticated attack damaged nearly one-fifth of Iran’s centrifuges, serving as a major wake-up call for Tehran. In response, Iranian authorities significantly accelerated the development of their own offensive capabilities in cyberspace.
This cyber arsenal is structured around two main poles: on one side, the Islamic Revolutionary Guard Corps (IRGC), which operates under the direct authority of the Supreme Leader. This paramilitary organization is designated as a terrorist entity by the European Union, the United States, and Saudi Arabia, due to its involvement in various regional operations. On the other side, there is the Ministry of Intelligence and Security (MOIS), which reports directly to the Iranian presidency. These two entities oversee distinct groups of hackers and cyber operators—sometimes in competition—reflecting internal power dynamics and rivalries within the state apparatus.
This structure has enabled Iran to conduct several major cyber operations, marking its rise as a significant actor on the international stage:
In 2012, the Shamoon attack on Saudi Aramco destroyed over 30,000 workstations, temporarily crippling the Saudi oil giant and sending a strong geopolitical signal in the regional context.
Between 2012 and 2013, Operation Ababil, orchestrated by a mix of state actors and affiliated malicious groups, targeted the U.S. financial sector through massive DDoS attacks against several major banks.
More recently, in 2020, a sophisticated cyberattack targeted Israeli water infrastructure, highlighting the growing technical capabilities of Iran and their integration into a broader regional strategy of influence and coercion.
These examples demonstrate the diversity of targets, the adaptability of operational methods, and the ambition of the Iranian regime to project power in cyberspace—not only for defensive purposes, but also as part of a long-term offensive and strategic influence doctrine.
As part of this investigation, our attention turned to one of the Iranian organizations that make up the hybrid ecosystem of Iran’s cyber capabilities: Ravin Academy.
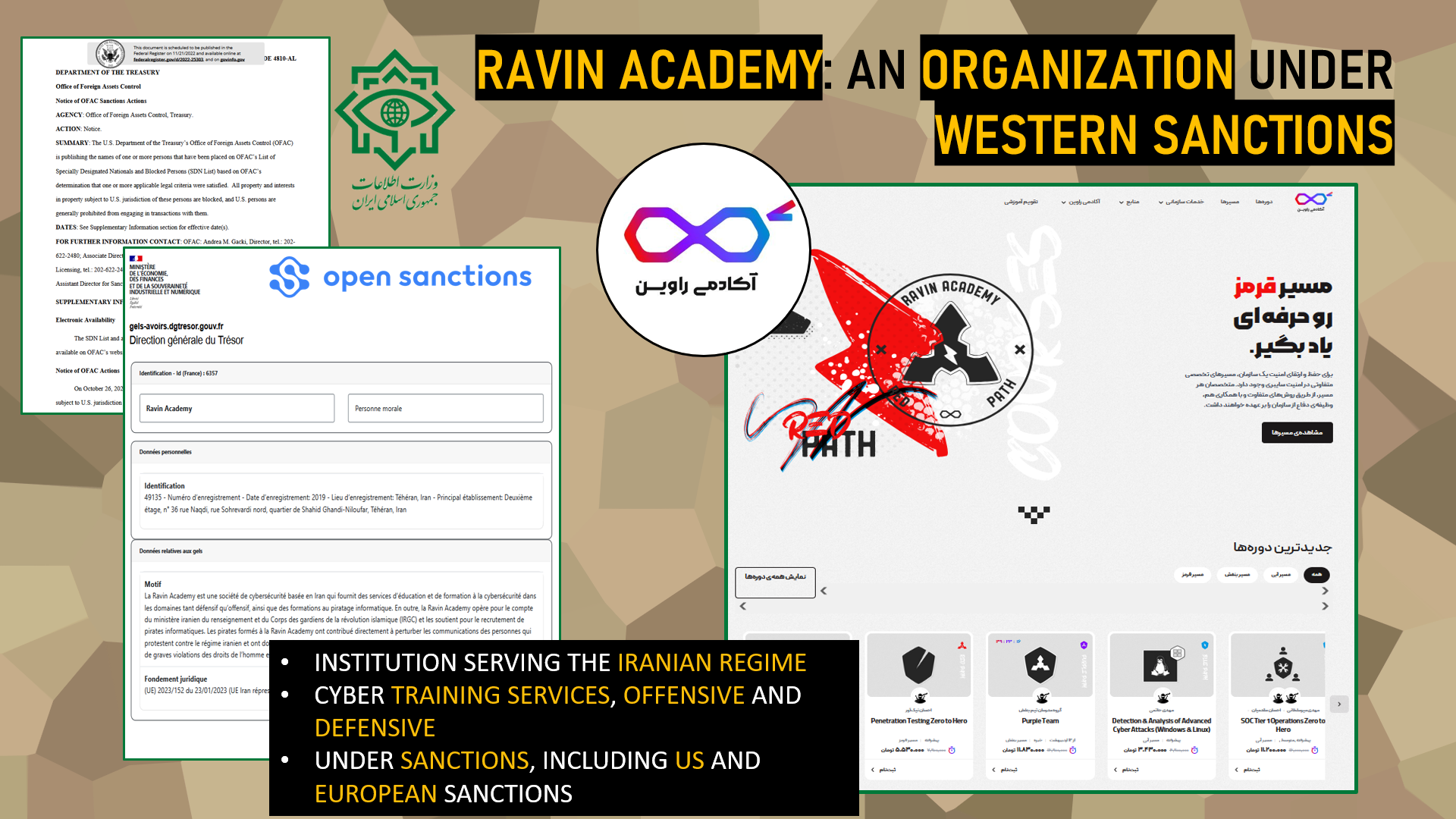
Ravin Academy: An Organization Under Western Sanctions
Founded in 2019, Ravin Academy officially presents itself as an Iranian institution specializing in cybersecurity training. It offers a wide range of courses, from offensive techniques to defensive strategies, much like the training programs found in many countries—including France. On paper, Ravin Academy functions as an academic center dedicated to developing cyber skills within a professional and educational framework.
However, behind this façade of a legitimate institution lies a far more complex reality. Since October 2022, Ravin Academy has been subject to international sanctions imposed by the United States, the United Kingdom, and the European Union, including France. These sanctions are based on evidence directly linking the organization to the Iranian Ministry of Intelligence and Security (MOIS). According to Western authorities, Ravin Academy is not merely a training center, but a recruiting ground for the regime’s future hackers, a breeding ground for cyber operators engaged in offensive operations serving Iran’s strategic objectives.
This dual nature, academic training on the surface, covert operational function beneath, perfectly illustrates Iran’s hybrid strategy, which blends apparent legitimacy with clandestine activity. Ravin Academy is thus part of a broader network that strengthens the regime’s cyber capabilities while maintaining enough plausible deniability to obscure its true role on the international stage.
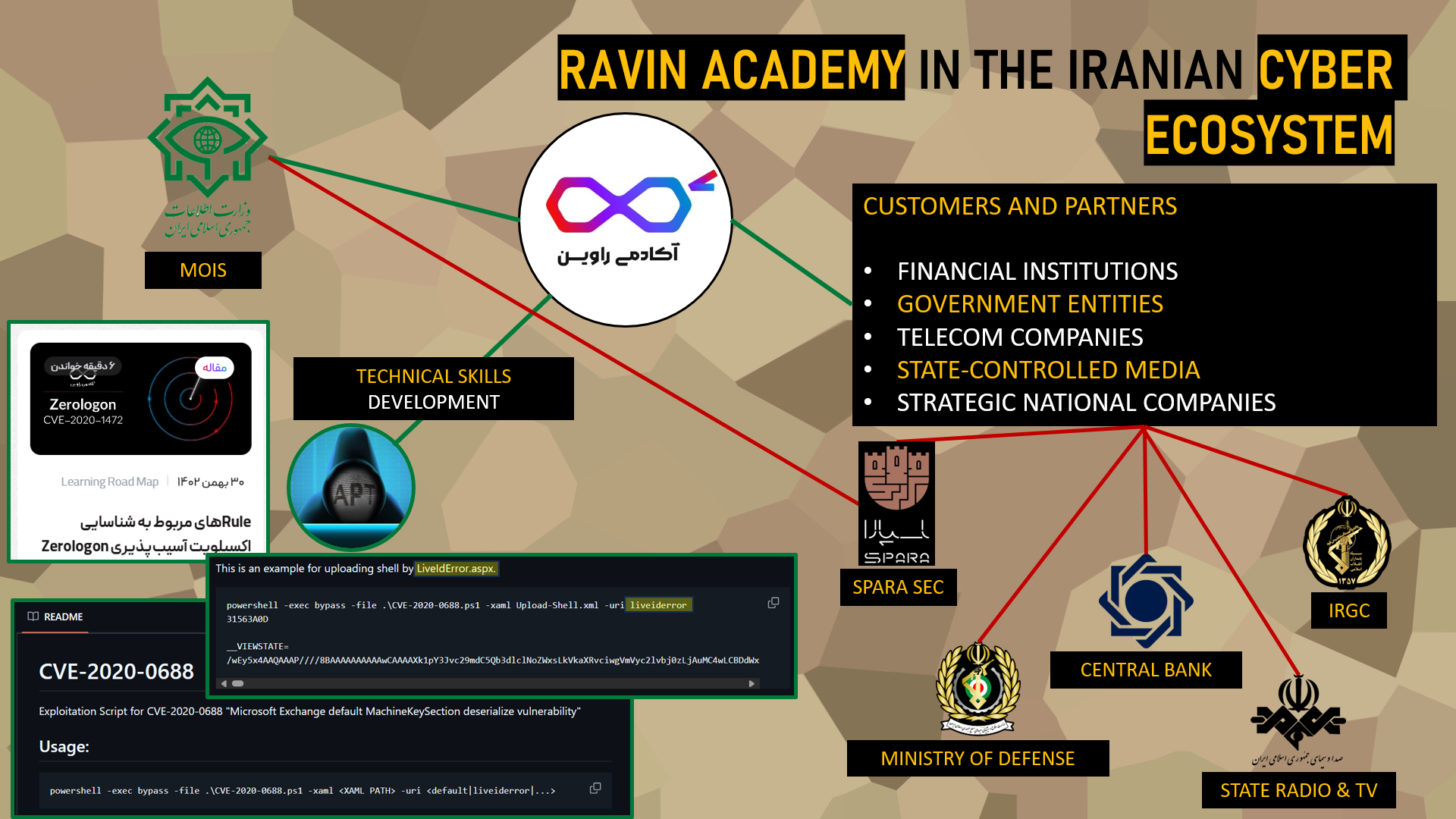
Ravin Academy holds a particularly intriguing position within Iran’s cyber ecosystem, sitting at the intersection of academic, state, and operational spheres. Among the many companies and organizations listed as clients or partners of the academy, several are themselves under Western sanctions, reflecting the breadth and depth of its ties to the regime.
Among these entities are organizations designated as terrorist groups by multiple governments, such as the Islamic Revolutionary Guard Corps (IRGC)—a paramilitary force central to Iran’s military and cyber strategy. Other sanctioned actors, such as Iran’s state broadcaster, the Central Bank of Iran, and even the Ministry of Defense, also appear in Ravin Academy’s network of collaborators. To this are added lesser-known companies, such as Spara Sec, a shadowy firm whose activities will be examined in more detail later in this investigation.
Ravin Academy is not only in the crosshairs of Western state authorities; it has also become the target of alerts issued by several Cyber Threat Intelligence (CTI) teams within specialized cybersecurity companies. In November 2022, the firm PwC released a detailed CTI report denouncing Ravin Academy’s direct involvement in malicious activity. According to this report, the academy provides active technical support to multiple Iranian APT (Advanced Persistent Threat) groups, which are recognized as state-aligned cyber units engaged in offensive operations abroad.
PwC’s technical investigation notably draws on the analysis of Ravin Academy’s public GitHub repositories, shedding light on tools, code contributions, and development patterns that link the institution to coordinated cyber campaigns.
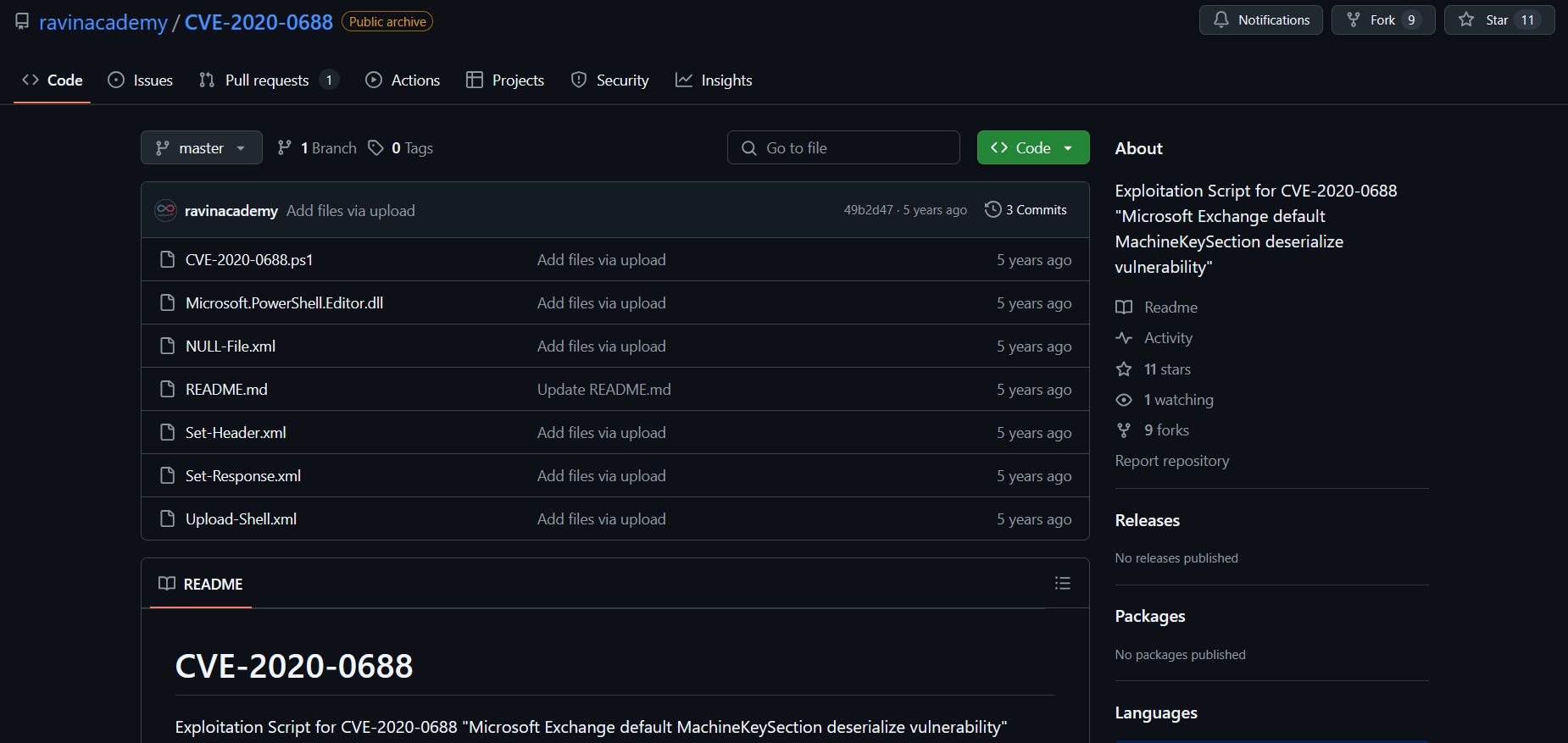
These archives contain, among other elements, a Proof of Concept (PoC) exploiting the CVE-2020-0688 vulnerability, a critical flaw that has previously been used by Iranian threat actors to breach systems. Strikingly, analysts identified in this GitHub repository file naming conventions, code structures, and command patterns identical to those observed in real-world attacks attributed to APT groups affiliated with the Iranian regime.
This technical correlation allowed PwC to draw a near-direct link between Ravin Academy and these offensive cyber groups, thereby confirming the operational role of the academy in Iran’s cyber warfare strategy.
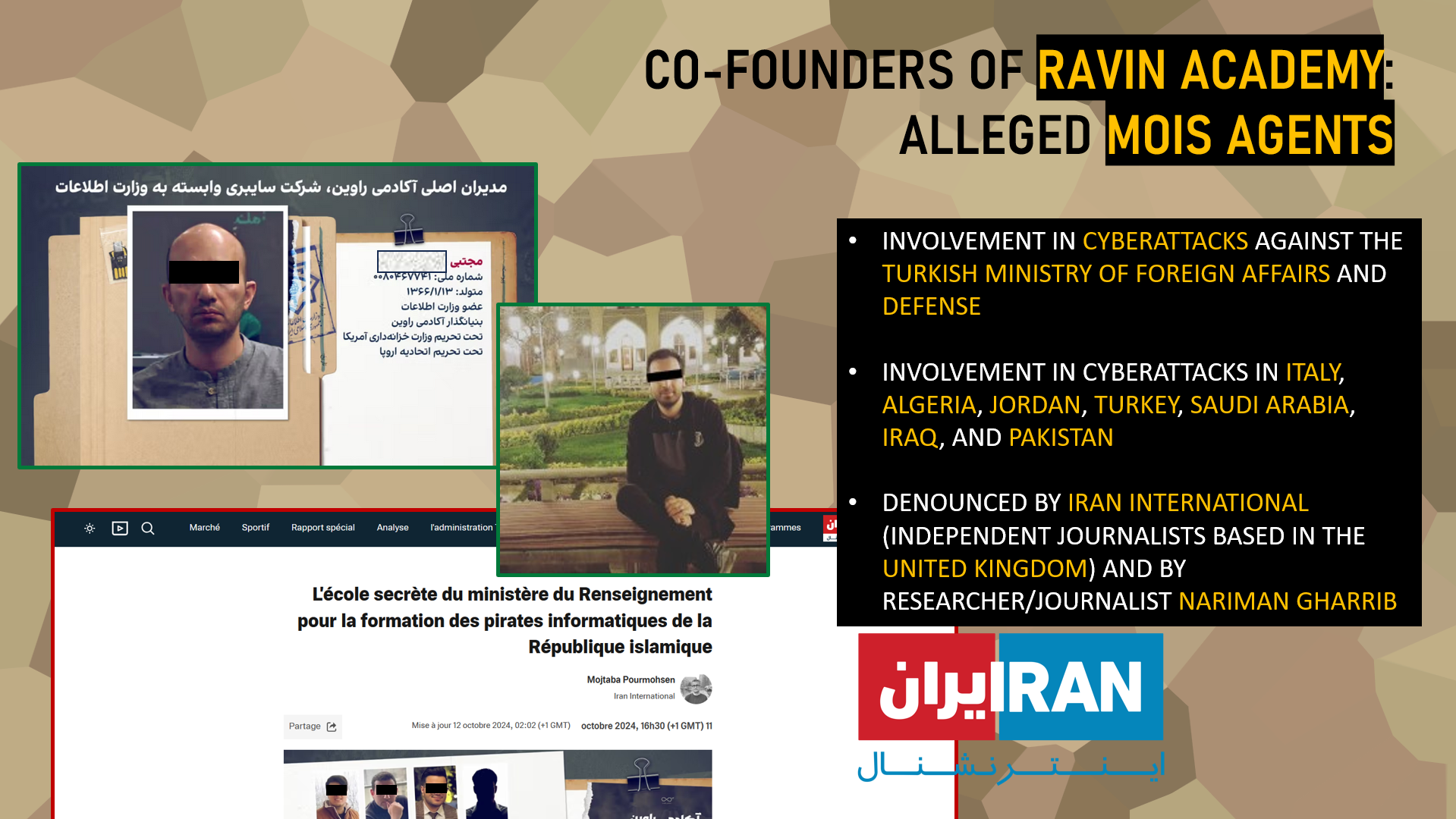
To fully understand the role and influence of Ravin Academy, it is essential to look at its founders. The two co-founders, who are now under Western sanctions, were revealed by several media investigations, notably by Iran International, an independent opposition media outlet based in the United Kingdom, known for its investigative work on Iranian networks. Researcher and journalist Nariman Gharrib also contributed to exposing their profiles, describing them as presumed agents of the Iranian MOIS (Ministry of Intelligence and Security).
According to Iran International’s revelations, under the leadership of these two individuals, Ravin Academy allegedly played an active role in the preparation and technical support of cyberattacks against several foreign states. Among the most notable targets are the Turkish ministries of Foreign Affairs and Defense, as well as institutions in various countries (Italy, Algeria, Jordan, Saudi Arabia, Iraq, and Pakistan). These operations, attributed to the organization, highlight its direct involvement in projecting Iranian cyber power regionally and internationally.
These elements demonstrate a deliberate strategy to use Ravin Academy not only as a training center but also as an operational platform serving the geopolitical ambitions of the regime.
The Profiles Behind Ravin Academy
Thanks to OSINT, we were able to leverage a significant portion of Ravin Academy’s digital footprint, which allowed us to identify an extensive network of actors directly or indirectly linked to the organization. Among them are the co-founders, instructors specialized in blue team (defense) and red team (offense) training, as well as several external contributors often called upon to strengthen the academy’s technical or strategic expertise. Cross-analysis of these profiles provides valuable insight into Ravin Academy’s internal structure and operating methods.
Within this overview, we have selected certain profiles that are particularly revealing.
Farzin K. and Mojtaba M.: APT MuddyWater and OilRig
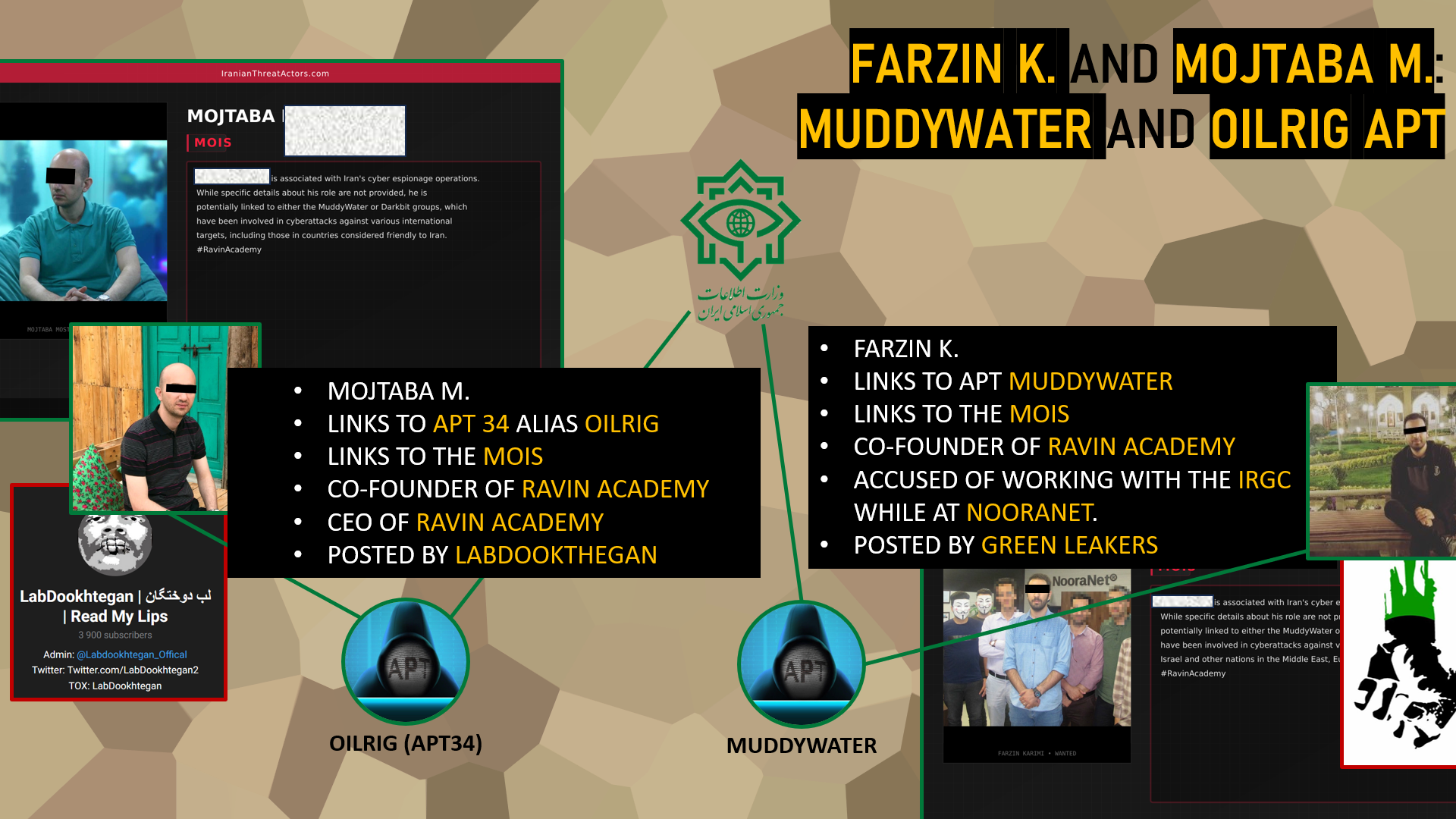
To better understand the nature and orientation of Ravin Academy, it is crucial to revisit its two co-founders, whose backgrounds reveal close connections with major Iranian state-sponsored cyber groups.
Farzin K., co-founder of Ravin Academy, was identified as early as 2019 by the whistleblower group Green Leakers on Telegram. He is described as the former leader of the Iranian APT MuddyWater and an active agent of the Ministry of Intelligence and Security (MOIS). Before founding the academy, Farzin K. reportedly collaborated with the Islamic Revolutionary Guard Corps (IRGC) through his work at Nooranet, a company closely linked to the regime. For those unfamiliar, MuddyWater is a cyber espionage group known for its targeted operations since 2017, primarily in the Middle East but also globally. This group continues to conduct espionage, information gathering, and infiltration campaigns, always serving the strategic interests of the Iranian regime.
The second co-founder, Mojtaba M., serves as the general manager of Ravin Academy. In 2019, his name was mentioned by the whistleblower and hacktivist collective Labdookhtegan, which identified him as a member of APT34, also known as OilRig, and an agent of the MOIS. For those unfamiliar, OilRig is an Iranian state-sponsored hacker group active since at least 2014, specializing in cyber espionage operations, supply chain attacks, and sabotage campaigns. Like MuddyWater, OilRig remains a major player in Iran’s offensive cyber strategy, still active today.
The direct involvement of these two key figures in the governance of Ravin Academy confirms the strategic role of this institution within the continuum of Iranian cyber offensive operations, acting both as a training center and an operational relay for the MOIS.
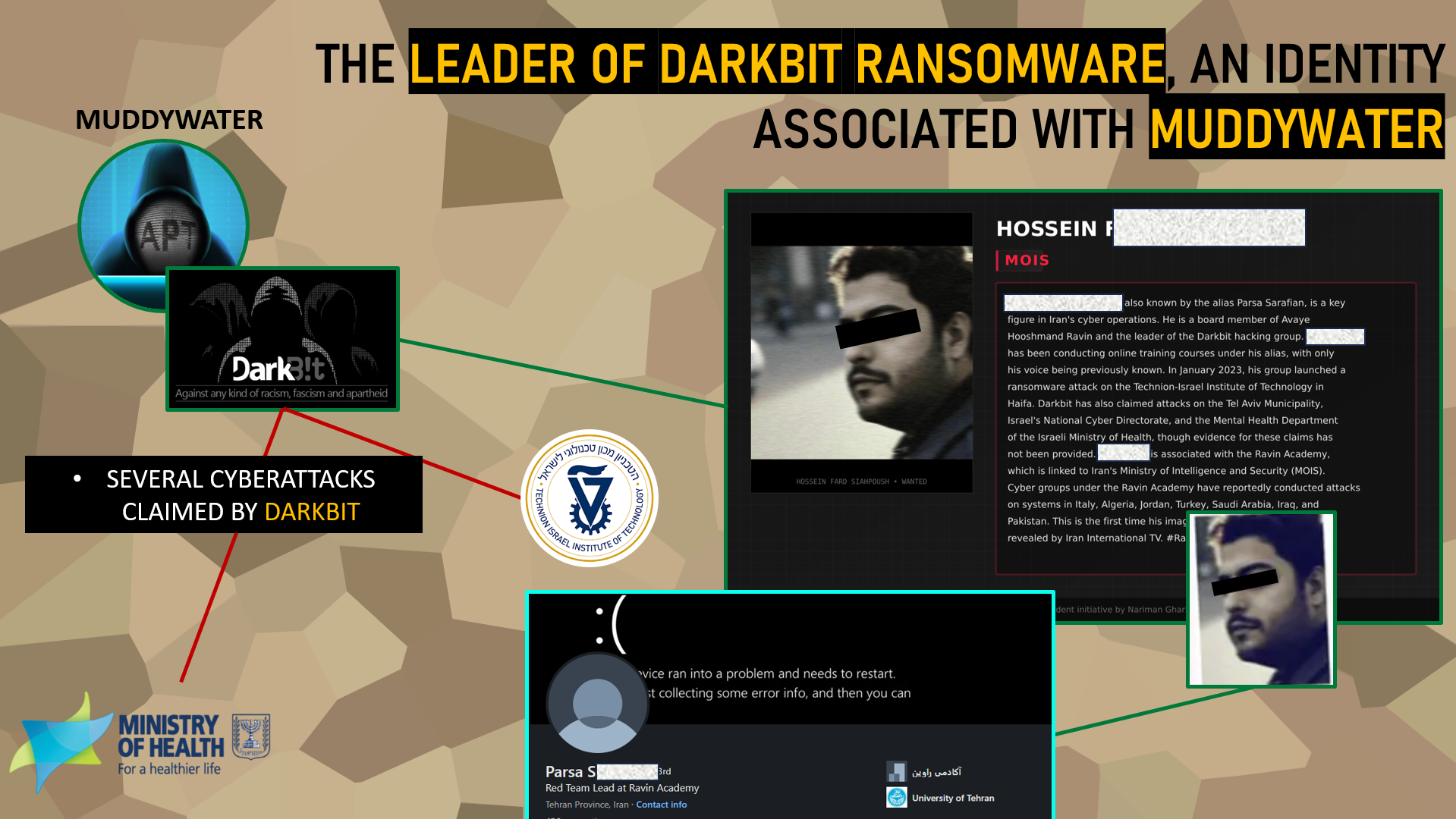
The leader of Darkbit ransomware, an identity linked to MuddyWater
Among the other figures identified within Ravin Academy, Hussein F. S. draws particular attention. Known by the pseudonym Parsa S. within the academy, he is recognized as the leader of the Darkbit ransomware group. This identity was revealed by Iran International, which also published the only available image of him, thereby strengthening the traceability of this actor.
Darkbit has been responsible for several major cyberattacks targeting sensitive Israeli institutions, notably the Israeli Ministry of Health and the Technion University, attacks directly claimed by the group. For a long time, Darkbit was perceived as an independent hacktivist collective. However, in-depth investigations conducted by CTI teams have demonstrated that Darkbit is, in reality, a front, a fabricated identity controlled by the APT MuddyWater.
This tactic is not isolated: it fits into a recurring practice used by several Iranian groups, involving the creation of fake hacktivist groups to conceal direct state actor involvement in offensive operations. These false flags enable the Iranian regime to obscure trails, allow plausible deniability, and intensify its influence and sabotage campaigns in cyberspace.
Thus, like the co-founders previously mentioned, Hussein F. S. also appears closely linked to the Ministry of Intelligence and Security (MOIS), once again confirming the deeply strategic and controlled nature of the ecosystem surrounding Ravin Academy.
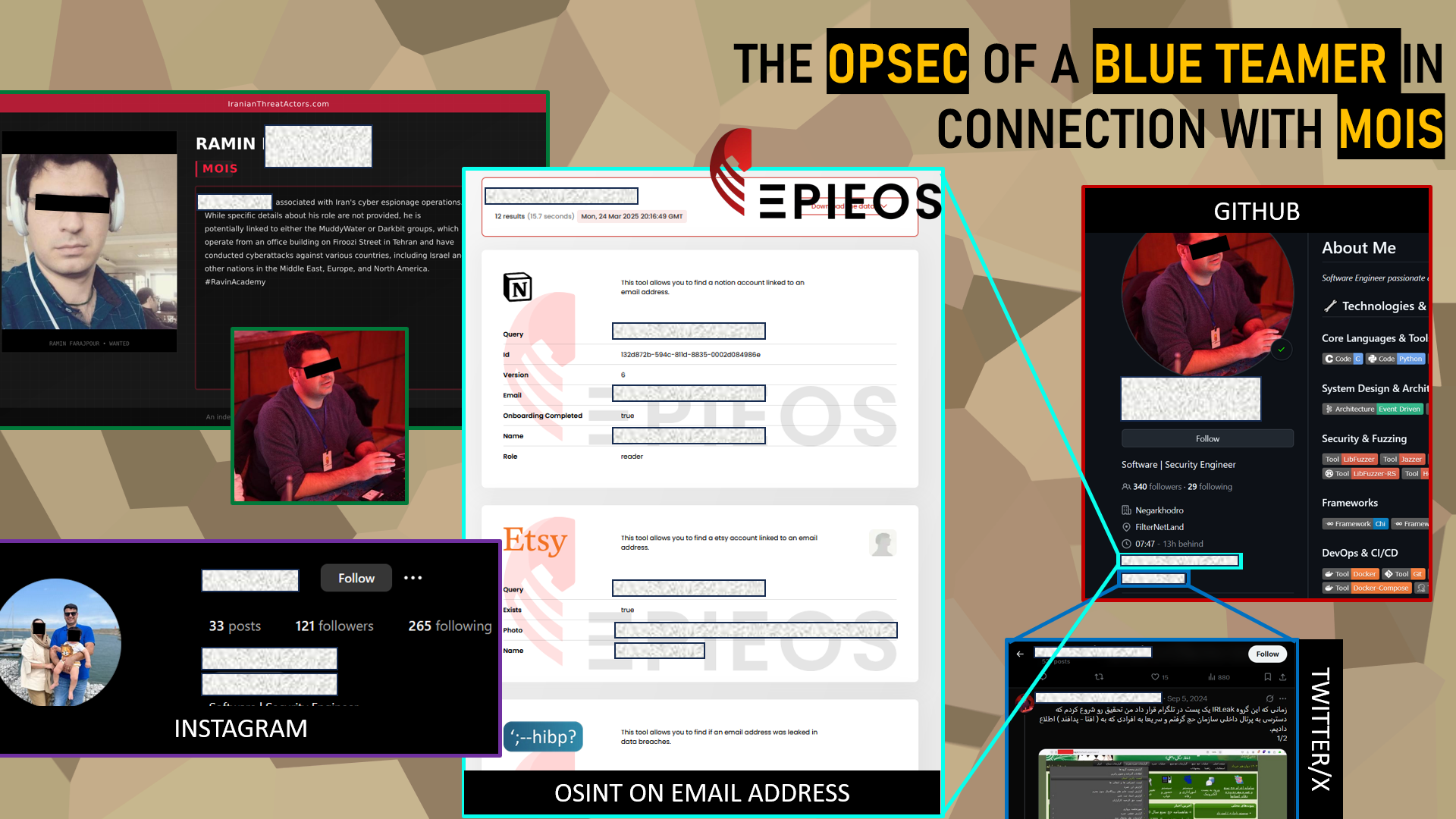
The OPSEC of a Blue Teamer linked to the MOIS
Among the various profiles identified within Ravin Academy, some occupy IT defense roles, often referred to as blue teamers. We chose to take a look at the relatively weak OPSEC (operational security) of one of them, whose digital traces reveal several interesting elements.
Ramin F., a teacher specializing in digital forensics at Ravin Academy, is suspected by cybersecurity researcher Nariman Gharrib of having links with MOIS and the MuddyWater APT. However, to date, no tangible public evidence has been put forward to confirm this link.
An OSINT analysis of his GitHub account has, however, enabled us to cross-check several clues: his profile links to his personal Twitter account as well as to his personal e-mail address. By exploring this Twitter account, we discovered that he had in the past communicated sensitive information relating to leaks to related contacts in the Iranian Ministry of Defense.
Thanks to OSINT tools like Epieos, it’s possible to link this e-mail address to several other online accounts: a Notion profile, an Etsy account where he uses the pseudonym Matthew, and an Instagram account whose profile photo shows him with his wife and child, giving rare visibility to his private life.
If these elements are not enough to formally confirm membership of an APT group like MuddyWater, the fact that Ramin F. evolves in a close circle of profiles with suspicious activities and close links to the Iranian regime makes him an actor to be closely monitored in the Iranian cyber dynamic.
Yashar S., aka Sc0rpion, aka Voorivex: From hacktivist to APT
Among the most striking profiles identified in the Ravin Academy network, that of Yashar S., also known by the pseudonyms Sc0rpion and Voorivex, stands out for a career closely linked to Iranian state cyber spheres.
Yashar appears to have begun his career as a hacker affiliated with the Iranian regime within the Izz ad-Din al-Qassam cybercombatants, a hacktivist group presenting itself as state-linked, and bearing the same name as an Iranian-backed terrorist organization. This collective has been accused of leading Operation Ababil between 2012 and 2013, a massive campaign of DDoS attacks targeting the US banking sector, attributed to Iran. These links have notably been discussed on forums such as SoldierX. Interestingly, however, while several members of this group have been sanctioned by the US, Yashar itself has not been subject to sanctions.
Yashar has also been associated with the ITSEC Team, a state-owned cyber group affiliated to the Islamic Revolutionary Guards (IRGC), some of whose members have been sanctioned by Washington. Again, Yashar has not been sanctioned.
Just like Mojtaba M., in 2019, the hacktivist group Labdookhtegan revealed that Yashar was linked to MOIS, more precisely to APT34 (or Oilrig), which is intriguing when we know the relationship between IRGC and MOIS, which has historically been marked by internal rivalries. This change of allegiance, from IRGC influence to MOIS tutelage, is a strong signal of the complex dynamics within the Iranian cyber ecosystem.
Public records, and in particular Ravin Academy tweets, show that Yashar has been an active player since the academy’s first year. In particular, he co-organized the “Lovely Hackers” event with them, an event dedicated to training and promoting cybersecurity.
Today, Yashar S. seems to have distanced himself from official Iranian circles. He now resides in Turkey, where he has set up his own training facility specializing in offensive cybersecurity, continuing to exploit his expertise while possibly operating outside the direct bosom of the Iranian regime.
Ravin Academy partner alleged MOIS agent
As previously mentioned, Ravin Academy regularly collaborates with external entities to enrich its educational offering and broaden its scope of action.
Our attention was caught by a document detailing an intensive 125-hour training program dedicated to “cyber threat hunting”. This program is jointly organized by Ravin Academy, Khatam University, and a company called Spara Security, whose logo can be seen on the training materials.
By investigating Spara Security, it is possible to discover that its CTO and co-founder, Omid P., is also designated as a MOIS agent by LabDookhtegan. The group claims to have solid evidence establishing a direct link between Omid P. and the Iranian intelligence services. In their statement, LabDookhtegan leave little doubt as to their determination: they promise “not to forget him” and even to offer a reward for any further information on what they refer to as “mercenary” Omid.
This connection between Spara Security and MOIS is a striking illustration of how the Iranian regime integrates companies with seemingly private profiles into its vast cyber ecosystem. It also raises legitimate questions about the real nature of some of the training courses offered by Ravin Academy, which can serve as both pedagogical vectors and operational relays for the regime’s strategic objectives.
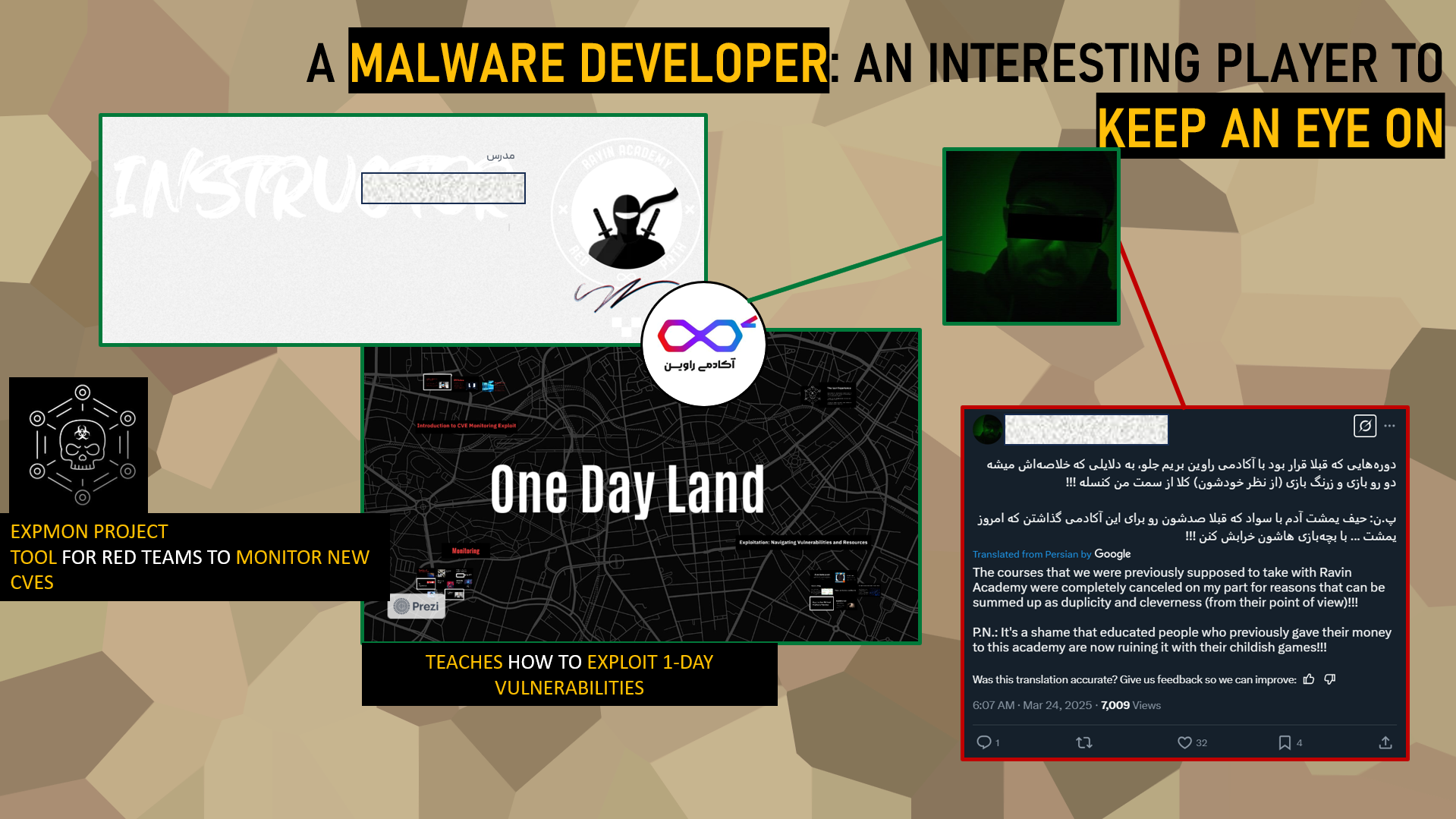
A malware dev: An interesting player to keep an eye on
Among the faculty of Ravin Academy, the profile of Iman R. stands out. A specialist in malware development, he operates in an ecosystem where ties with the Iranian Ministry of Intelligence (MOIS) and Iranian APT groups are common, warranting heightened vigilance.
Although OSINT investigations do not formally establish a direct affiliation between Iman and APT groups, his activities and positioning raise several questions.
Iman teaches advanced courses on exploiting ‘1-day’ vulnerabilities, which are recently discovered flaws for which no patch has been widely deployed. He teaches his students how to create operational exploits from these vulnerabilities, a skill highly sought after in offensive cyber operations.
Furthermore, he is the author of a tool called ‘Project Expmon’. This tool, accessible only to a restricted circle, primarily serves red teams by enabling real-time monitoring of new critical vulnerabilities (CVEs) detected in the global digital ecosystem.
What makes Iman‘s trajectory particularly interesting for intelligence analysts is his recent activity on social media. In a tweet dated March 24, 2025, he openly expressed his discontent with Ravin Academy, denouncing ‘duplicities’ and ‘schemes’ related to the cancellation of certain courses, revealing a fracture within the institution.
Such internal tensions represent a potential entry point for intelligence services and Cyber Threat Intelligence (CTI) teams. A key player in disgrace or in conflict with their organization can indeed become a valuable source of information on internal practices, sensitive programs, and hidden relationships with Iranian government entities.
This human vulnerability is therefore an essential angle of analysis for understanding the real dynamics within Ravin Academy and, more broadly, within the Iranian cyber ecosystem.
At the time this article is published, we have noticed that Iman has deleted his social media accounts.
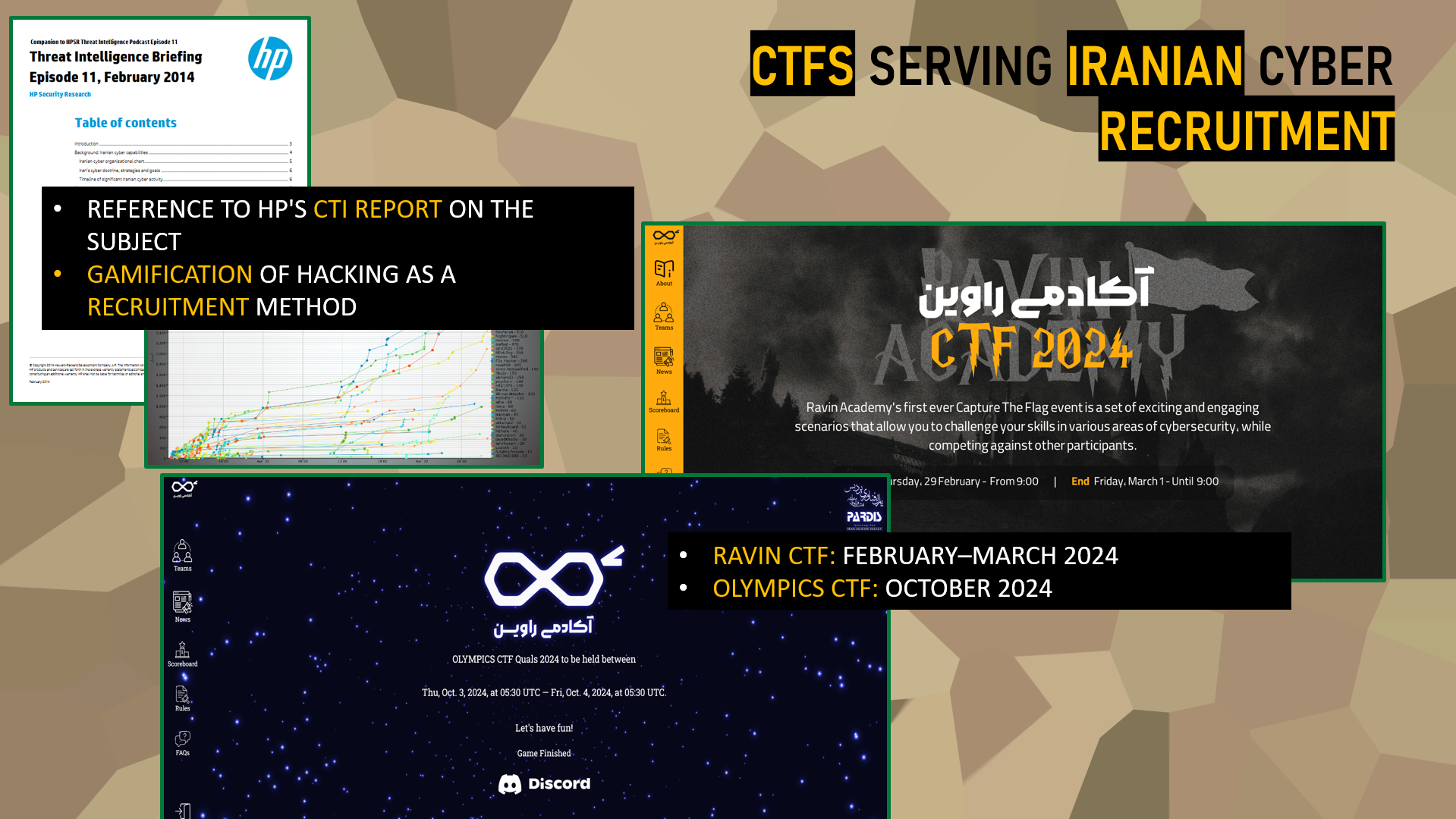
CTFs in the Service of Iranian Cyber Recruitment
To understand how Iran identifies and trains its cybersecurity talents, it is important to look at a particularly effective recruitment method: CTF competitions (or Capture The Flag). These events, popular worldwide, including in France, consist of technical challenges where participants must solve complex cybersecurity puzzles. Beyond their playful and competitive nature, these competitions play a crucial role: they allow for the detection of the most promising profiles while evaluating their skills under almost real conditions.
This practice is not recent. As early as 2014, a Cyber Threat Intelligence report published by HP already highlighted the importance the Iranian regime places on gamifying hacking as a preferred recruitment method. This approach skillfully combines learning, hands-on practice, and competitive spirit, thereby facilitating the training of future cyber experts capable of serving the regime’s strategic interests.
In 2024, Ravin Academy organized two major CTF competitions. The first event, called Ravin CTF, took place between February and March 2024. This competition, open to a wide audience, aimed to detect and recruit talent from a diverse pool of participants. The official poster attests to the scale of this operation. The second event, Olympics CTF, also open to the public, was held in October 2024, further strengthening the strategy to identify and train the best candidates.
The investigation also brought to light the role of an entity called ASIS. This group regularly organizes high-level competitions. ASIS maintains close ties with the Iranian cyber ecosystem.
These CTF competitions therefore form an essential link in Iran’s cyber strategy, combining recruitment, training, and loyalty-building in a competitive setting, while masking their true objectives behind the facade of a simple technical exercise.
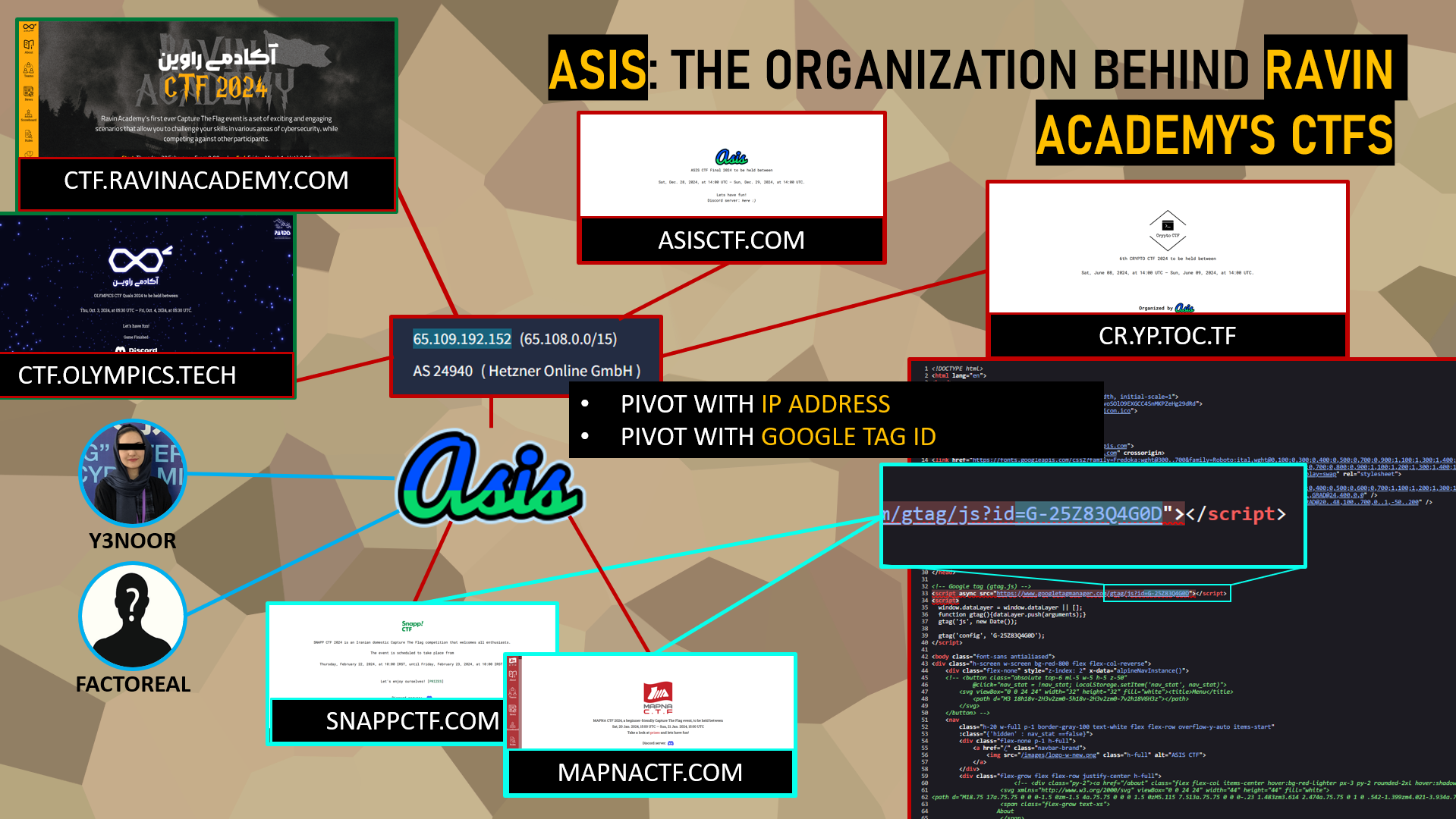
ASIS: The Organization Behind Ravin Academy’s CTFs
By analyzing in more detail the two CTF competitions organized by Ravin Academy, a first striking technical observation emerges: their domain names share the same IP address, hosted by Hetzner, a German provider. This hosting choice already illustrates a certain level of circumvention of Western sanctions, as it allows these Iranian cyber events to maintain Western hosting despite restrictions.
On this same IP address, we also identified several other domain names linked to CTF competitions, such as AsisCTF or CryptoCTF. By exploiting a pivoting technique based on the Google Tag Manager IDs present on these platforms, it is possible to pivot to other servers and discover additional competitions, all related to the same entity.
Using this method, our investigation revealed the existence of CTFs conducted for major Iranian industrial and commercial entities, such as Snapp!, the main ride-hailing platform in Iran, as well as MAPNA, a key player in the Iranian industry. All these CTF events are designed and managed by the same organization: ASIS.
Furthering our investigation into ASIS, we identified the pseudonyms of its two co-founders: Y3noor and Factoreal. Pushing our research even further, their real identities were also discovered, but we have chosen not to disclose this information as it goes beyond the scope of this inquiry.
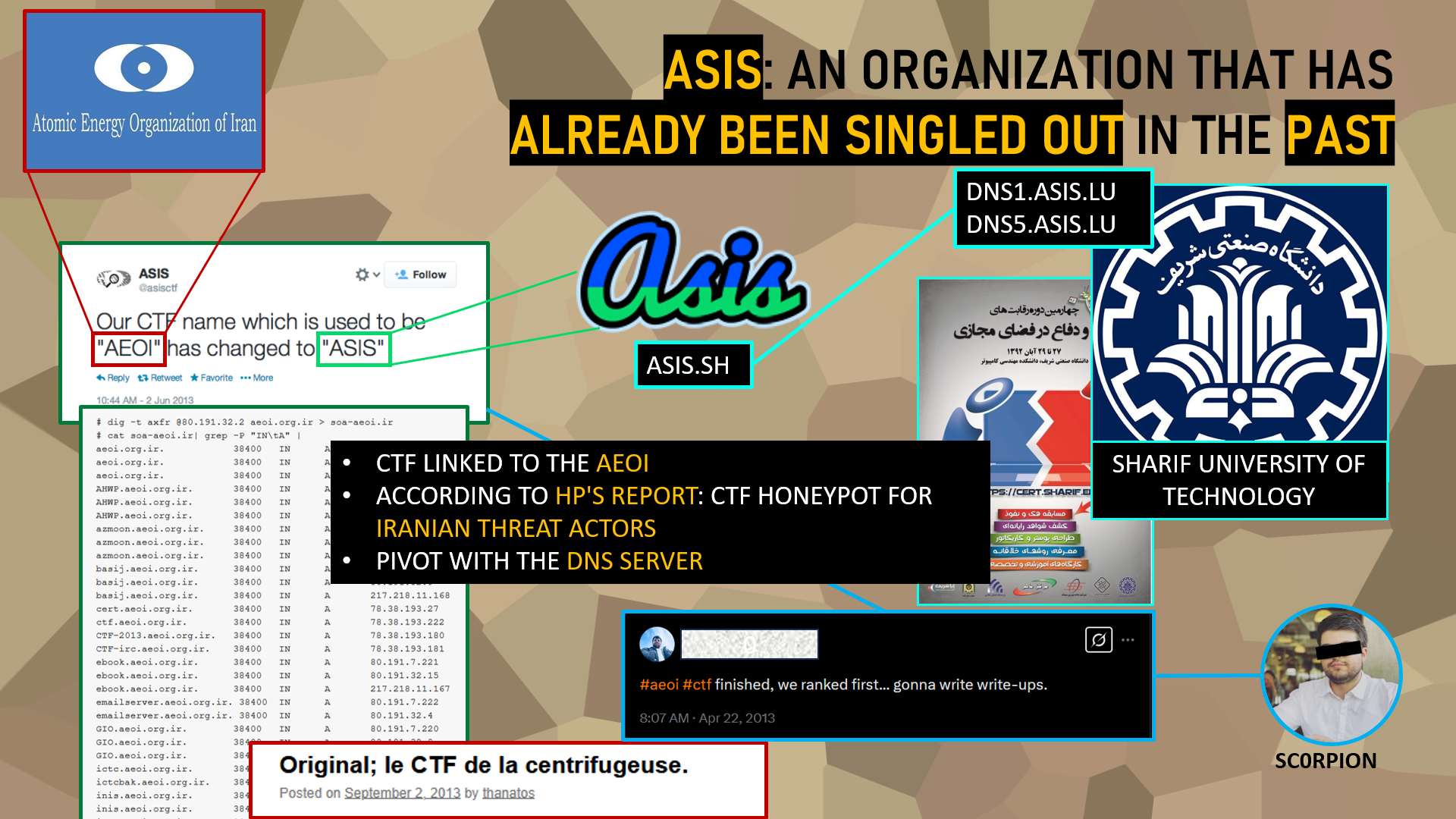
ASIS: An Organization Previously Exposed
ASIS is not a new entity in the Iranian cyber landscape. It has already been identified in CTI reports for several years, notably in the 2014 report published by HP. This report revealed that ASIS was initially a CTF directly linked to the AEOI (Atomic Energy Organization of Iran), the Iranian nuclear agency responsible for the country’s nuclear program.
Over time, ASIS repositioned itself: it changed its name and expanded its scope to become an organization specialized in designing and organizing CTF competitions, while officially distancing itself from its nuclear-linked past. However, its roots remain marked by close ties to sensitive Iranian infrastructure. In 2013, a French internet user under the pseudonym Thanatos had already spotted the presence of the ASIS CTF on an IP address range belonging to the AEOI. This fact takes on particular significance when recalling that one year earlier, the Natanz nuclear plant, run by the AEOI, had been heavily targeted by the Stuxnet malware, a major cyberattack attributed to Israeli and American intelligence services.
The 2014 HP CTI report also mentions that, in its initial phase, the ASIS CTF operated as a honeypot designed to attract and analyze Iranian threat actors, allowing the AEOI to monitor and map emerging talents and techniques. In this context, some already known names reappear, such as Yashar S. (previously mentioned), who had won this first CTF under the pseudonym Sc0rpion.
Another interesting element is that, by examining ASIS’s technical infrastructure via DNS archiving tools, it appears that the servers for the official website, asis.sh, are hosted on IP addresses belonging to Sharif University of Technology, one of Iran’s academic institutions. This technical detail suggests a strong link between ASIS and this university.
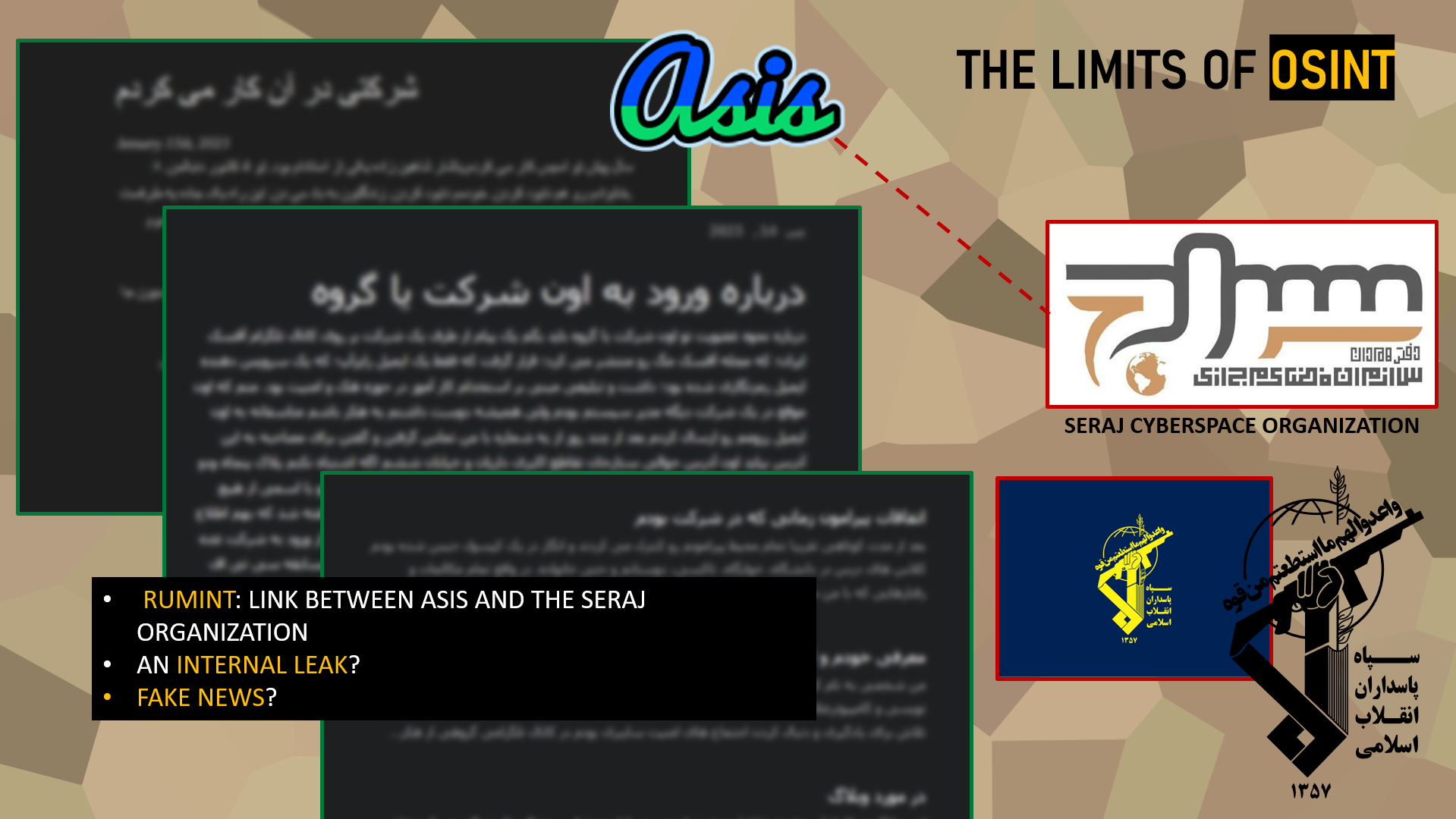
Limitations of OSINT
During our investigation into ASIS, we came across several documents from a data leak allegedly disclosed by a former collaborator of the organization. These documents claim that ASIS is closely linked to another Iranian entity operating in cyberspace: the Seraj Cyberspace Organization. This organization is known to be under the direct control of the paramilitary Basij forces, which themselves are attached to the powerful Islamic Revolutionary Guard Corps (IRGC).
Seraj is often described within intelligence circles as a major player in Iranian information warfare, combining cyber influence, psychological operations, and large-scale digital propaganda.
However, despite these allegations, an in-depth OSINT analysis did not allow us to independently confirm the veracity of the information contained in this leak. The weak correlation with other reliable sources and the absence of tangible evidence prevent us from validating these revelations today. It is also possible that this is a disinformation operation designed to confuse and mislead.
Aware of the stakes and risks associated with disseminating unverified information, we have therefore chosen not to dwell further on this lead, preferring to focus on corroborated and documented elements to ensure the rigor of our investigation.
Iran's dual approach: Cyber and PSYOPS
We have just explored in detail the cyber-offensive dimension of Iran’s cyber capabilities. However, it is crucial to understand that Tehran’s strategy goes far beyond simple conventional cyber operations. Indeed, Iran has developed what can be described as a “dual” approach, skillfully combining offensive cyberattacks with sophisticated psychological operations.
Several state agencies, foreign intelligence services, and cybersecurity firms have formally accused Iran of conducting coordinated campaigns blending influence, disinformation, and manipulation of public opinion.
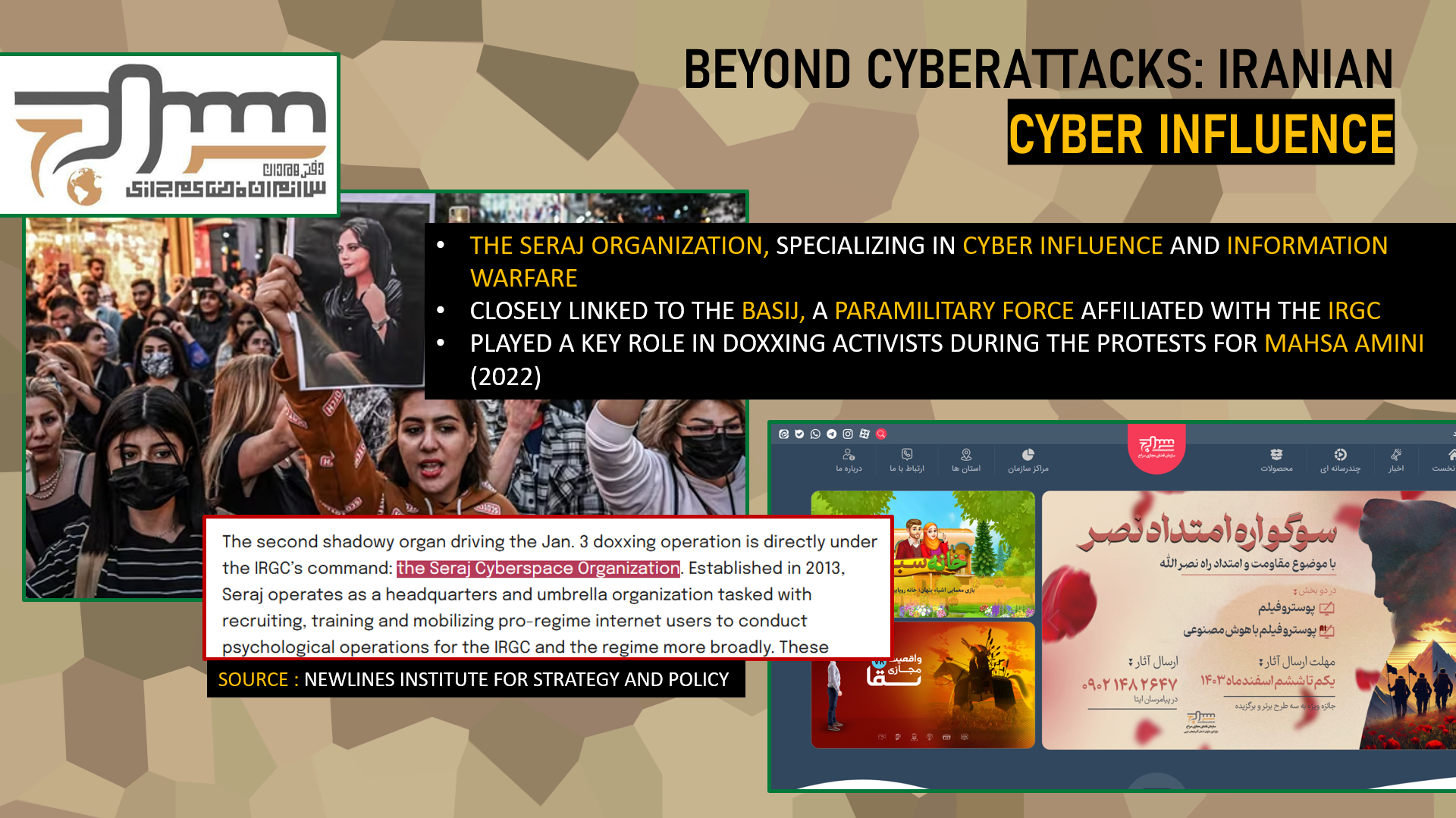
At the heart of this psychological warfare apparatus is the Seraj Organization, specialized in information warfare and digital influence operations. Created in 2013, Seraj acts as an umbrella structure, recruiting, training, and mobilizing pro-regime internet users to carry out manipulation and propaganda actions in service of the Iranian state’s interests. What particularly distinguishes this organization is its direct link to the Basij, a paramilitary force closely connected to the Islamic Revolutionary Guard Corps (IRGC).
This alliance took a particularly worrying turn during the protests following the death of Mahsa Amini in 2022. According to an article from News Line, the journal of the Newlines Institute for Strategy and Policy, Seraj played a central role in the doxxing of protesters and activists. The organization collected and then disseminated personal data enabling Iranian security forces and the Basij to identify and target demonstrators. In the context of the conflict with Israel, the paramilitary Basij forces have intensified their repression in Iran. Increasing patrols and checkpoints, they exert systematic violence against the civilian population. Their actions are characterized by mass arrests, movement restrictions, and summary executions, particularly targeting ethnic minorities. Recent civilian killings, such as those of Reza Hamidavi and Azad Ranaei, reveal the brutality with which the Basij suppress any potential opposition or collaboration.
But Seraj’s activities are not limited to repression. The organization also produces a wide range of propaganda content: patriotic video games, ideologically charged films, as well as cybersecurity awareness courses accessible to the general public. These trainings include specific guidelines on the so-called “appropriate” way to express oneself online, in line with the values promoted by the regime.
Despite its central role in the Iranian cyber-influence ecosystem, the Seraj remains relatively unknown to Western analysts, giving it a significant operational advantage.