OSINT in the analysis of armed conflicts: The Russian military presence in Belarus

Since April 2022, joint military exercises between Russia and Belarus have been underway, but their duration has been steadily increasing. In this article, we will explore the application of OSINT in the analysis of the Russian military presence in Belarus. We will focus on two key aspects: the transport of weapons between Russia and the various training zones, and the information left online by Russian soldiers present in these zones.
The joint military exercises between Russia and Belarus were announced to be temporary, but despite multiple promises to complete them, their end has been repeatedly postponed. According to the Project Hajun, an initiative of Belarusian journalist Anton Motolko, who is close to the opposition, the total duration of these exercises has been extended by 49 weeks so far, at the time of writing. When we began our OSINT analysis of this case, the exercises were scheduled to end in January. They are still ongoing.
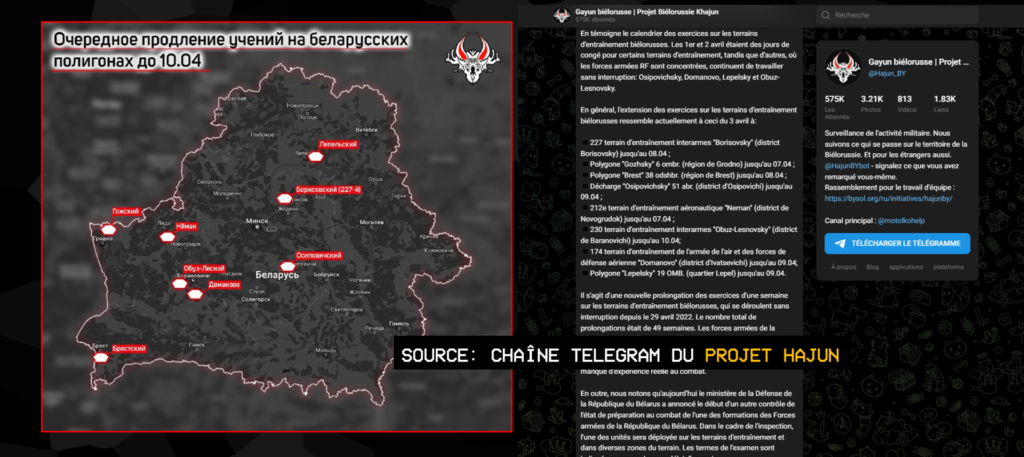
We will present several techniques for gathering relevant information on these military training courses. As previously announced, we have approached the case from two angles. Firstly, we will deal with the transport of weapons between Russia and the training areas, and secondly, we will look at the profiles of the Russian soldiers identified in these training areas.
Tracking down Russian arms convoys in Belarus
In a sensitive geopolitical context, gathering accurate and reliable information is essential to understanding the issues and conflicts at stake. With this in mind, we carried out an in-depth OSINT analysis of the transport of weapons by train between Russia and training zones in Belarus.
Our work began with the creation of an interactive map which enabled us to locate the various videos and information relating to the transport of weapons by train. OSINT applied to geopolitics is first and foremost a community effort. We collected this data from various communities and actors in the OSINT sphere, including Geoconfirmed, Centre for Information Resilience, with their initiative Eyes On Russia, and Project Hajun.
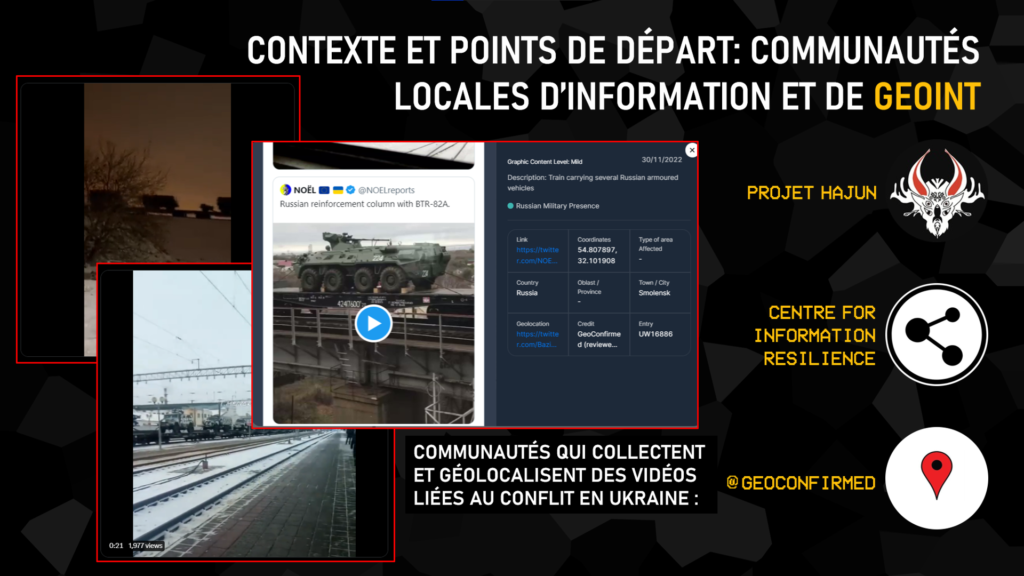
The authenticity and reliability of these data were verified before being integrated into our map. This interactive map enabled us to clearly visualize the areas where the transport of weapons was observed, and to follow their trajectory.
In addition to this data, we carried out extensive searches on social networks for other non-geotagged videos. Using various GEOINT techniques, we were able to position them precisely on our interactive map.

On this map, areas of joint military training are shown in dark blue, while geolocated Russian military trains are marked in red. This visualization highlights the areas where military exercises are taking place, as well as the routes taken by trains transporting weapons and military equipment to these areas. This cartographic representation is an essential tool for better visualizing the movements of Russian armed forces in Belarus.
Widely used in the context of the war in Ukraine, by Internet users and military forces alike, the exploitation of geospatial intelligence (GEOINT) or imagery intelligence (IMINT) can yield a wealth of information. In the months preceding the start of the invasion, numerous images on social networks showed convoys of vehicles or trains heading for the Ukrainian border, while satellite images also showed a pile-up of military equipment in Russian bases close to the border, the forerunner of the invasion to come. Even today, the movement of equipment is widely reported on social networks, particularly in Belarus. We have chosen two videos to illustrate different ways of geolocating a train carrying Russian equipment.
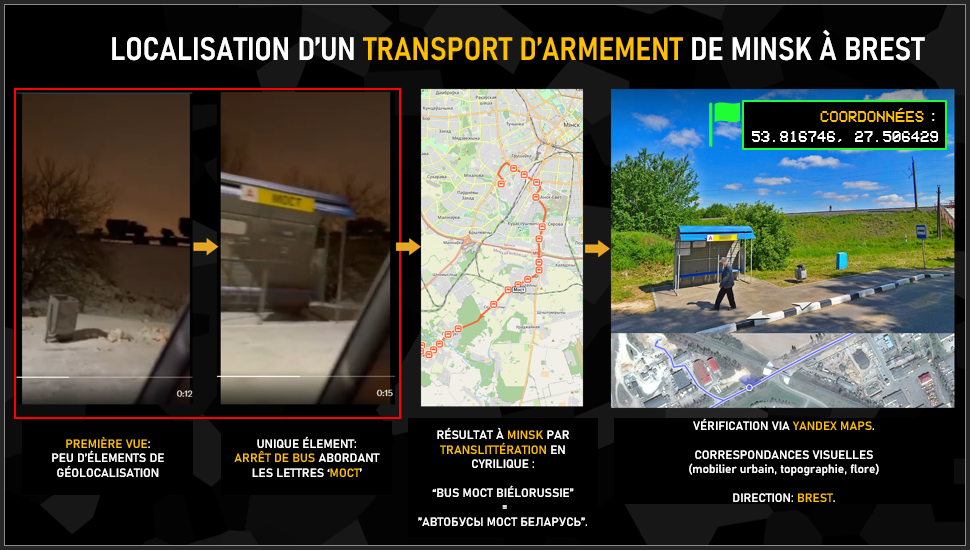
First of all, the video description indicates that the train is travelling from Minsk to Brest, in the west of the country. At first glance, this video seems difficult to use, given its framing and lighting conditions. The only clue is the briefly visible name of the bus stop. This is where the video’s context comes into play, as the letters MOCT designate a multitude of things in Russian-speaking countries, Hence the importance of associating the words “bus” and ” Belarus” and then carefully analyzing the concordance of the search results and not going for the first thing that comes up. After several links, we come across a bus route corresponding to our search, with a stop of the name we’re looking for, close to a railroad. We then go on to the confirmation phase with Yandex to verify the visual location.
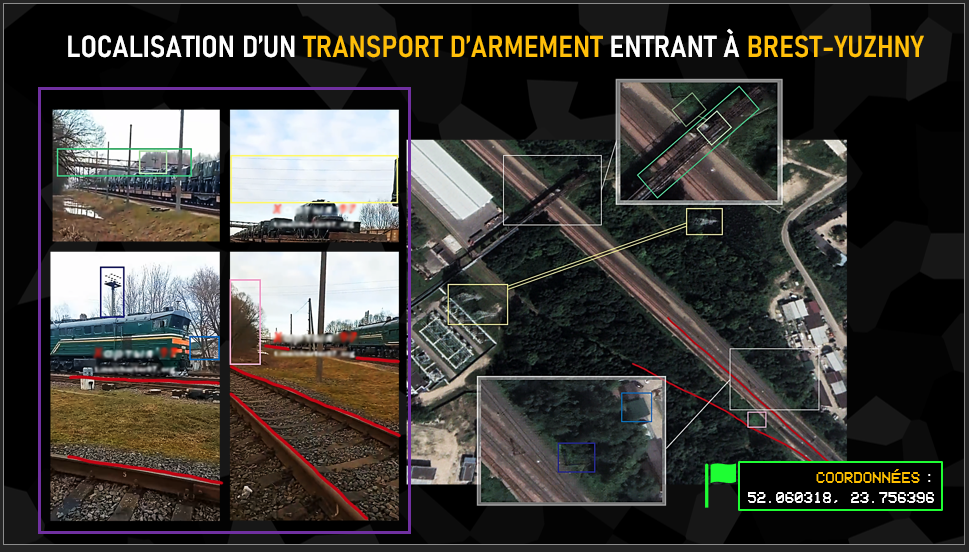
In this case, the video description indicates the name of a station, Brest-Yuzhny. The goal here is to verify a piece of information you already have, in the same way as for determining an unknown location, by taking sufficiently distinctive landmarks from the video to find and compare their positions on satellite imagery, Street View or a photo. In this example, which was actually quite simple since the elements were numerous (sometimes limited to a simple corner of a wall or a few trees), we can see the variety of identifiable elements: a bridge, a tower, power lines, a roof, vegetation or even the direction of the rails, all of which effectively confirm the video’s location.
The analysis of the map reveals the presence of four main routes between Russia and the training areas used to transport armaments. Among these axes, we can clearly identify the city of Smolensk in Russia as a key point for these shipments to training areas in Belarus.
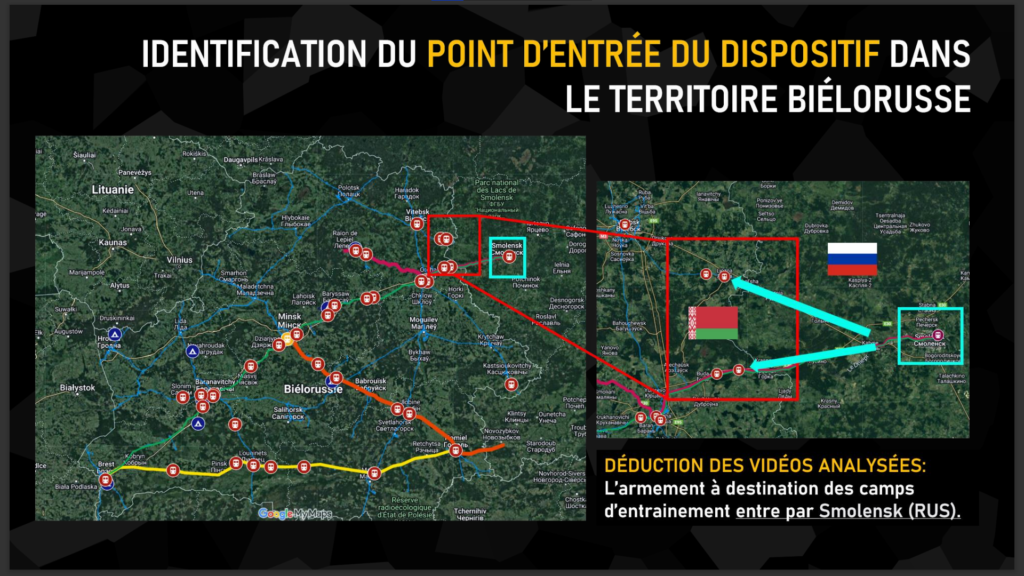
Two railway lines depart from Smolensk and are used to transport weapons to Belarus. These lines play an important role in the logistical movement of military equipment between the two countries.
This observation confirms the importance of Smolensk in the deployment of Russia’s military presence in Belarus. By understanding these transport routes, we can gain a better understanding of the logistical flows and routes taken by Russian military convoys.
It should be stressed that the identification of these axes as key points is based on the analysis of available data, and can be supplemented by other sources of information. However, this geographical information sheds important light on the routes used for transporting weapons between Russia and Belarus, thus reinforcing our understanding of the Russian military presence in the region.
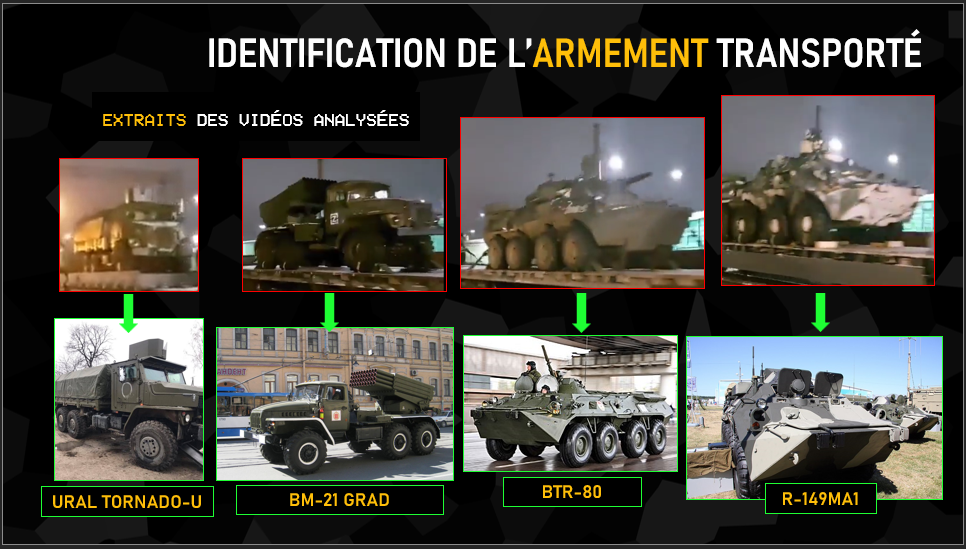
Beyond geolocation, the other information that can be exploited on these videos of equipment convoys is precisely to identify what equipment is being transported. In this video, we can see a Ural Tornado-U armored transport vehicle in its version with a weapon station on the roof, a BM-21 Grad launcher, a BTR-type troop transport and finally an R-149MA1 armored command vehicle, recognizable here by its shape and camouflage. Identifying the equipment being transported can also give an indication of the “state of health” of the armaments involved, with videos of T-54 and T-55 tanks, built in the 1940s-1950s, being transported to Ukraine in March, a sign of the lack of more modern equipment available. Of course, identifying and distinguishing these military vehicles, with all their variants, requires either a great deal of time or solid military knowledge. Twitter accounts such as “Ukraine Weapon Tracker” and “Oryx“, which list all the land, sea and air equipment destroyed or captured on both sides, have specialized in this area.
Using other tools, we were also able to detect activity within these training camps. One such tool is NASA’s Global Fire Map, which uses satellite data to map forest fires around the world.
The Global Fire Map is a very useful tool for detecting activity in military training areas. Indeed, this NASA tool can detect active fires and thermal anomalies, which can be used to spot missile launches, heavy artillery fighting and explosions. Although this tool was originally developed to track forest fires, it is increasingly being used to track activity in conflict zones.
We noticed that some military training areas were showing fire activity, probably due to shell explosions during training, indicating the presence of soldiers in training on the ground. This observation strengthened our analysis and gave us a better understanding of the activities taking place in these training areas.
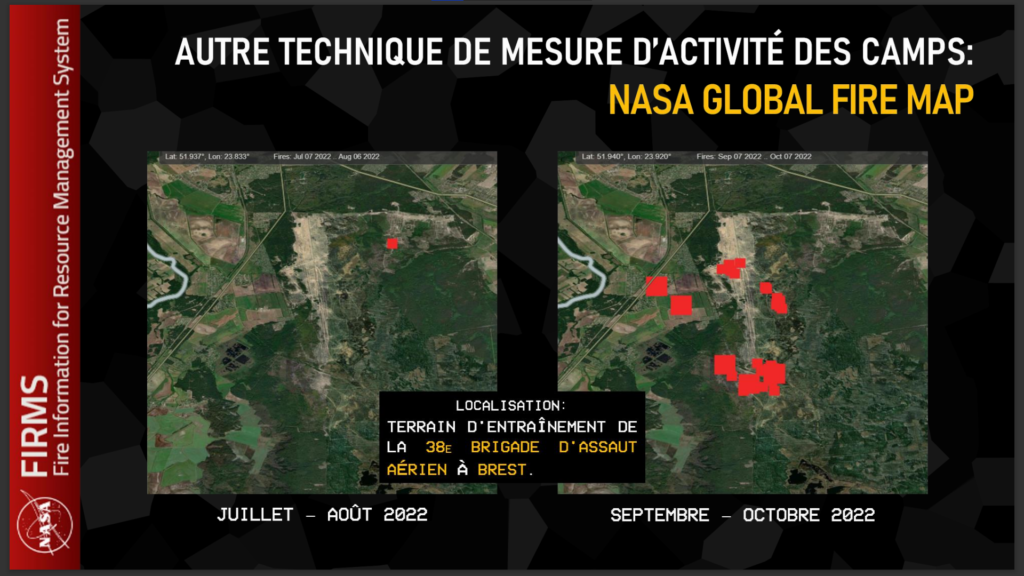
For example, by analyzing data from the Global Fire Map, we observed high activity in the Brest training camp between September and October 2022. The information gathered suggests an increase in military activity in this area.
In contrast, during July and August 2022, we detected lower activity in the Brest training camp. This could indicate a temporary pause in exercises or a reduction in the intensity of military operations during this period.
Russian soldier profiles in Belarus
For the remainder of our demonstration, we have recalibrated our analysis from the global and strategic level, to the individual level, by tracking down Russian soldiers in Belarus and exploiting their online data.
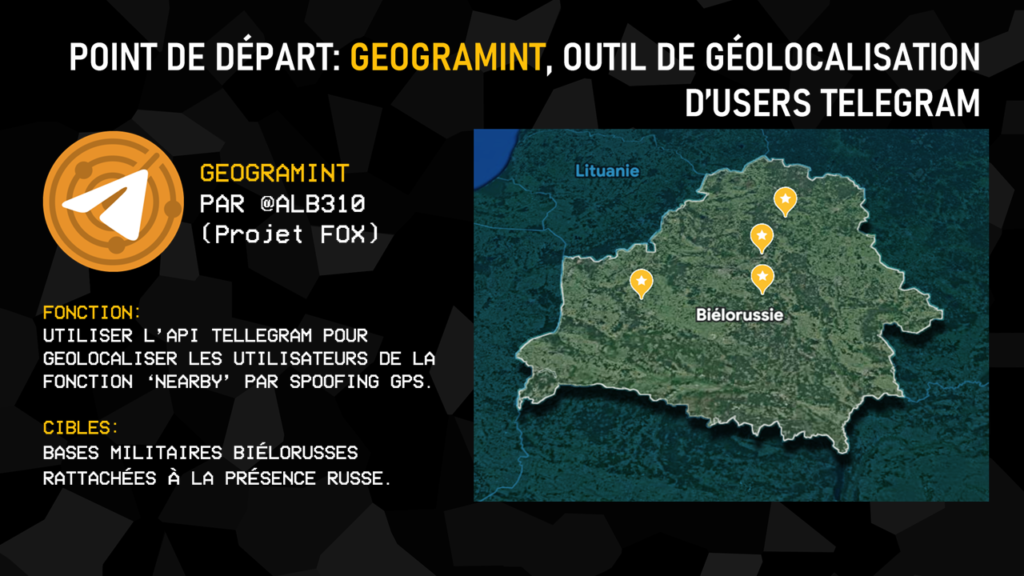
Our starting point in this second part of our investigation was a home-made tool, Geogramint, developed by our co-founder Alb310. This tool exploits Telegram’s API and more specifically its Nearby function, which in normal circumstances enables the discovery of all users of this function, present in predefined perimeters around oneself (500m, 1,000m, 2,000m, …).
Geogramint usurps the GPS coordinates entered by its user, and enables these profiles to be listed in real time from any point in the world.
The feature is very popular in Russian-speaking countries, as it can be used to contact drug dealers and prostitutes, among others, and has proved particularly useful in Belarus.

Thanks to our study of the Russian logistics network, we were able to identify four Belarusian military bases used by Moscow’s men. We entered the GPS coordinates on Geogramint, extracted all the user profiles identified, and isolated all those with a military connotation, grouped together in the slide above.
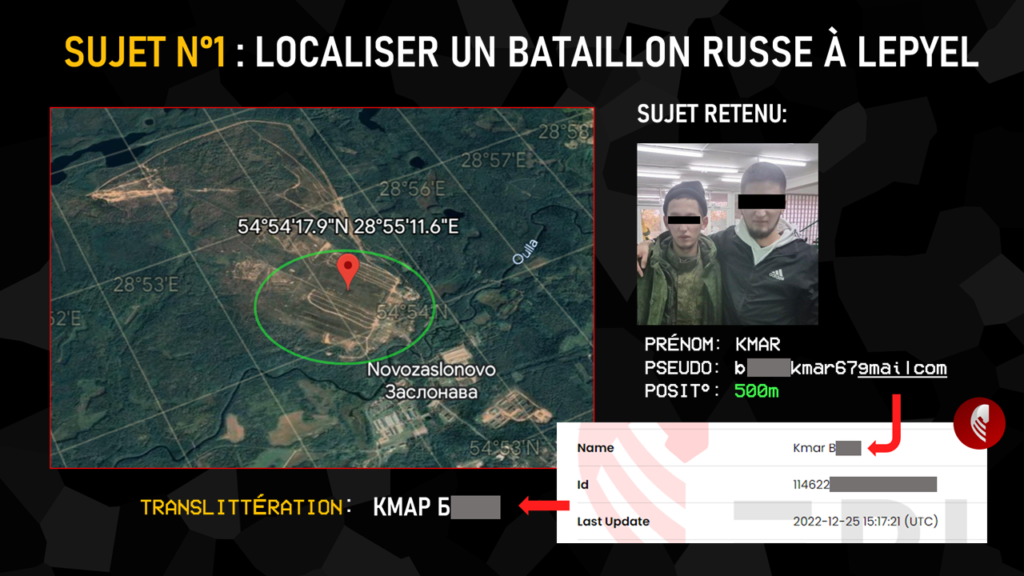
The individual shown above was spotted within 500m of the Lepyel base, where he was active the night before our presentation at the International Cybersecurity Forum. The extracted data yielded a photo of two men, one in fatigues, a first name and a pseudonym betraying the exact composition of a gmail address. This e-mail address was run through Epieos to obtain a full name in Latin characters, which we transliterated into Cyrillic characters for further research.
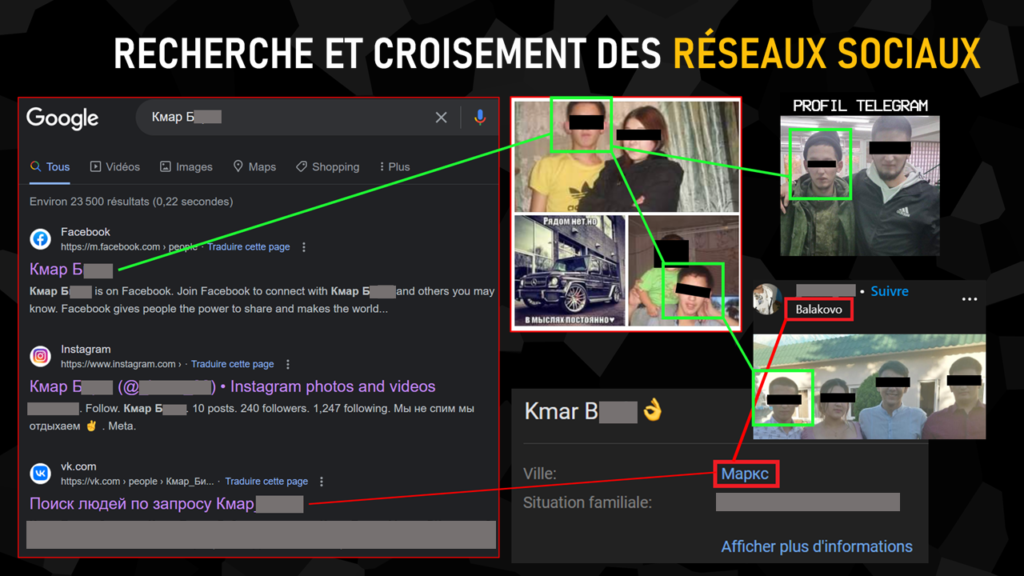
Searching for this name in Cyrillic characters on Google, without any particular tag, the first results have already identified three social networks in his name. We were able to confirm the link between each of them and our Telegram user by various means: notably by facial identification and similarity of location (neighboring towns).

Confident of the relevance of our results, we took a closer look at the target’s social networks. His brother’s Instagram profile shows him and our subject posing in fatigues in a celebratory mood, each in front of the emblem of a different Russian army corps (air defense forces for the brother, railway troops for our subject).
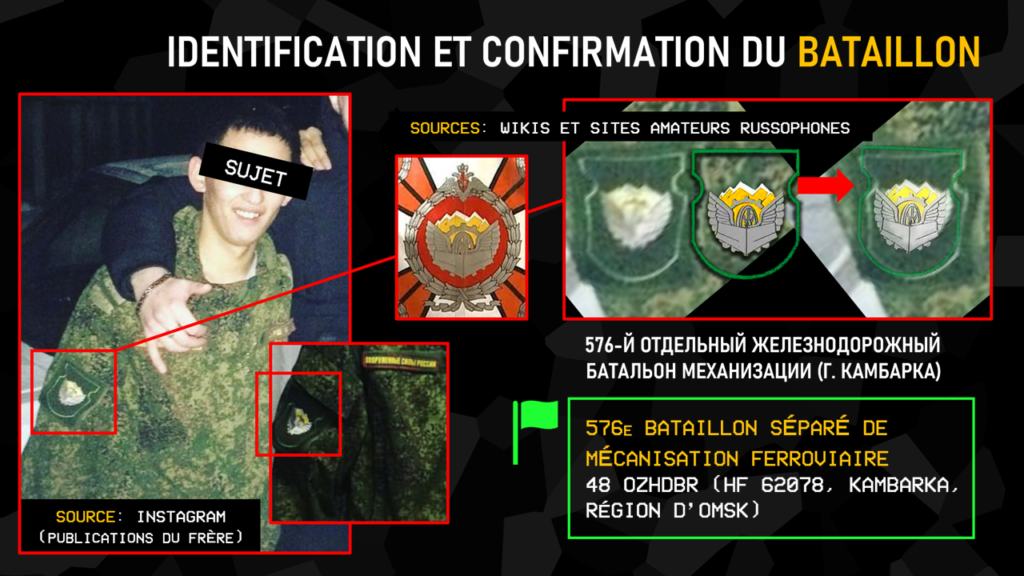
Armed with this information, and studying other photos published by the brother in which our subject appears, we found a very low-definition coat of arms on the latter’s latticework. We then set out on the Russian Internet in search of amateur sites listing the various regiments and battalions and their emblems, concentrating on railway troops. On this website, we come to the conclusion that the 576th Separate Railway Mechanization Battalion was stationed that night at Lepyel in Belarus.
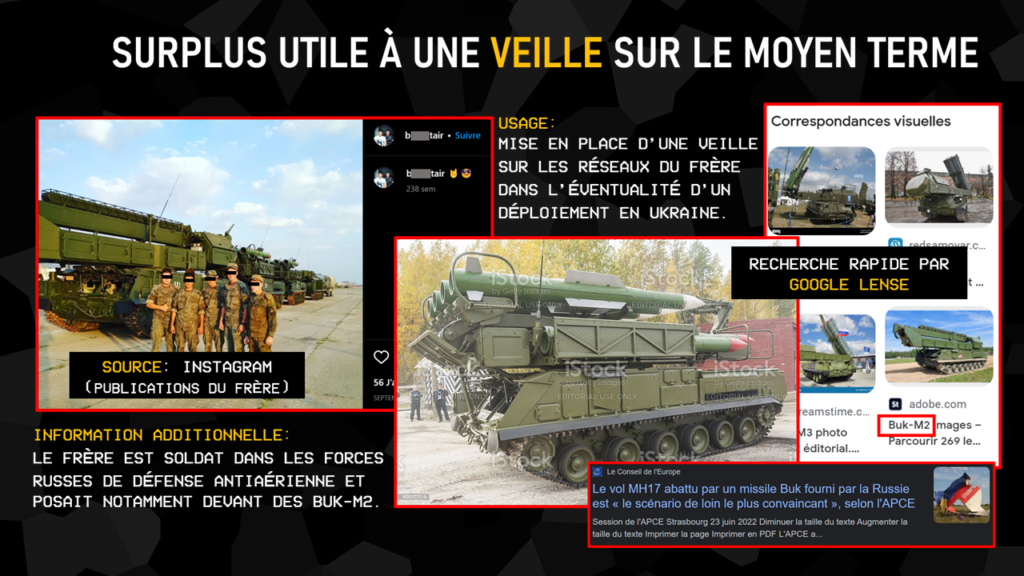
As a side note, we also point out that the brother posed in front of Buk-M2 systems and could legitimately handle them as part of his service with the air defense forces. A watch on this type of individual could enable faster investigations into incidents such as that of flight MH17, shot down by one of these missiles in 2014.
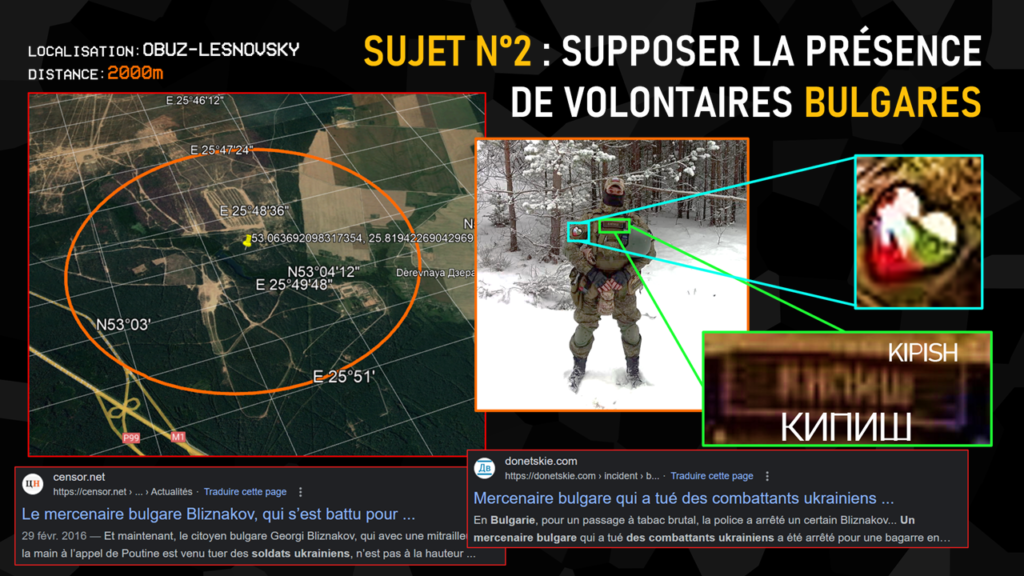
The second subject we chose for our presentation was a man located in the 2000m around the Belarusian base of Obuz-Lesnovsky, again on the night before the FIC. The idea of this second demonstration was simply to expose the amount of information that can be extracted from a low-resolution profile photo: on the one hand, a coat of arms featuring the Bulgarian flag and the Russian flag within a heart, assuming the man’s origin, and on the other, the name Kipish appearing in Cyrillic on his torso, later confirmed in his Telegram pseudonym.

The last subject selected was a profile featuring two men in fatigues, this time wearing Belarusian camouflage, and identified within a 2000m radius of the Lepyel base. A search for the name extracted by Geogramint, this time transliterated from Cyrillic to Latin, revealed an Instagram profile. With no obvious connection, we had to carry out an in-depth analysis of the two men’s facial features to compare them with those of the Instagram user. As is often the case in this type of situation, it was the shape of the ear – a distinctive one at that – that confirmed that the same person was behind both accounts.
Analysis of his following on social media led to the identification of a whole series of other military profiles, one of which was clearly a ranking officer. Another of these profiles even crudely proceeded to publish his military documents, further analysis of which would in turn identify the Belarusian regiment stationed here.
Concluding words
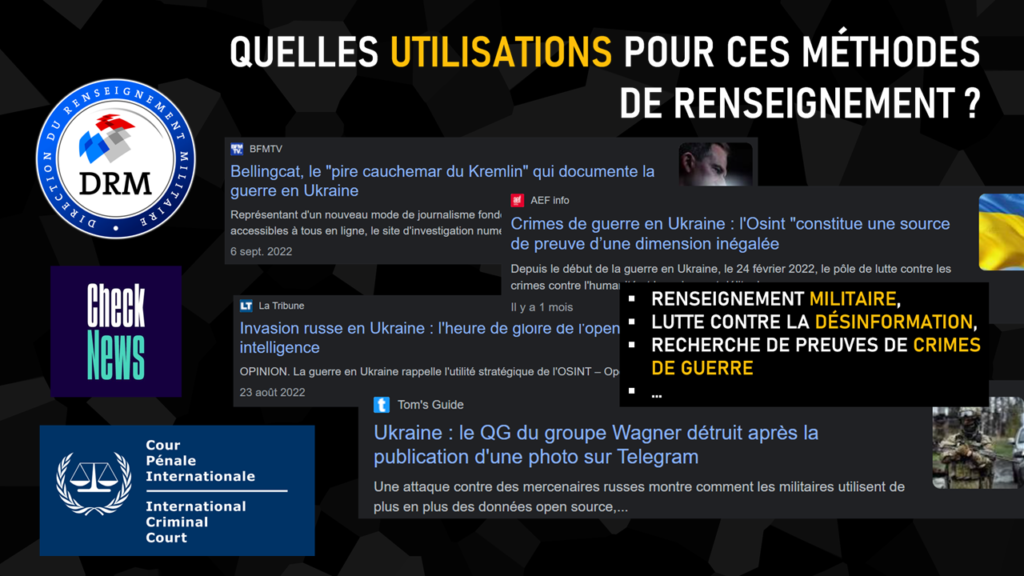
This is the conclusion of our demonstration, representative of the interests that OSINT can serve in times of war or crisis, targeting both the global and individual levels. The results obtained naturally lead us to associate these techniques with military intelligence, but they can also prove – and are already proving – to be profoundly decisive in the fight against disinformation or in the search for evidence of war crimes.
For the founders of the Projet FOX, this presentation, made for the first time to the FIC audience, is also the culmination of three years of applying open-source intelligence techniques to crises and conflicts across the globe.