Tracking down the cybercriminal infrastructure of infostealer RisePro

During the course of a technology watch, IP addresses associated with the RisePro infostealer came up. Investigations using OSINT techniques enabled deeper research and uncovered a large part of the cybercriminal infrastructure linked to this malware, as well as its connections with a PPI (Pay Per Installation) service: EasyLead.
This article will present different methods for identifying cybercriminal infrastructure using OSINT. First, we’ll look at the presence of RisePro on Telegram, particularly since December 2022 when SEKOIA.IO published its CTI report on RisePro (which I highly recommend checking out!). Next, we’ll look at RisePro’s presence on hacking forums. After that, it will be interesting to look at the methods and tools used to track down the RisePro infrastructure. Next, we’ll take a detailed look at PPI provider EasyLead and its links with RisePro. Finally, we will attempt to make contact with various actors.
What is an infostealer?
An infostealer is a type of Trojan designed to collect information from a system. The most common form of infostealer collects login information, such as usernames and passwords, which it transmits to another system over the network or by other means. Other common types of infostealer, such as keyloggers, are designed to capture user input, revealing sensitive information.
The consequences of the presence of an infostealer can be serious, leading to identity theft, financial loss, privacy breaches and other risks to the security of personal and business data.
What is a C2?
Command and control (C2) servers are tools used by threat actors to orchestrate and manage cyber attacks by transmitting instructions to their malware, disseminating malicious programs and scripts, among other things. They also act as receivers for data collected from targeted servers, devices, websites and forms. In a way, C2s act as nerve centres for the malicious operations carried out by these individuals.
These C2 systems facilitate communication between the attacker and the target, whether to direct a network of compromised machines or to transfer stolen data to its final destination. Targets can vary from a single device to hundreds within a single system, or even millions.
Establishing and maintaining a connection with a C2 is a crucial step for threat actors, as without this link they would only be able to carry out part of their malicious activities. Attackers need to be able to transmit commands to exert control over the outcome of their actions.
Command and control servers often exploit unmonitored and unreliable communication channels, such as DNS, to transmit instructions to infected systems. Today, these servers are often short-lived, frequently residing in reputable cloud services and using automatic domain generation algorithms to complicate their detection by authorities and cybersecurity researchers.
RisePro
RisePro is a fearsome infostealer that spreads mainly via downloaders, notably PrivateLoader. Once infiltrated into a system, this malware is capable of stealing sensitive data such as credit card details, passwords and personal details, creating serious security risks for users.
This infostealer shares similarities with another malware called Vidar. Like the latter, RisePro collects and extracts sensitive data in the form of logs, operating in the C++ programming language.
The actors behind RisePro have been spotted distributing it via a malware downloader called PrivateLoader. They market their malicious services on the Telegram messaging platform.
CrowdStrike, in its investigations, is tracking the operator of RisePro under the name “HERMIT SPIDER”. This entity is described as the brains behind both the pay-per-installation (PPI) service PrivateLoader and the infostealer RisePro. Active since at least May 2021, this player first developed and operated the PrivateLoader downloader as a PPI service. HERMIT SPIDER usually uses another PPI service to distribute PrivateLoader, but has set up its own loader to disseminate RisePro, thus consolidating its malicious activities.
In December 2022, the French company SEKOIA.IO produced a detailed CTI report on RisePro, highlighting its connections with PrivateLoader.
RisePro's presence & activity on Telegram
It appears that RisePro’s presence on Telegram is quite extensive, with several accounts and channels being used for various malware-related activities.
The “RISEPROSUPPORT STEALER” channel (https://t[.]me/RisePROstealers) stands out for its high number of followers, over 2,300, and is active just a few months after its creation on 1 February 2023. This channel provides regular updates on the development of RisePro, and was last active on 15 November.
A look at other channels such as “RisePRO” (https://t[.]me/RisePROstealer) and “RisePro | News” (https://t[.]me/risestealer), created in July 2023, reveals different patterns of activity. “RisePRO” stopped publishing in August 2023, while “RisePro | News” is active with regular publications on the development of the malware, most recently on 21 November.
According to the SEKOIA.IO report, the Telegram account used by the developer to sell RisePro was @RiseProSUPPORT (https://t[.]me/RiseProSUPPORT). However, the biography for this account now lists the “RisePro | News” channel as the main channel for RisePro, while @RiseProSUPPORT is listed as the post-purchase support account. In addition, references to the @RiseProSUPPORT account are also made in posts in the “RisePRO” channel. This suggests that both channels, “RisePRO” and “RisePro | News”, as well as the @RiseProSUPPORT account, most likely belong to the infostealer operator.
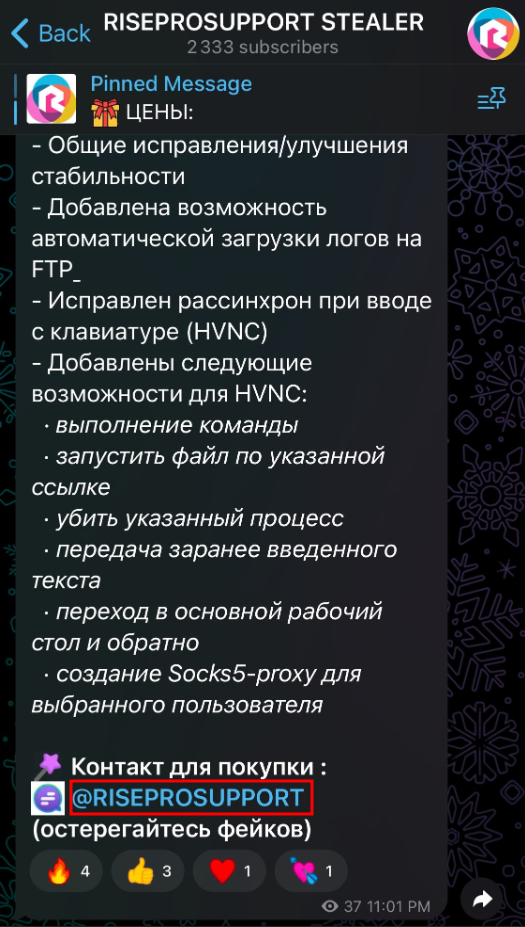
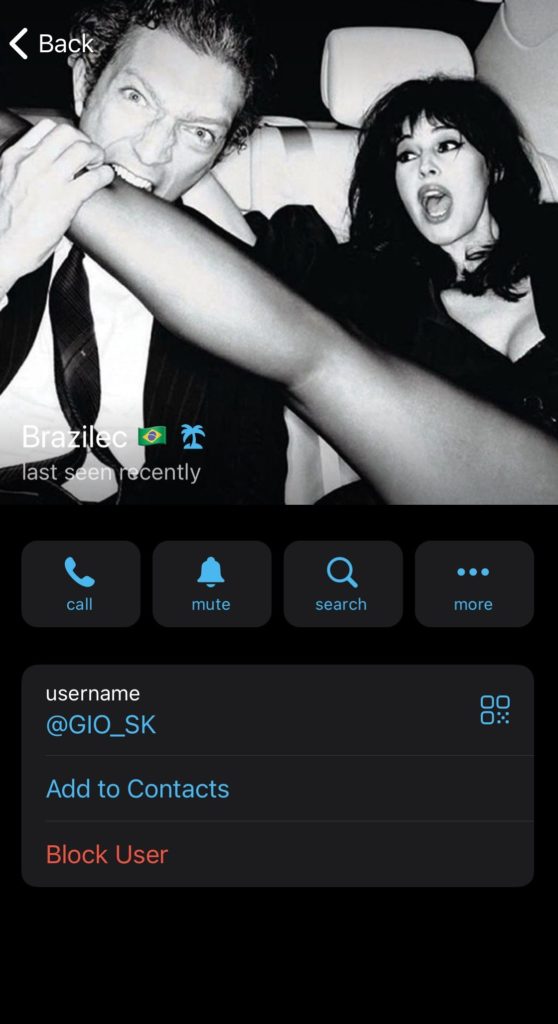
As for the “RISEPROSUPPORT STEALER” channel, despite its large follower base, it directs users to the @GIO_SK account (https://t[.]me/GIO_SK) for any purchases or support. This redirection appears to be a scam designed to trick users interested in the malware.
There is also a final account, “Rise Pro” (https://t[.]me/RisePro), followed by only around sixty people, but which often refers to PrivateLoader in its posts. In one of its posts, this account shows a video of the supposed ‘C2’ interface. However, this interface does not match the screenshots shared by the other accounts/channels attributed to the RisePro operator. So this too appears to be a scam, especially as this account is charging $250 for lifetime access to a C2 that doesn’t match RisePro’s.
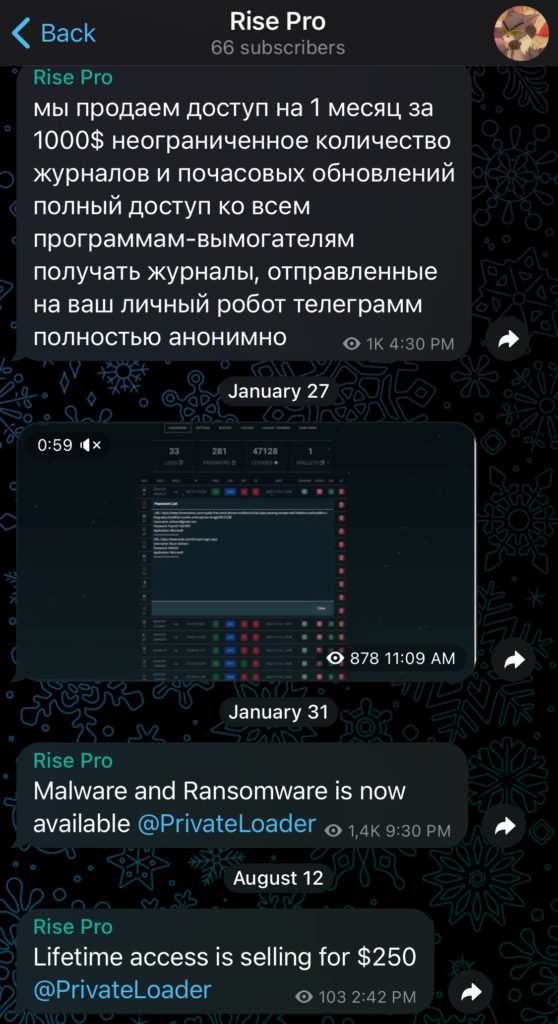
After carrying out a reverse image search, it turns out that the video on the “Rise Pro” channel actually corresponds to the interface of another infostealer: Aurora.
#Malware #Aurora Misconfigured Aurora C2 🙄
— 0xperator (@0xperator) April 11, 2023
hxxp://37.220.87.8/
1523 Logs
98630 Password
2613728 Cookies
79 Wallets
Loader: hxxp://94.130.59.91:8000/reports/MSCLIB.exehttps://t.co/4XCLpPjb5C
cc/ @Gi7w0rm pic.twitter.com/80Ld3s2oqo
Back to RisePro. The operator of this malicious software uses Telegram to disseminate information about updates to its code, to market its product and also to provide after-sales support for users.
Since the creation of the Telegram channel in July 2023, RisePro has undergone 12 code updates. The software has evolved from version 0.2 to version 1.1, released on 23 November. These updates have brought several notable improvements:
- Improved infostealer functionality
- Automation of the payment process for using the malware via a Telegram bot
- Support for different foreign encodings
- Addition of a proxy for client-server communication
- Development of a C# version of the malware
- Support for many new programs such as Outlook, TotalCommander, Skype, Element, Signal, Tox, OpenVPN, etc.
- Addition of a “Hidden Virtual Network Computing” feature
- Integration of a SOCKS5 proxy for users
- Addition of a button to reset all collected logs
- Added Telegram notifications based on collected logs
These changes demonstrate the active and constant development of the malware, highlighting the commitment of RisePro’s operators to improving and extending its functionality.
RisePro on Hacking Forums
In one of the posts on Telegram, the RisePro operator announced that it had shared information about the malware on 4 specific forums:
- XSS
- BHF
- HackForum
- WWHClub
I was able to access two of these forums and observe RisePro-related activity there.
WWHClub
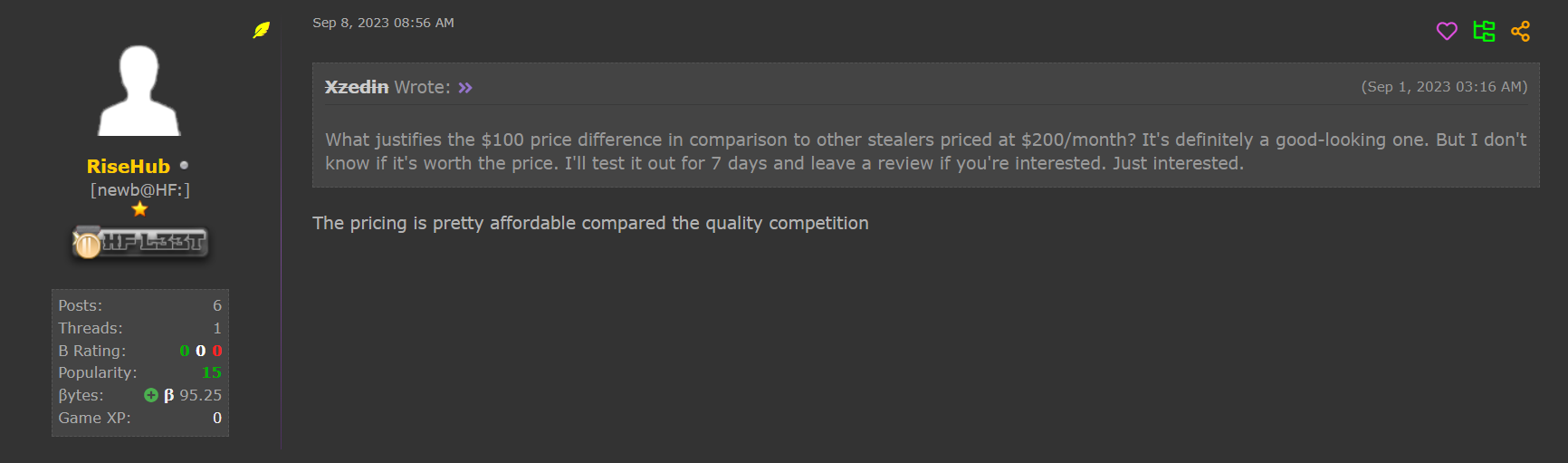
On WWHClub, as well as on other forums, the RisePro operator uses the pseudonym ‘RiseHub’. There is a thread where RiseHub has shared a detailed description of the infostealer, accompanied by screenshots of its C2 interface, followed by its rates, Telegram contacts and rules of use.

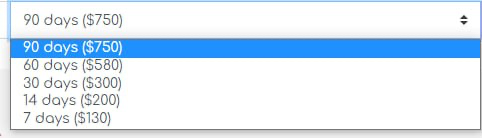
These publications allow RisePro to raise its profile within the cybercrime community, attracting potential customers. The cost of using RisePro ranges from $130 for 7 days, to $200 for 14 days, to as much as $750 for 90 days, offering different pricing options for interested users.

Some users on the forum feel that the prices offered are rather high, but RiseHub defends itself by pointing out that quality comes at a price.
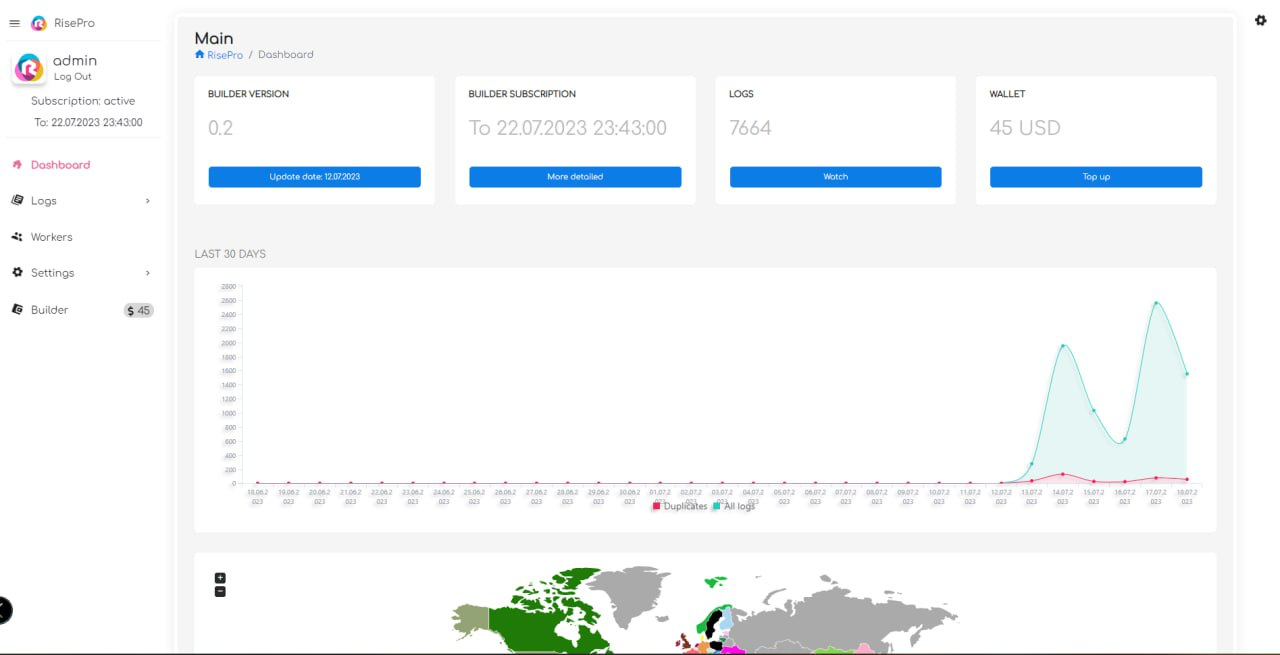
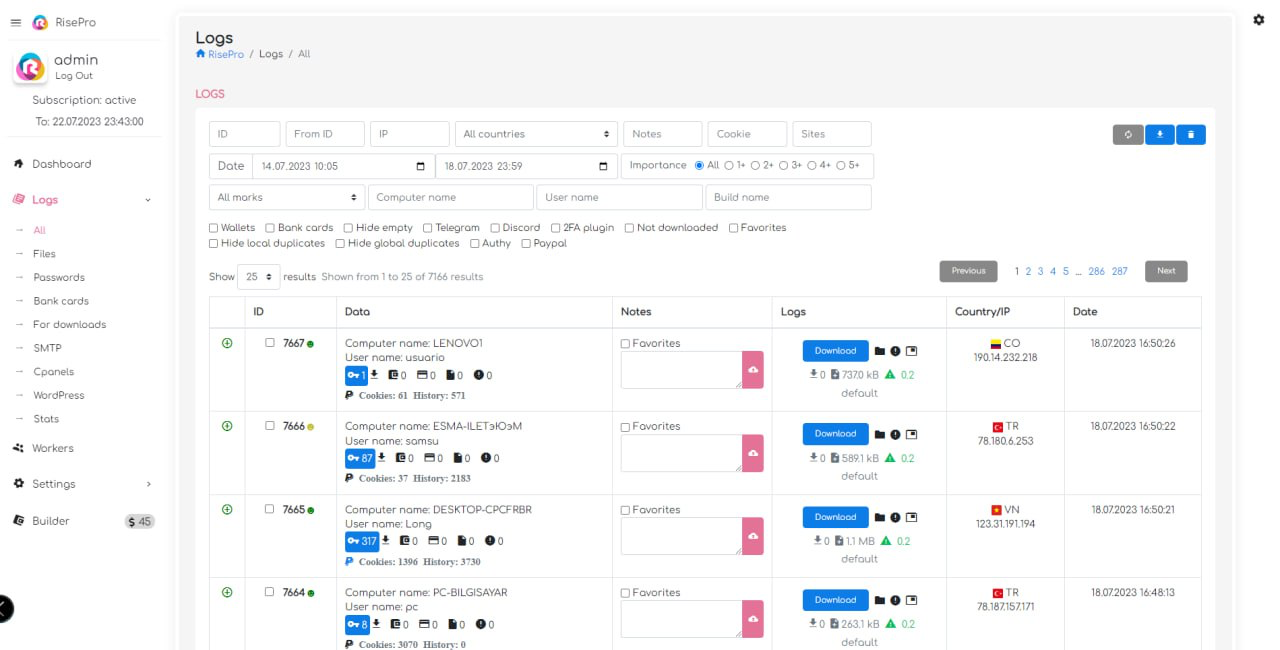
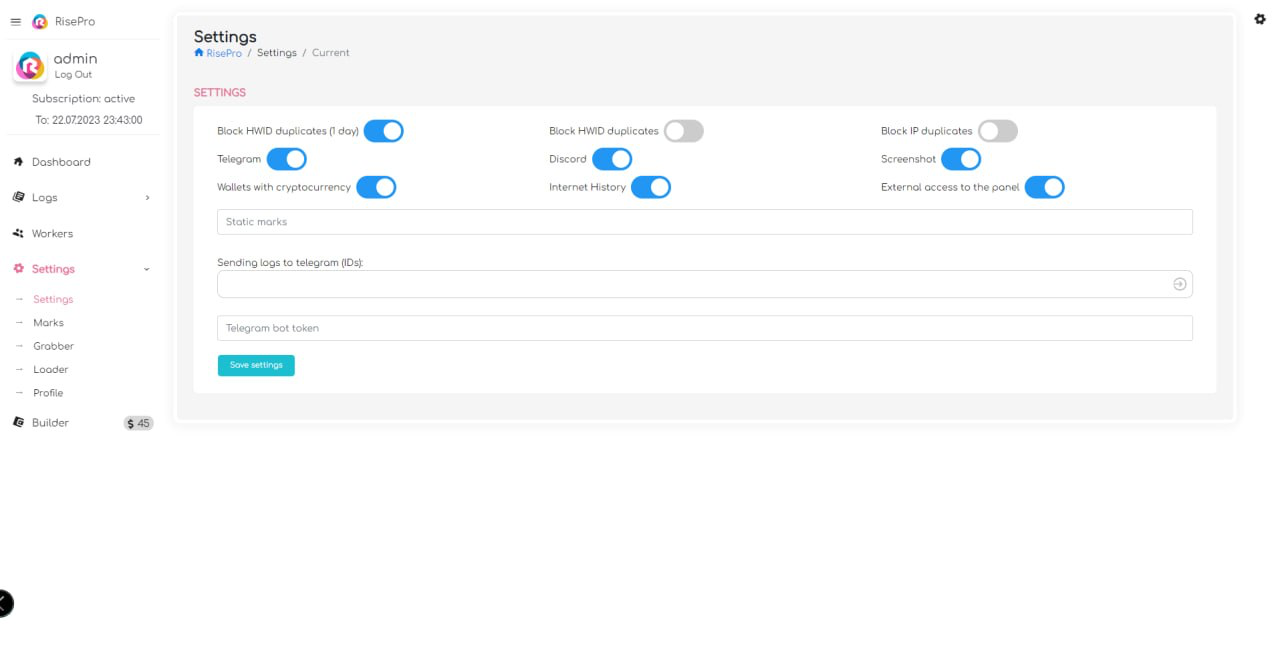
RiseHub’s promotion of its malware includes various screenshots of its C2. These images reveal a sleek, neat and rather high-quality design, on a par with the software available on the market.
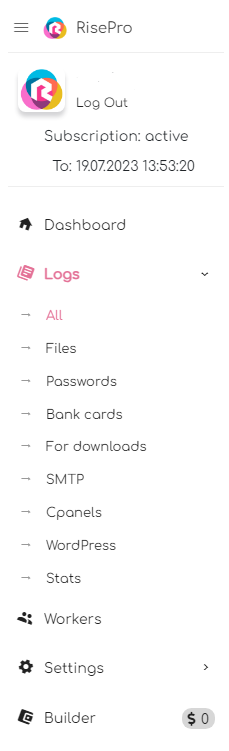
As can be seen from the screenshots shared, C2 offers a comprehensive range of features. There are a number of key aspects that demonstrate its rich functionality. These may include management of infected machines, data collection, management of malware user subscriptions, as well as advanced capabilities for manipulating stolen data. These details highlight the sophistication of the C2 used by RiseHub to orchestrate RisePro’s activities.
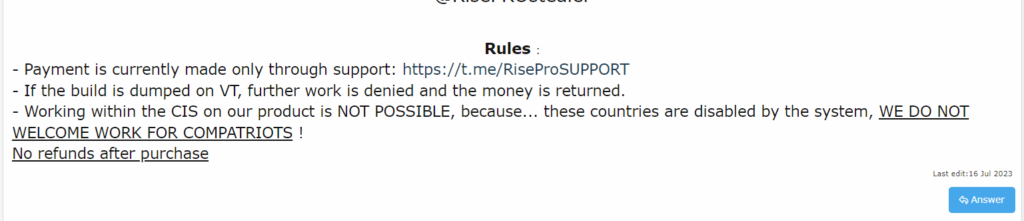
It is also interesting to note, in the forum post, the strict usage rules set out for the infostealer. Payment for the subscription can only be made via Telegram. What’s more, if a user’s build is detected on VirusTotal, all collaboration with that user is stopped and the money is refunded.
One important rule clearly states that it is forbidden to attack individuals from the Commonwealth of Independent States (CIS), the former Soviet countries. RiseHub even specifies that technically, an attack with RisePro on computers from these countries would be impossible and would be blocked by the system. These rules are common among hackers and malware from this geographical region.
Of course, RiseHub points out that there are no refunds after purchase.
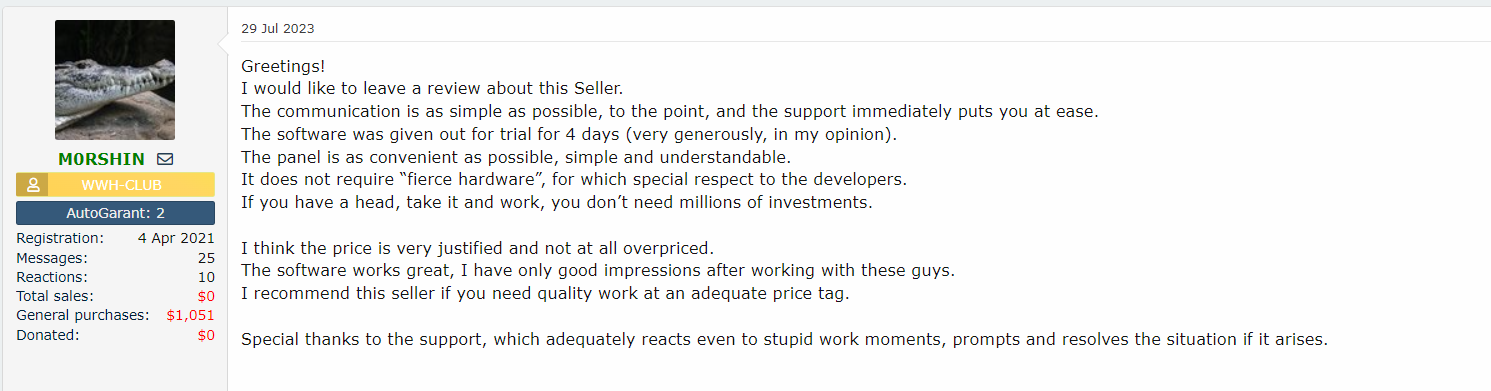
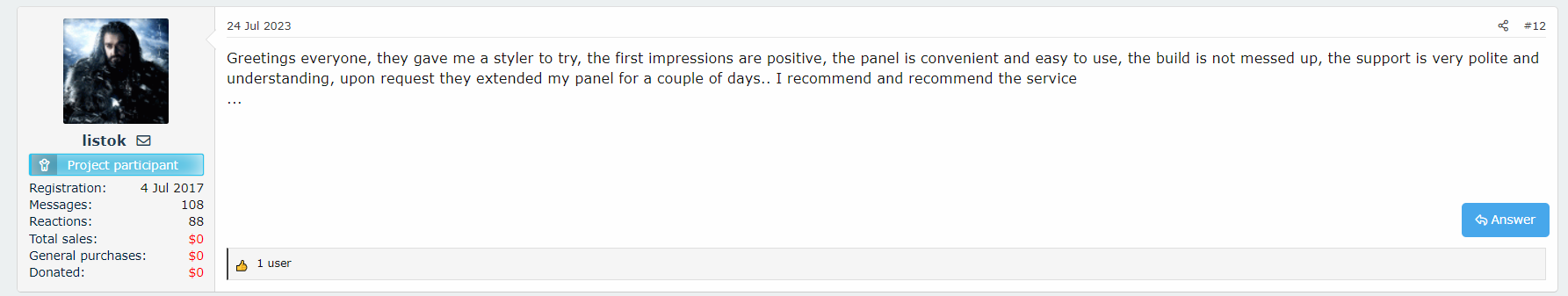
Looking at the discussion threads and the various interactions, it is clear that RisePro is receiving positive reviews. Cybercriminals who have used the service seem satisfied with its functionality and effectiveness.
Finally, it is also important to note that RiseHub is active on this forum, having last interacted on 17 November.
HackForum
On HackForum, RiseHub has published a post similar to the one on WWHClub. It promotes RisePro, shares the same screenshots of its C2 and presents the software’s prices. On this forum, all the content is in English, unlike WWHClub where the exchanges were in Russian.

We note that RiseHub also appears to be active on its discussion thread on this forum, with its last post dated 8 September.
RisePro Infrastructure
By combining different OSINT methodologies and tools, and drawing on the work of CTI analysts and Threat Hunters such as BushidoToken and Michael Koczwara, I was able to identify a list of active RisePro C2s as well as a number of inactive C2s. This section will be dedicated to explaining the various tools and techniques I used in this research. All the IoCs (Indicators of Compromise) found are available at the end of this article.
Google Dorks
The search began using Google Dorks. During this exploration, it was easy to see that the titles of C2 pages often included “Log In – RisePro”. However, on some C2s, ‘Login’ was written as a single word. Using Google Dork was therefore very easy to find RisePro C2s: ““Log In — RisePro“ OR “Login — RisePro“”. This query enabled me to find several IP addresses and an associated domain name.
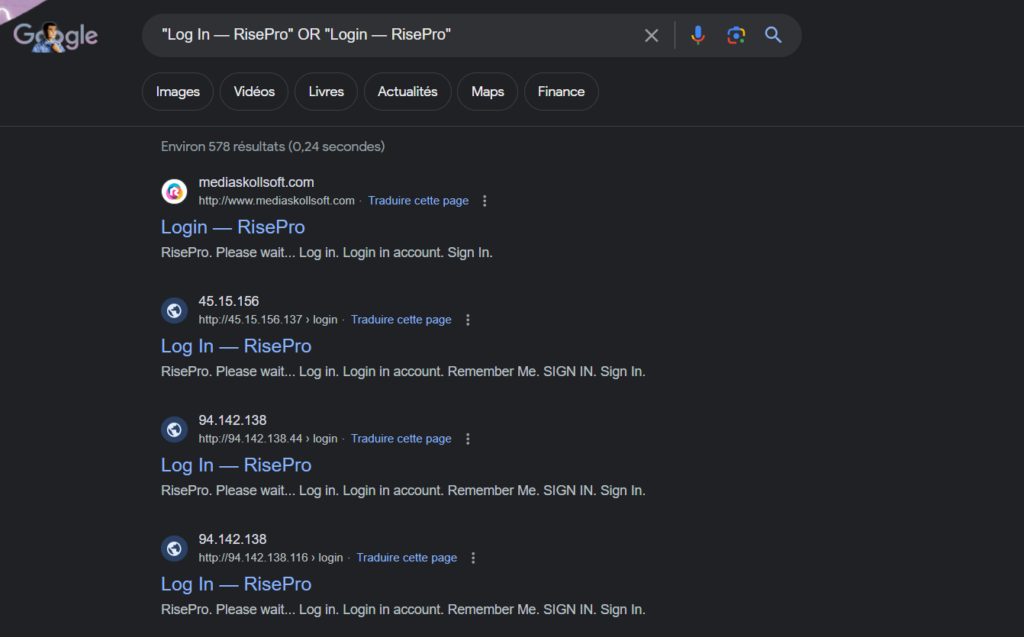
As you can see, some C2s are active:
Shodan
Shodan is a search engine specialising in exploring and indexing devices connected to the Internet. Unlike traditional search engines that scan website content, Shodan focuses on crawling connected devices, such as servers, routers, IP cameras, home automation systems and more. It allows users to perform specific searches to find devices based on their technical characteristics, such as the type of service they offer, their geographical location or their access provider.
When using Shodan, I used various queries, but only got one result.
Censys.io
Censys.io is a research and monitoring platform specialising in the collection and analysis of data relating to computer networks and devices connected to the Internet. It offers users access to a vast database containing detailed information on devices, protocols, SSL certificates, vulnerabilities and other data relating to online infrastructure. Censys.io offers advanced search capabilities allowing users to explore and categorise devices based on specific criteria such as IP addresses, open services, certificates used and much more.
Initial searches on Censys.io were characterised by the use of the following query: “( services.http.response.html_tags=“<title>Log In — RisePro</title>“ or services.http.response.html_tags=“<title>Login — RisePro</title>“ )”. This search uncovered 8 C2s from RisePro.
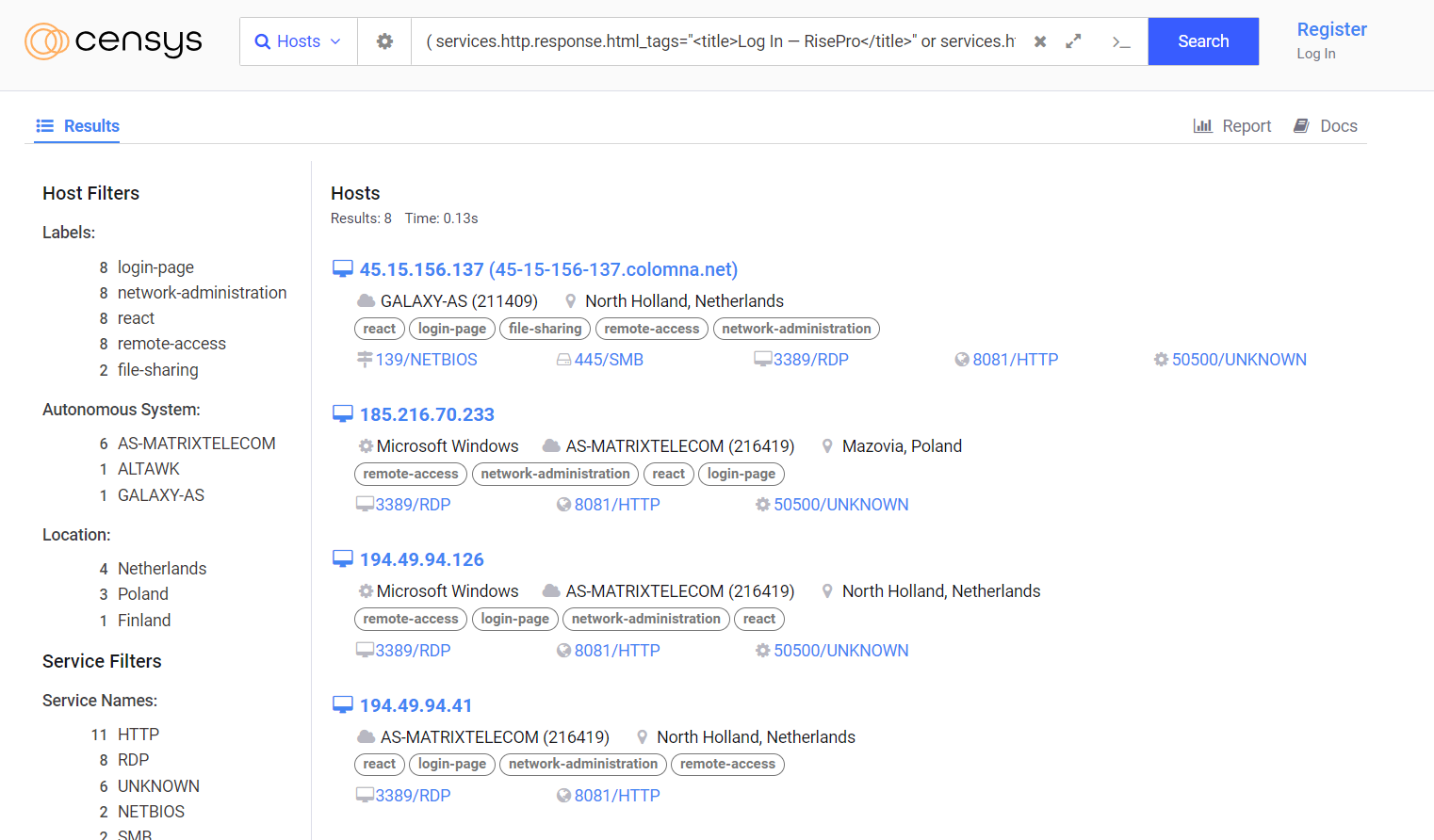
By noting certain similarities between the machines, the query could be refined by adding “autonomous_system.name=“AS-MATRIXTELECOM“”. Out of 6 machines, 5 had identical configurations. All were running Windows, had ports 3389, 8081 and 50500 open, and shared the same Autonomous System (AS).
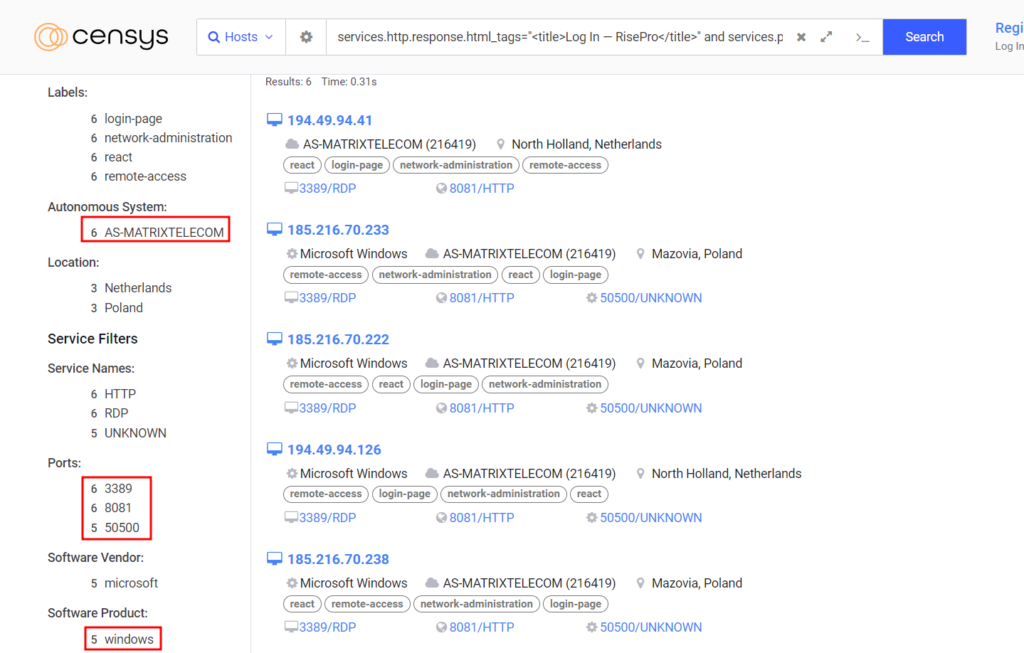
It is plausible that these RisePro C2 instances belong to the same malicious actor, potentially a RisePro customer, or that they are instances set up by the RisePro operator itself to serve its customers.
FOFA.info
FOFA.info is a search engine dedicated to mapping global cyberspace, positioning itself as China’s competitor to Shodan. Through active detection of the world’s Internet assets, it has identified more than 4 billion entities. This vast database also includes 350,000 fingerprints, enabling the identification of a large number of software and network hardware. Data on these assets can be exploited in a variety of ways to support external presentations and diverse applications, and can generate hierarchical profiles based on IP addresses.
FOFA is an incredibly powerful tool. To initiate searches it was possible to use a query similar to the previous ones: “title=“Login — RisePro“ || title=“Log In — RisePro“”. Thanks to this query, it was possible to identify a total of 64 RisePro C2 IP addresses.
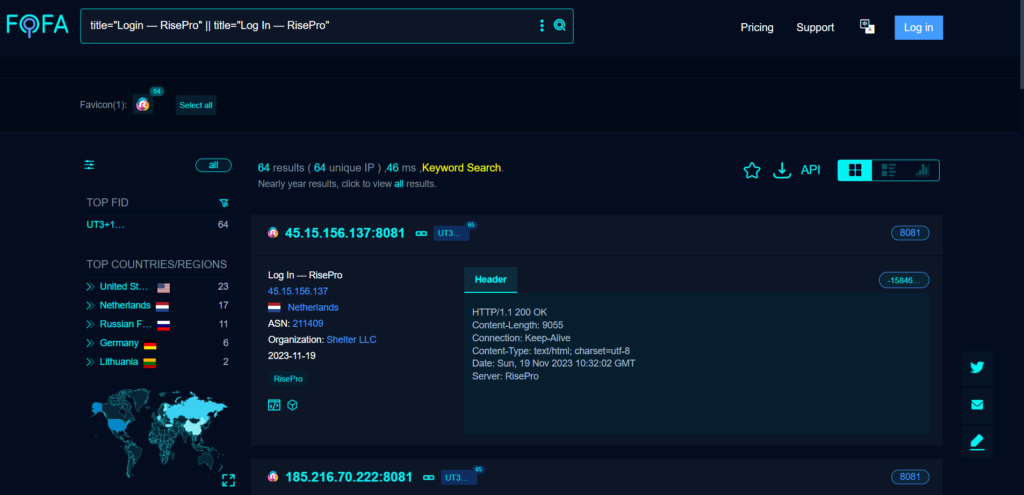
FOFA was able to detect almost all the IP addresses found using other tools. In total, 12 C2s were active out of 64.
Analysis of the results obtained
By combining all these tools, it was possible to trace 66 instances of RisePro C2, comprising 65 IP addresses and one domain name. Of these 66 instances, only 13 are active, comprising 12 IP addresses and 1 domain name. Unfortunately, it was difficult to use the different IP addresses as a pivot point for further investigation.
The C2 with a domain name is the only one of the 65 to have an SSL certificate and a domain name. Exploring the DNS records, an interesting sub-domain hosting a site called “EasyLead” stood out.
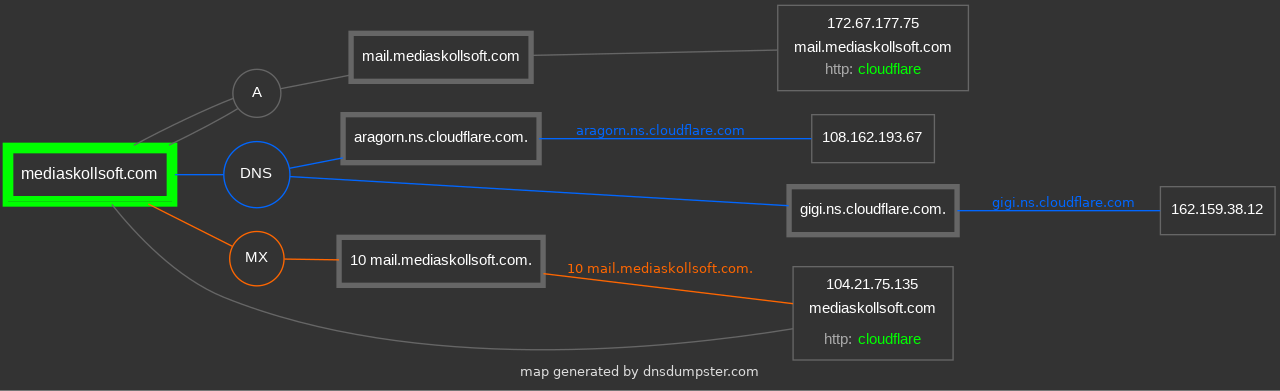
EasyLead was found on the subdomain mail.mediaskollsoft[.]com. Browsing mail.mediaskollsoft[.]com showed the following page:
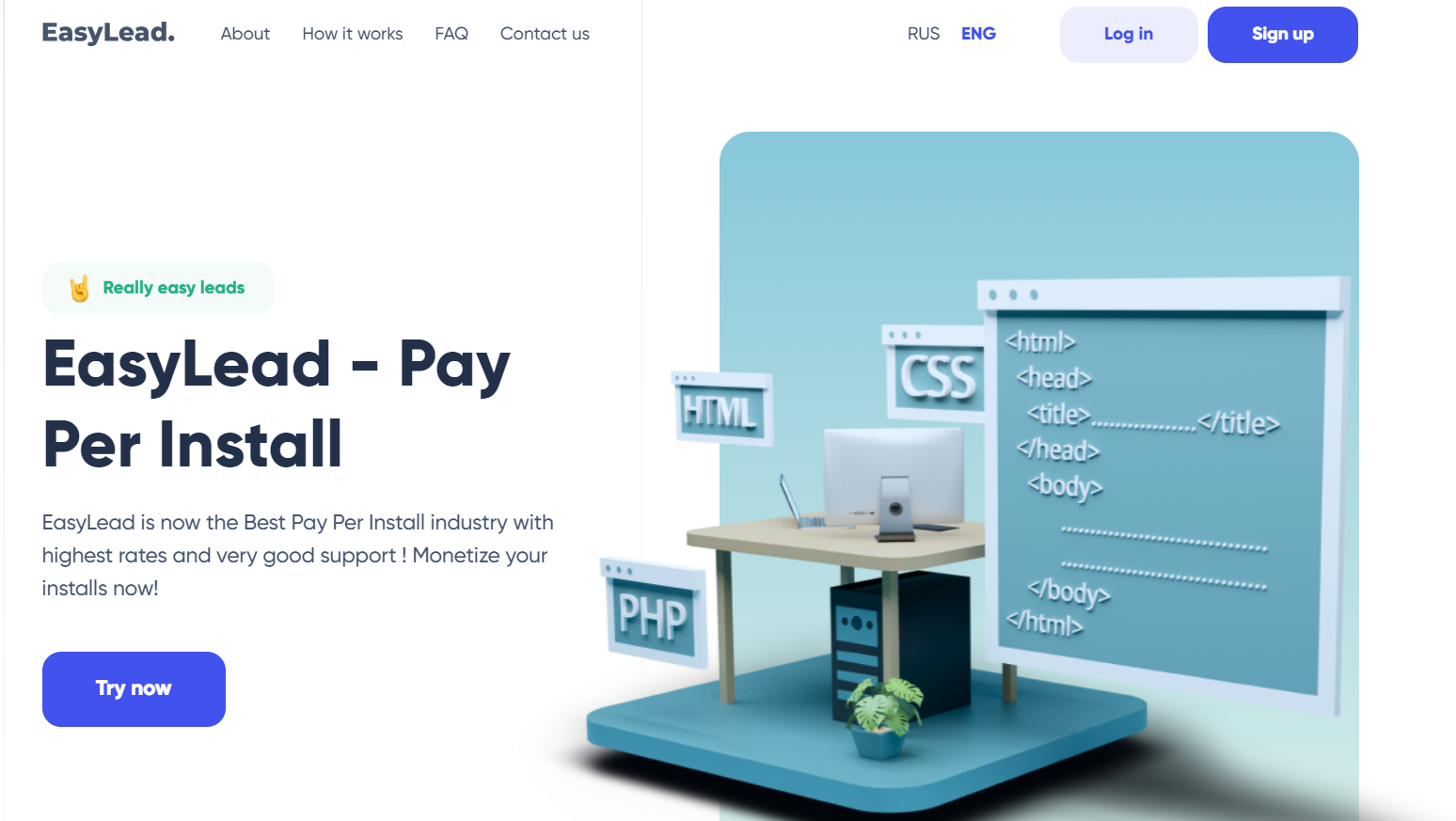
EasyLead, a Pay Per Install service
EasyLead presents itself as a platform for monetising software installations. They claim to offer the best rates on the market as well as responsive support. The platform prides itself on being easy to use and integrate into marketing campaigns, currently claiming to be the best in the Pay Per Install industry.
To get started with EasyLead, the site says that all you have to do is register on their platform and choose the software you want to promote. Next, a unique link is supposed to be generated to be shared with the targeted audience. Each time software is installed via this link, a commission is theoretically earned. Performance and revenue are then available on the user’s dashboard.
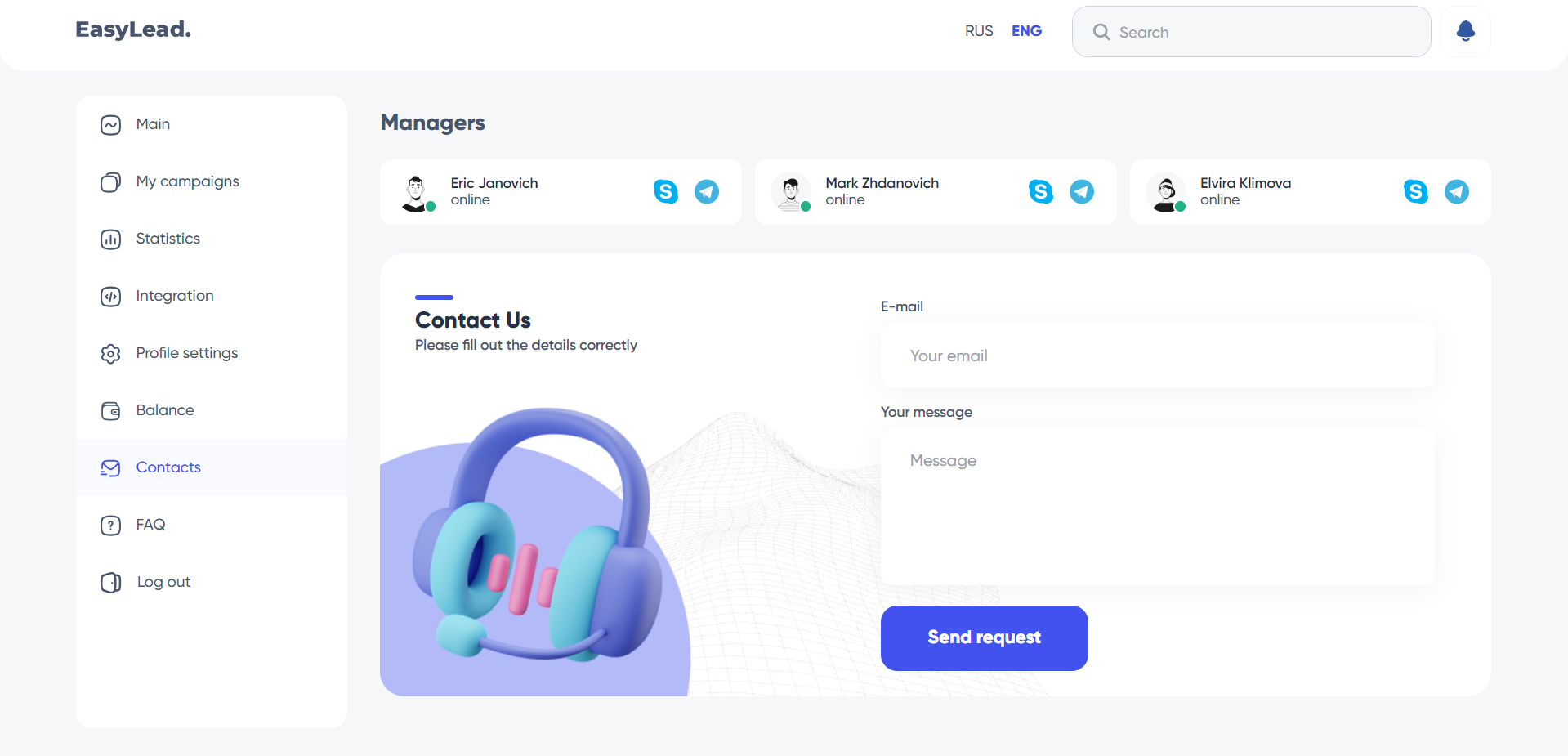
EasyLead also offers an FAQ section on its website, as well as support via e-mail, Skype or Telegram. They assure you that they are always available to listen and help their users.
At first glance, the website looks legitimate, with all the hallmarks of a genuine business. However, it should be noted that several links and buttons appear to be non-functional, particularly those leading to the legal notices or terms of use.
Running a basic search on FOFA with the query ““EasyLead“ && title==“ Really easy leads “”, this returned 4 results, with 1 duplicate domain name and 2 IP addresses. The two IP addresses are located in Russia, while the domain name is protected by Cloudflare.
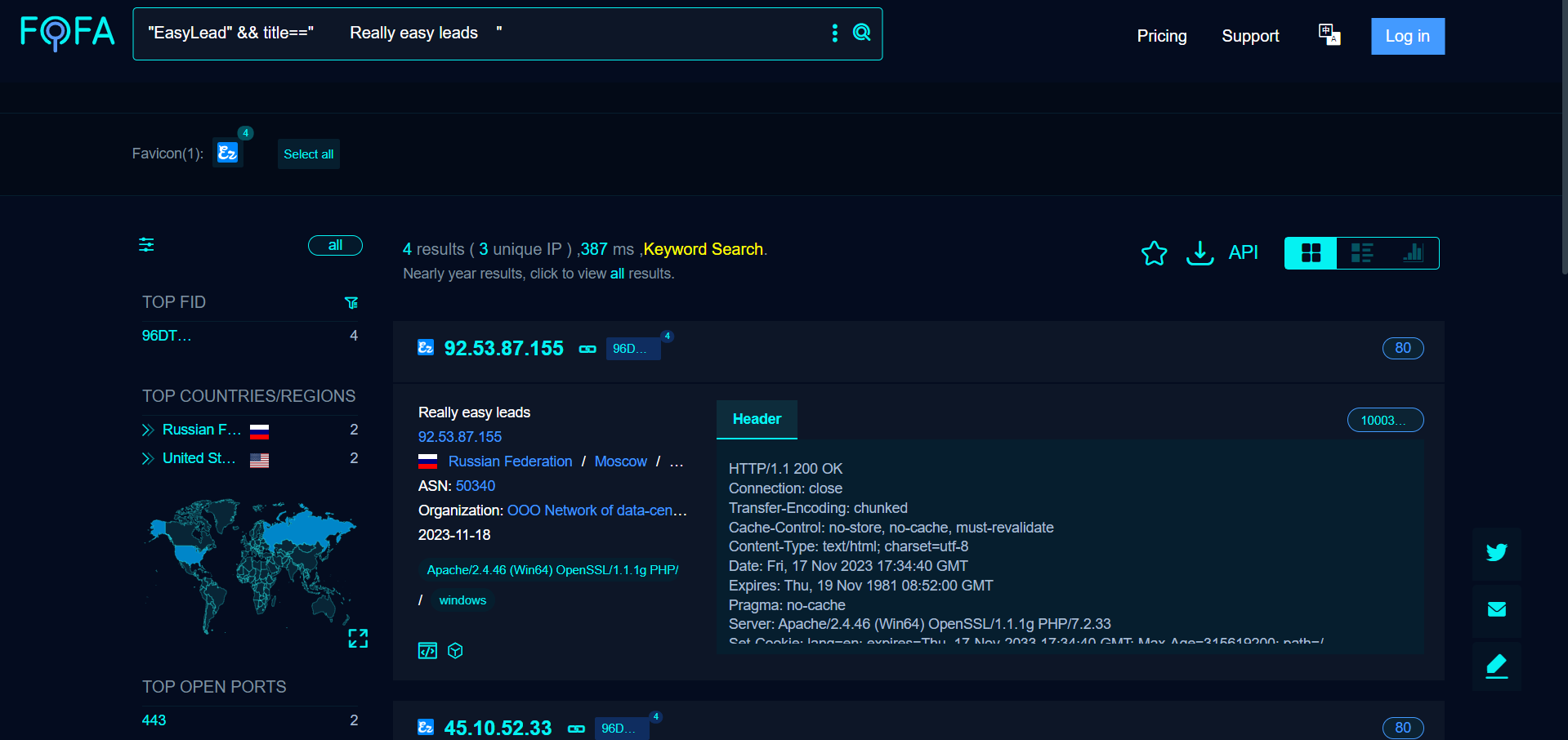
Each of these instances hosts an identical copy of the EasyLead frontend. This uniformity raises suspicions about EasyLead’s legitimacy.
We therefore identified four identical instances of the EasyLead website, this mysterious PPI (Pay Per Install) service:
- 45.10.52.33
- 92.53.87.155
- mail.mediaskollsoft[.]com
- ezlead[.]pro
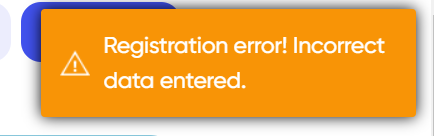
To investigate further, it would be interesting to create an account on these sites. Strangely, creating an account only worked on one site, ezlead[.]pro, while on the others, errors cropped up at every attempt.
The rest of this section will focus on the Ezlead instance.
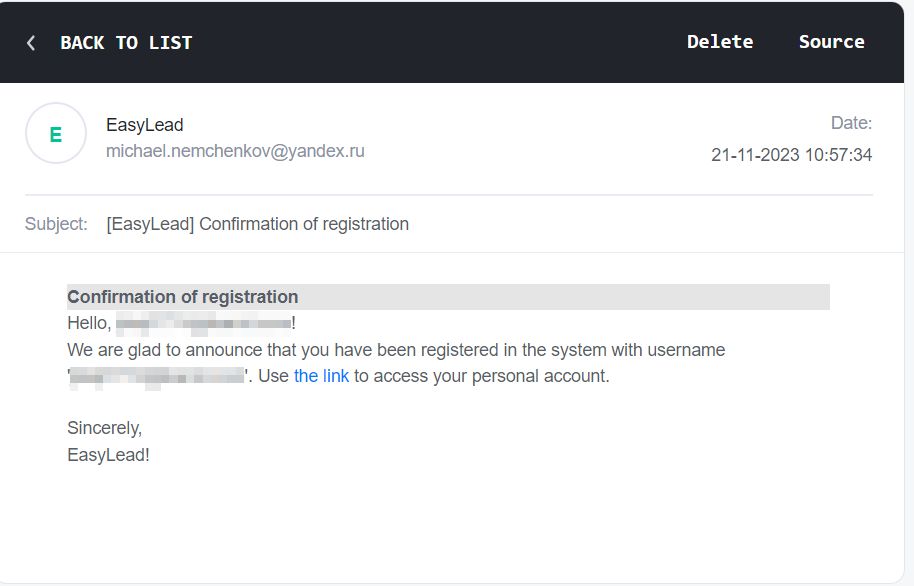
Ezlead
After registering on the site, I received a confirmation e-mail in my inbox. The e-mail came from “michael.nemchenkov[@]yandex[.]ru”.
Once connected to the site, it was possible to access several new pages:
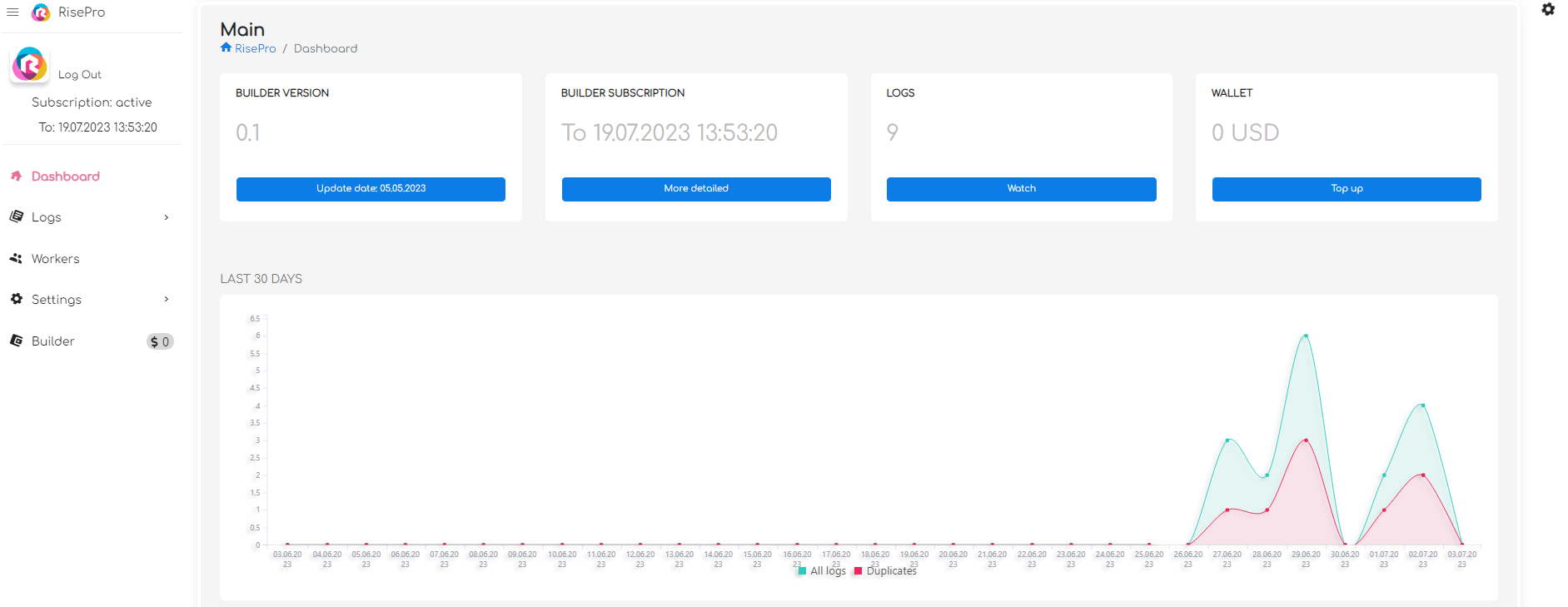
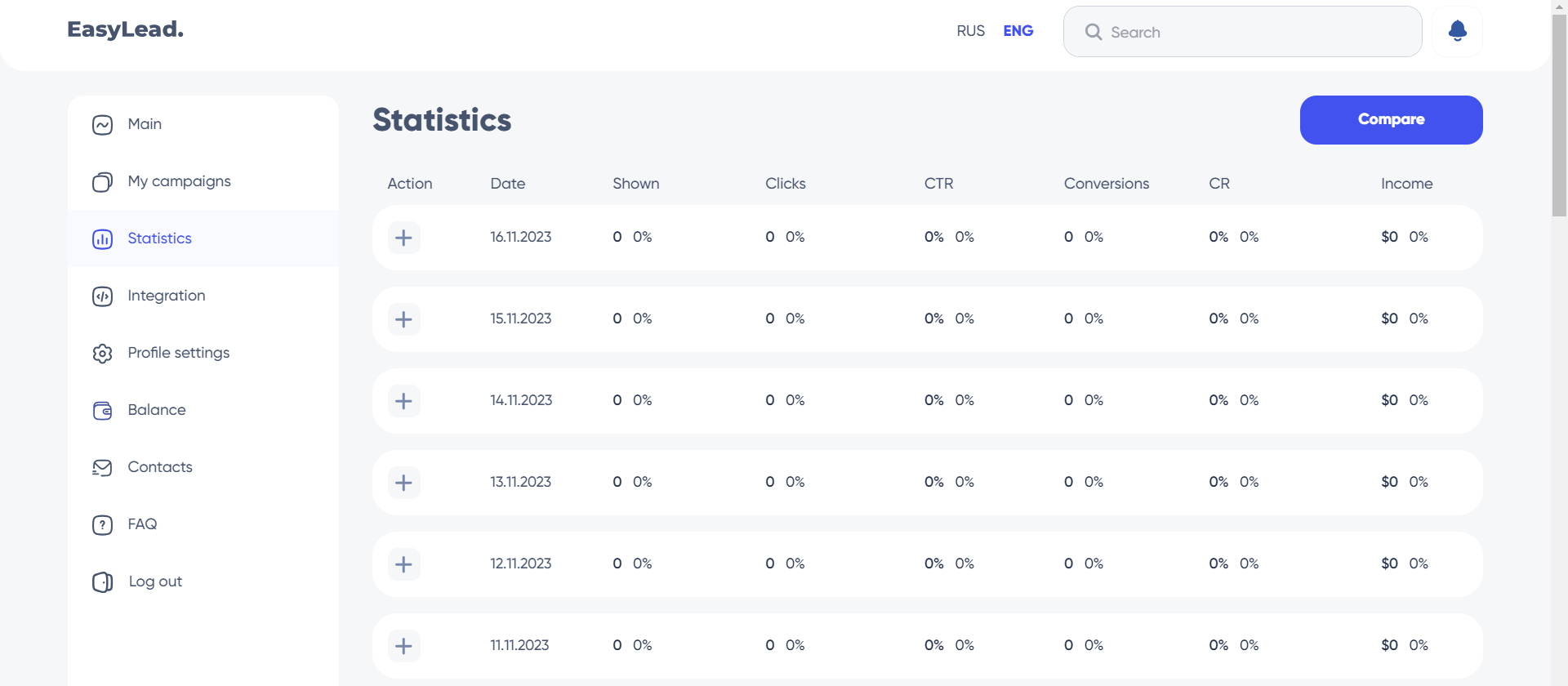
- The main page with a dashboard
- The page dedicated to my campaigns
- The campaign statistics page
- The integration page
- The settings page
- The page showing my cash balance
- The contact page
- The FAQ page
The site’s design is clean and professional, giving a sense of legitimacy. The platform offers a wide range of features, each of which seems to have been carefully designed to meet users’ needs. The simplicity of the navigation and the clear presentation of the different sections add to its professional appearance. Overall, the site looks serious and reliable, with a well-organised structure and attention to detail to deliver an optimal user experience.
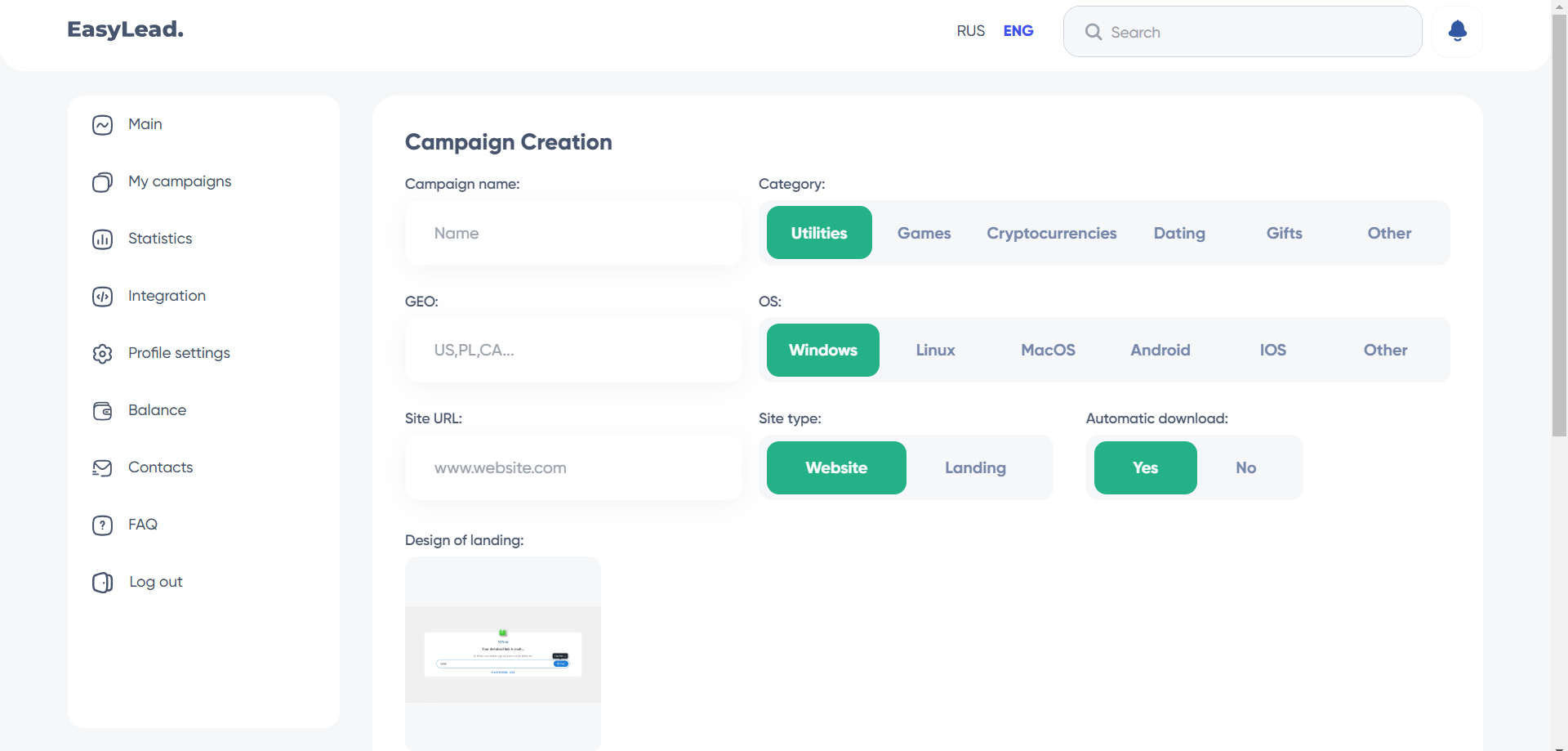
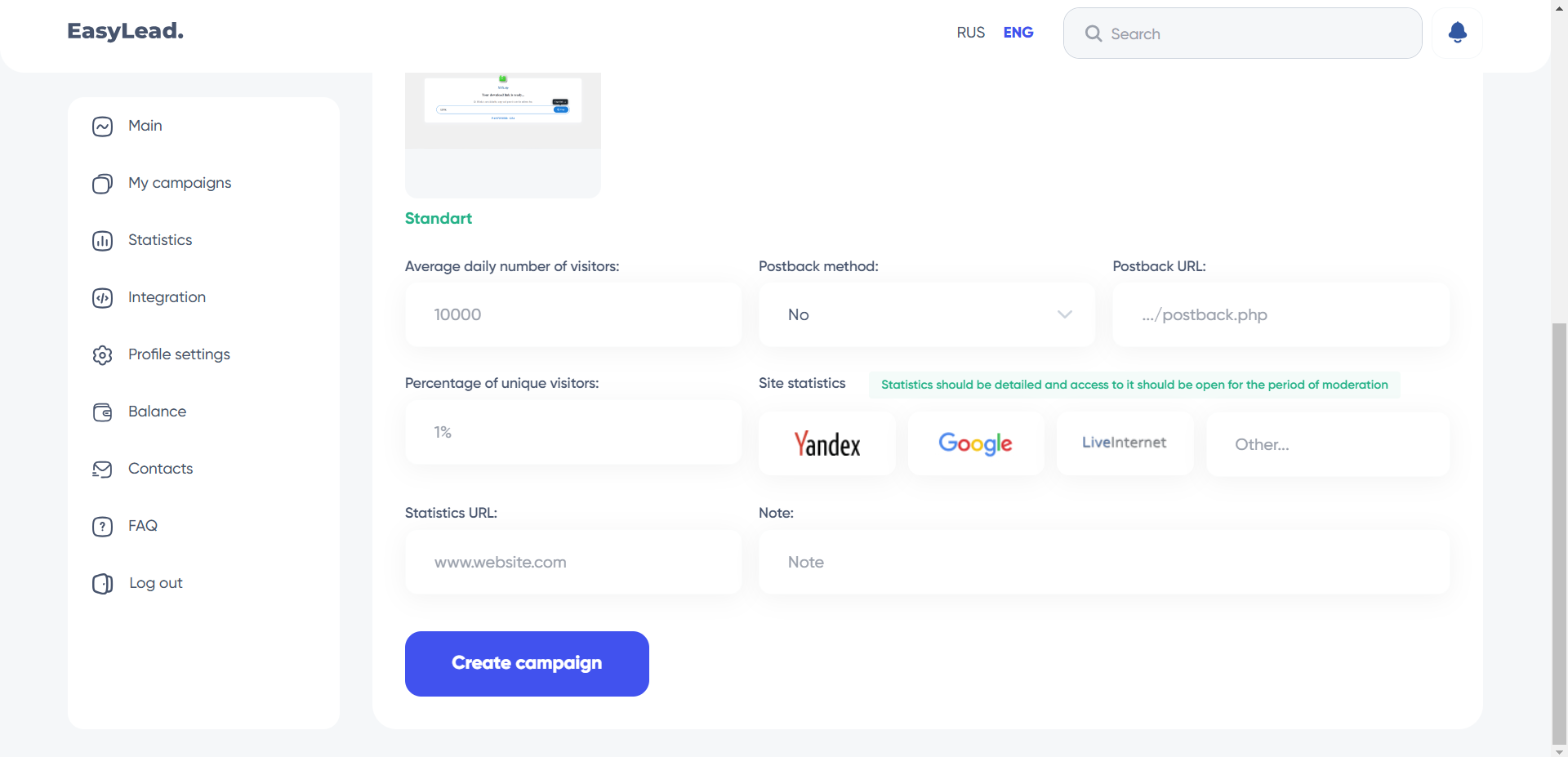
Exploring the platform’s main functionality, campaign creation, reveals a structured process. To initiate the creation of a new campaign, it was necessary to specify the name of the campaign, the target countries, as well as the type of software to be distributed from the proposed categories such as Utility, Games, Crypto, Dating, Gifts or Other. Next, the operating systems compatible with the software had to be specified.
The platform also requests information about the site where the software to be distributed is hosted, asking you to choose the type of website and define the download parameters. Other details are requested, such as the average number of visitors to the site, the percentage of unique visitors, the service used for site statistics, and a link to these statistics. This structured and detailed approach enables campaigns to be tailored in depth to meet the specific needs of users.
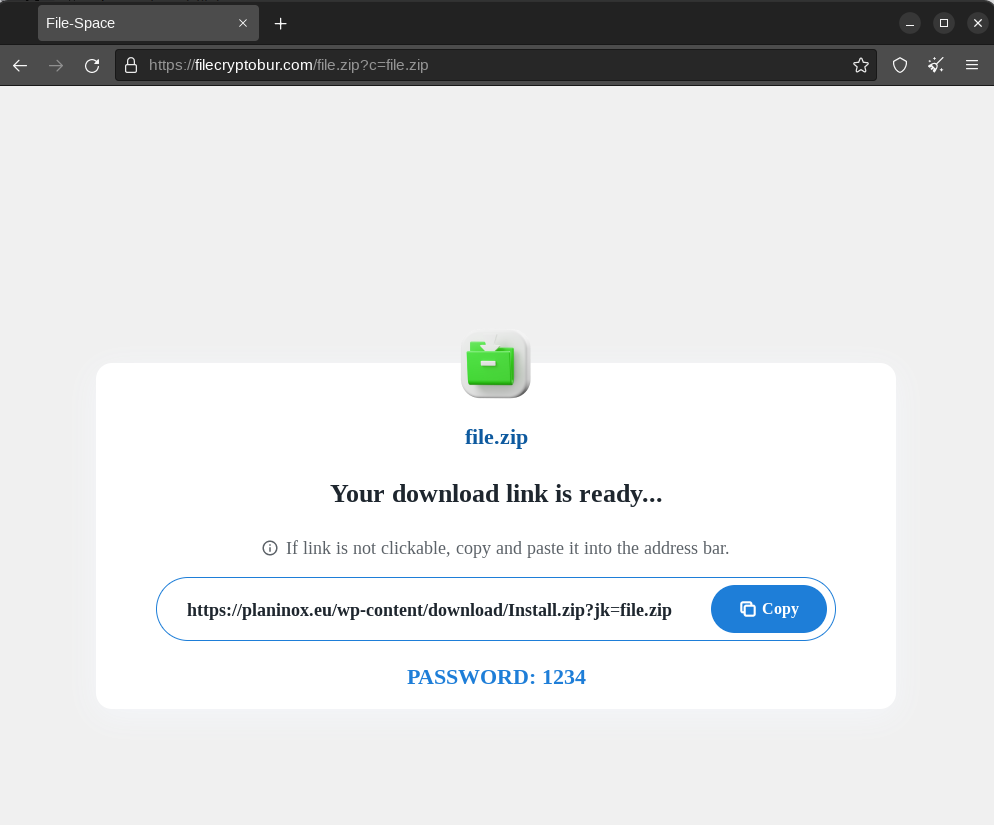
In this menu, an image of the design of the home page associated with our link during the campaign is visible. This page corresponds to the one discovered by SEKOIA.IO on the PrivateLoader distribution sites in its report. We can see the same design with the same logos and colours, it’s precisely the same page design.
In its report, SEKOIA.IO states that “the redirect URL to download the malware changed regularly, at least once a day” and that “the payload available for download on compromised WordPress sites is PrivateLoader, which installs a set of infostealers (RedLine, MixLoader, Vidar, etc.)”. This highlights a link between the EasyLead PPI service and the PrivateLoader loader, which is used by various malicious actors to propagate various malicious payloads, mainly infostealers such as RisePro. In a separate report, FLASHPOINT analysts claimed to have identified several samples of RisePro deployed via the PrivateLoader service.
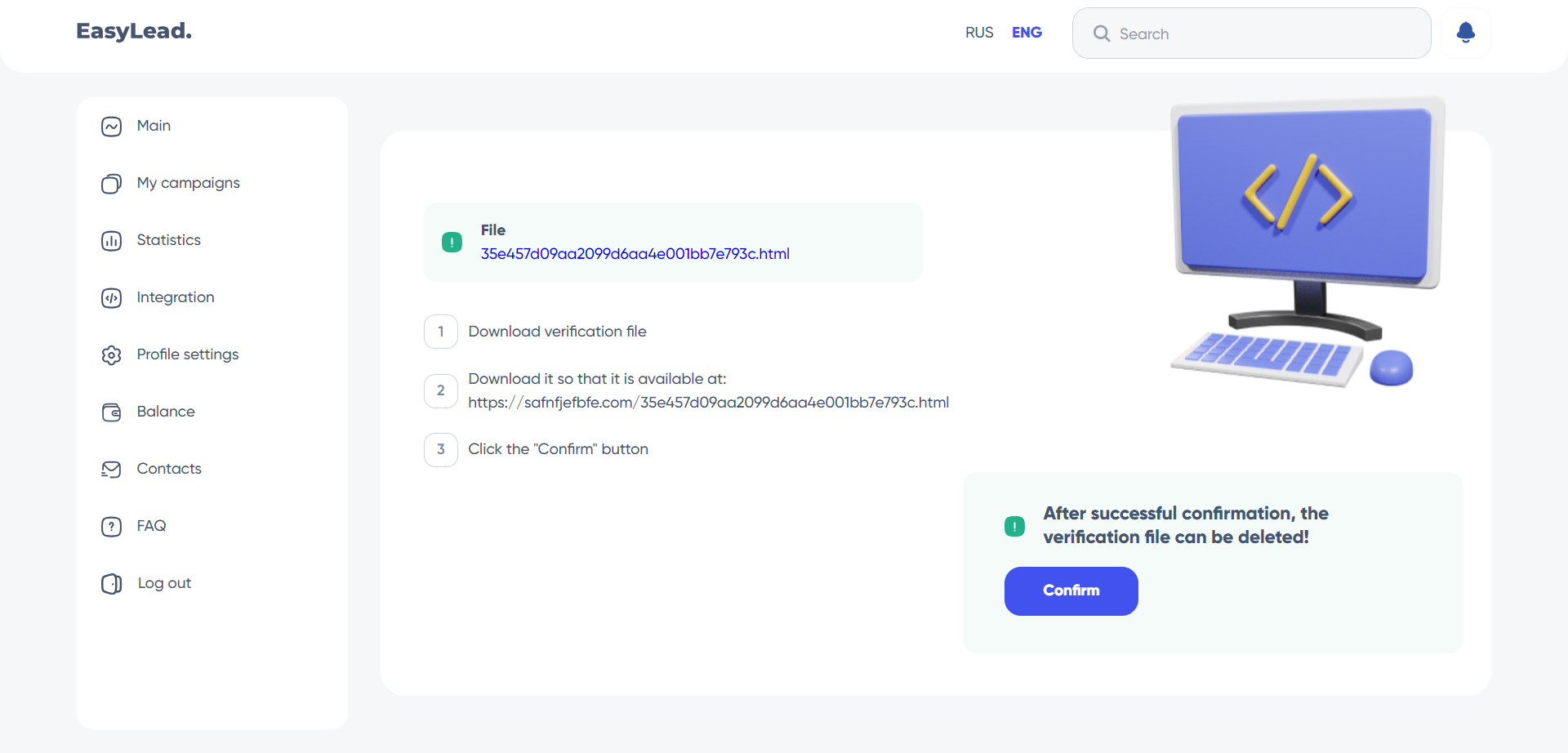
Back to the distribution campaign. Once it has been created, EasyLead asks us to confirm it by adding a specific HTML file to the root of our website. At the same time, the statistics menu changes to display daily data.
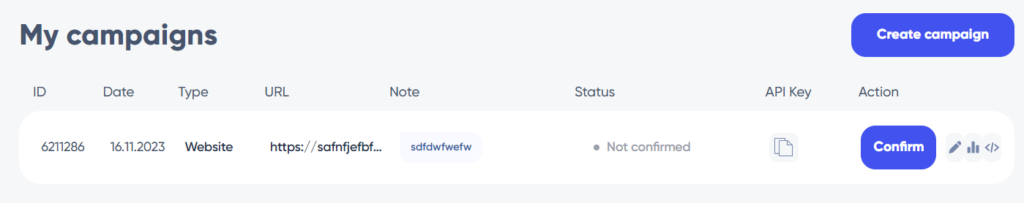
The content of the HTML file is not sophisticated: it’s just a simple string of characters :
Once the HTML file has been added to the root of the site and the campaign confirmed, its status changes to “Moderation”. It would appear that validation by the EasyLead team is required before the distribution campaign can be launched. Despite a two-week wait, the status of the campaign remains unchanged.
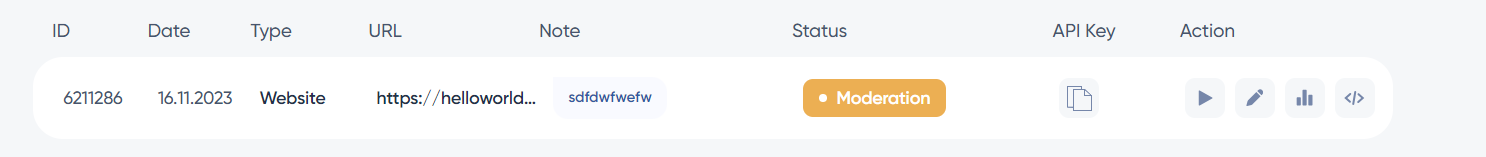
In-depth analysis
The ezlead[.]pro site is a key element that requires further investigation. The first step is to check the site’s WHOIS register, which reveals some very interesting results:
- The depositary’s organisation is LLC “MediaCube”.
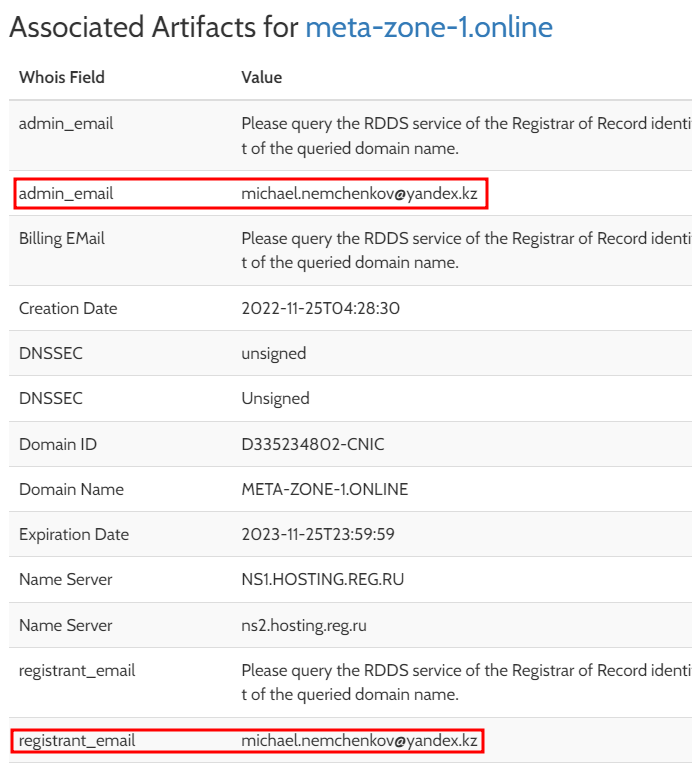
In addition, a Google search for more information on the e-mail address “michael.nemchenkov[@]yandex[.]ru”, previously found, leads to a similar address “michael.nemchenkov[@]yandex[.]kz”. This was found in the results of a malware analysis carried out by Hybrid Analysis.
In this analysis, malware with a risk score of 100/100 was detected in contact with the domain “meta-zone-1[.]online” via DNS. The WHOIS registry reveals that this domain name has been registered with the e-mail address “michael.nemchenkov[@]yandex[.]kz”.
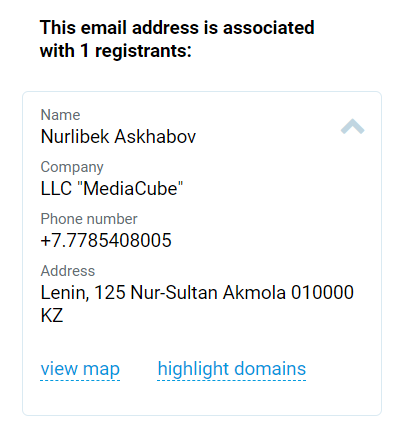
A further search for the e-mail address on website.informer.com yielded more results. We found :
- The company LLC “MediaCube”
- The first and last name of an individual : Nurlibek Ashabov
- A telephone number : +77785408005
- An address in Kazakhstan : Lenin, 125 Nur-Sultan Akmola 010000 KZ
This information has been corroborated by various WHOIS searches carried out by website.informer.com. We can therefore consider it to be highly reliable.
Linked to this e-mail is a list of seven domain names:
- rate-files[.]com
- files-rate[.]com
- files-null[.]com
- gg-download[.]com
- gg-loader[.]com
- files-pipe[.]com
- file-broker[.]com
Four of these domain names are mentioned in the SEKOIA.IO report on RisePro. They share the same Whois record with two domains extracted from samples associated with RisePro.
- gg-download[.]com
- gg-loader[.]com
- files-rate[.]com
- rate-files[.]com
This discovery reinforces the links established between EasyLead and RisePro.
Back on Ezlead[.]pro, in the contact section, three people are listed. Each is supposed to have Telegram and Skype contacts. None of these people has a Skype contact, but only the first named “Eric Janovich” has a Telegram account under the username “@king420S”.
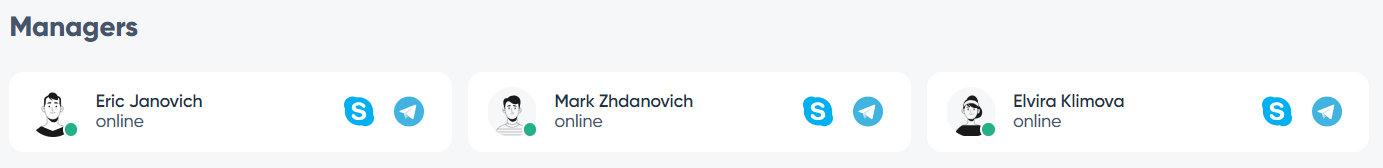

There appears to be an interesting correlation when examining the WHOIS information for the domain names mentioned in the SEKOIA.IO report. For example, for the domain “best24-files[.]com”, the WHOIS reveals :
- Registrant Name: Nikolai Petrov
- Registrant Phone: +77785408005
- Registrant Email: king420.lazy[@]gmail[.]com
A match emerges: the associated telephone number matches that of Nurlibek Ashabov mentioned earlier, and the owner’s email address displays the username “King420”.
There appears to be a close connection between these different entities. Analysis of the email address associated with Nikolai Petrov using the tool on website.informer reveals 17 associated domains, 10 of which appear in the SEKOIA.IO report as mentioned above. In addition, Nikolai Petrov’s profile reveals an additional domain “jojo-files[.]com”, also mentioned in the SEKOIA.IO report. All in all, there are 18 domains linked to Nikolai Petrov, 11 of which are associated with the RisePro infostealer. This correlation reinforces the idea of a connection between these elements. (All the IoCs are available at the end of the article)
Indeed, each discovery reinforces the correlation between EasyLead and RisePro. The clues and connections between these entities seem to be getting closer and closer.
Using the Epieos tool, the correlation between the email address associated with Nikolai Petrov, king420.lazy[@]gmail[.]com, and the Telegram account mentioned on Ezlead[.]pro, attributed to a certain “Eric Janovich”, was confirmed. Epieos revealed that the Gmail address has the same profile picture as the Telegram account in question.
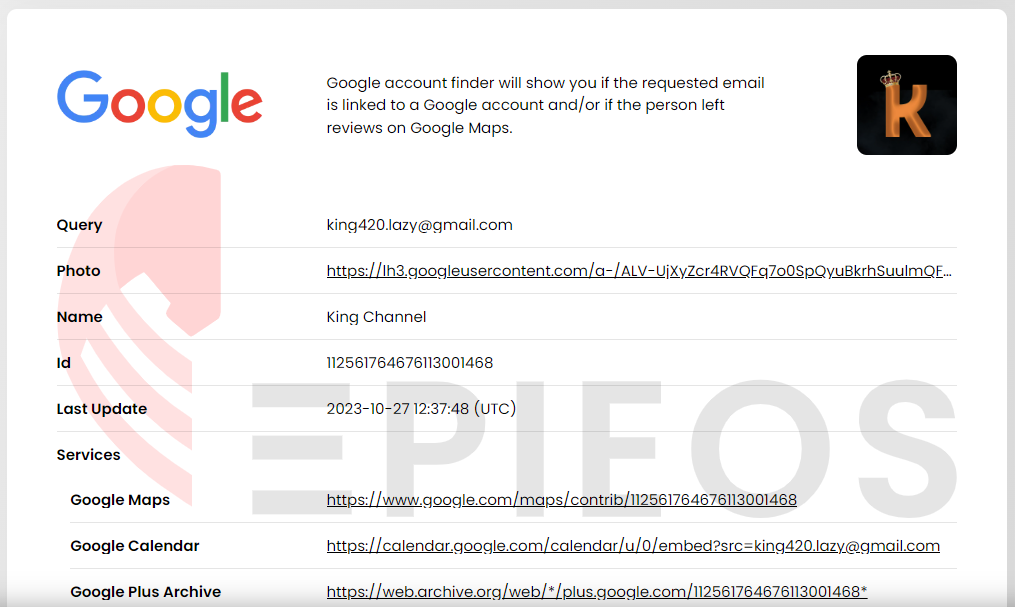
In-depth exploration of the links between EasyLead and RisePro reveals a complex interconnection between these players. Investigations ranging from the analysis of domain names to profiles associated with the various platforms reinforce the idea of a close relationship between these entities. Cross-referenced data such as email addresses, telephone numbers and messaging profiles confirm links between individuals and services, apparently involved in the distribution and monetisation of infostealers.
The discovery of shared profiles on separate platforms, matches in WHOIS information and similarities between data from different investigative tools help to paint an overall picture, suggesting coordination or collaboration between these players.
These elements reinforce the hypothesis of a link between the EasyLead PPI service, the RisePro infostealer and its operator.
Making contact with the various actors
In order to obtain more information, it was decided to contact the various players identified above. The objectives are to understand the process of acquiring the RisePro infostealer and to establish a link between it and EasyLead PPI.
Contact with RisePro's operator
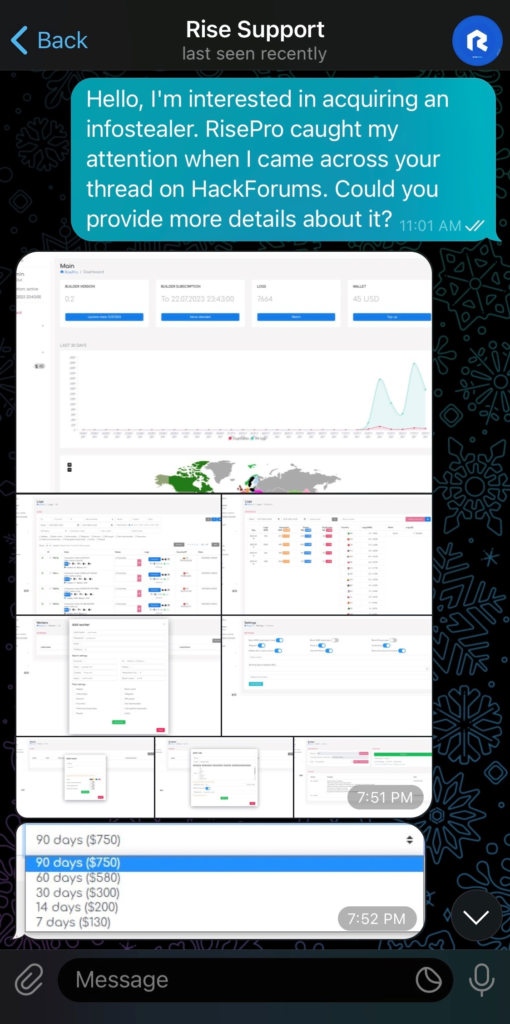
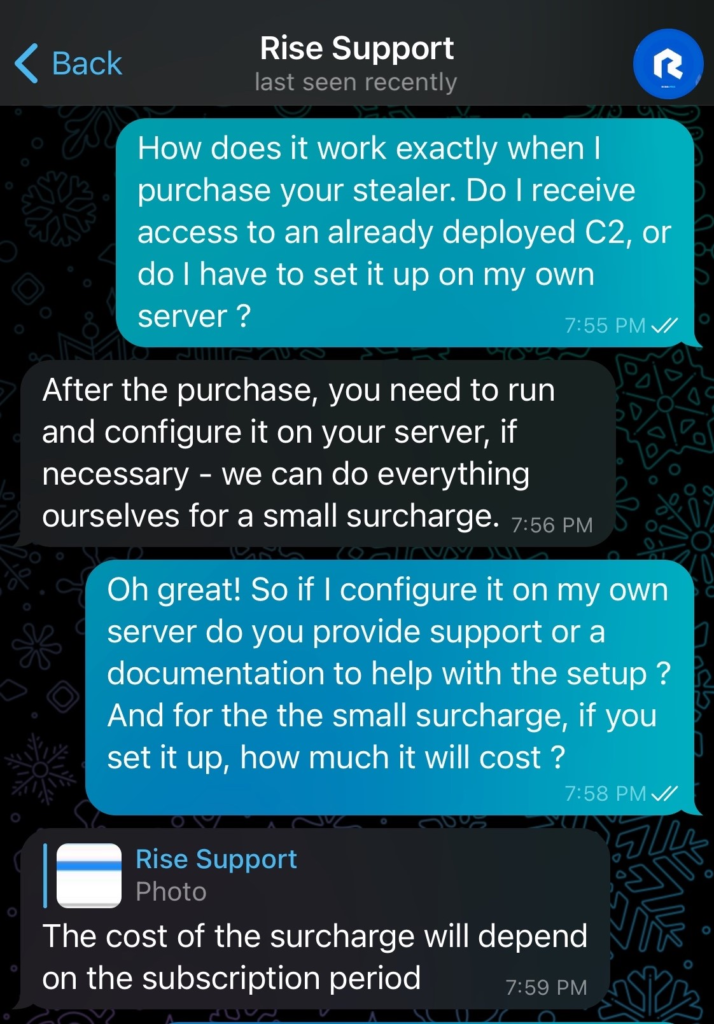
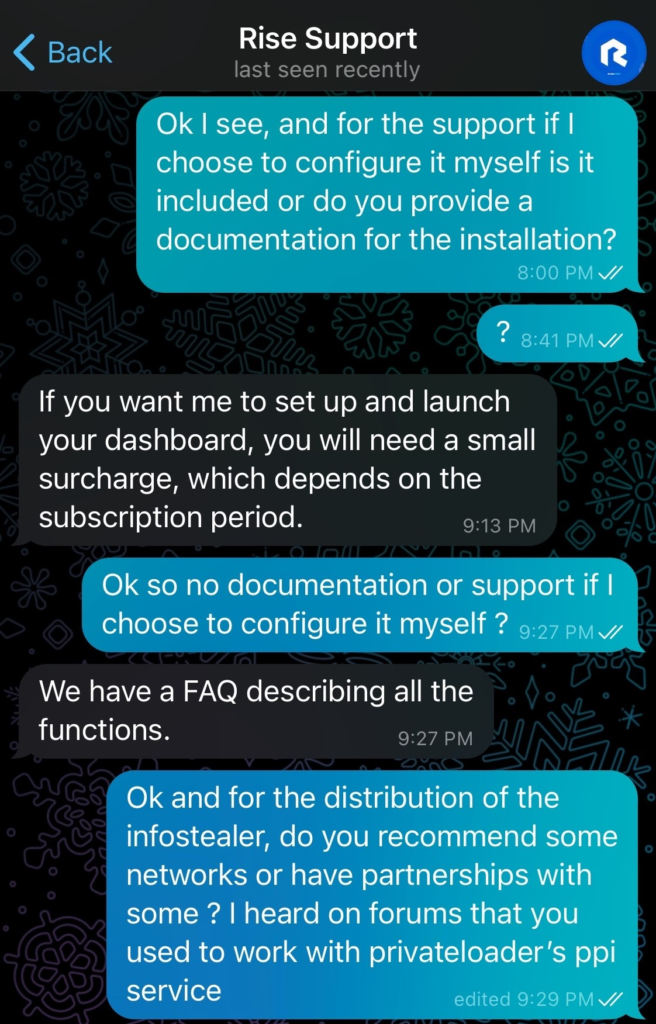
The conversation with the RisePro operator began by posing as a potential customer looking to acquire an infostealer, having discovered RisePro through its publications on the forums. I started by asking for a few more details about RisePro.
The first message was sent at 10:01 UTC, and we had to wait more than 8 hours to receive the first reply at 18:51 UTC: a series of 9 screenshots of C2 with no additional text :
The received screenshots differ from those previously posted on forums. They showcase various functionalities. A victim map has been added to the interface, and there’s an option to add new rules for the infostealer to target specific files. This indicates that RisePro is consistently evolving, with its operator continuously updating and adding features.
When probing about the C2 acquisition process, the RisePro operator explained that post-purchase, users need to configure the C2 on their own servers. However, they also offer to do it for a fee, which varies based on the subscription chosen. Regarding self-installation and configuration, there wasn’t much clarity on whether they provide user support or documentation for this phase.
This could explain the differences seen among the various detected C2s during the investigation. As for the multiple C2s with nearly identical configurations, it’s possible they are servers set up by the RisePro operator, as previously suggested in the article.
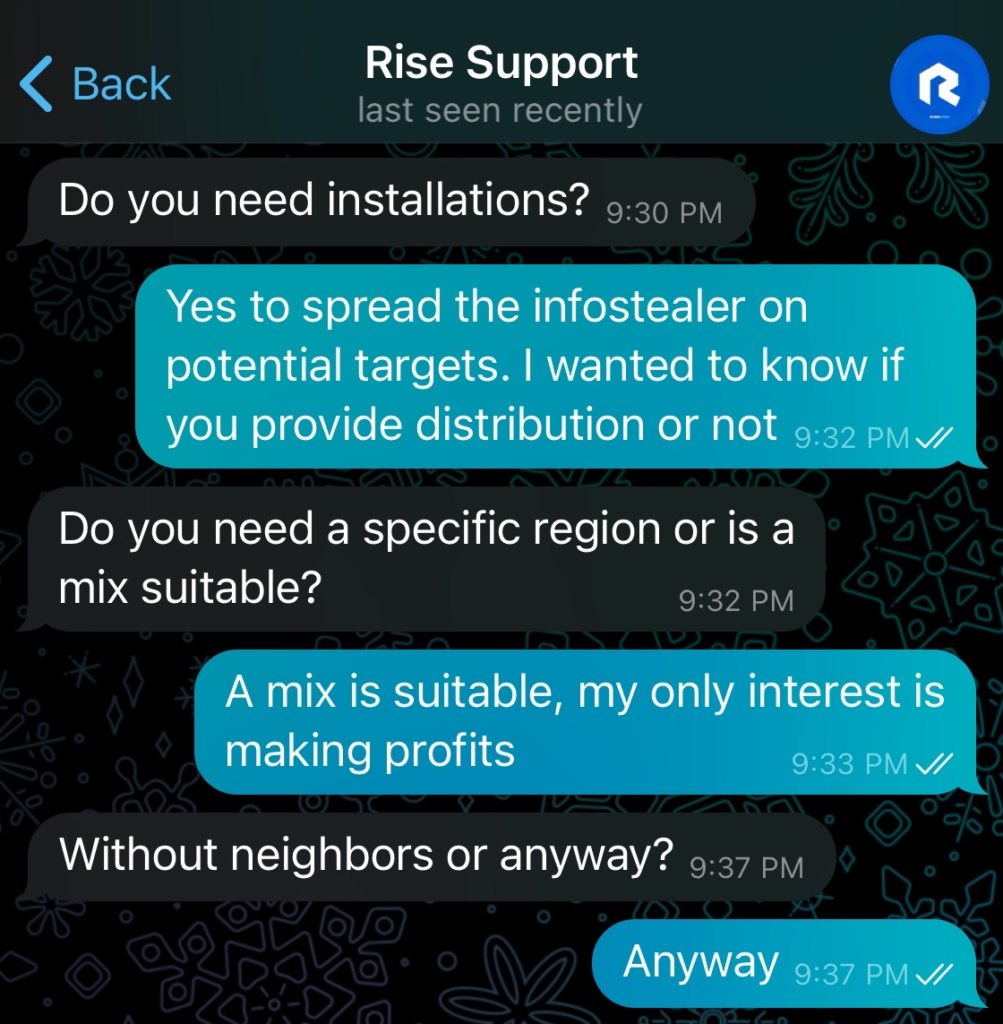
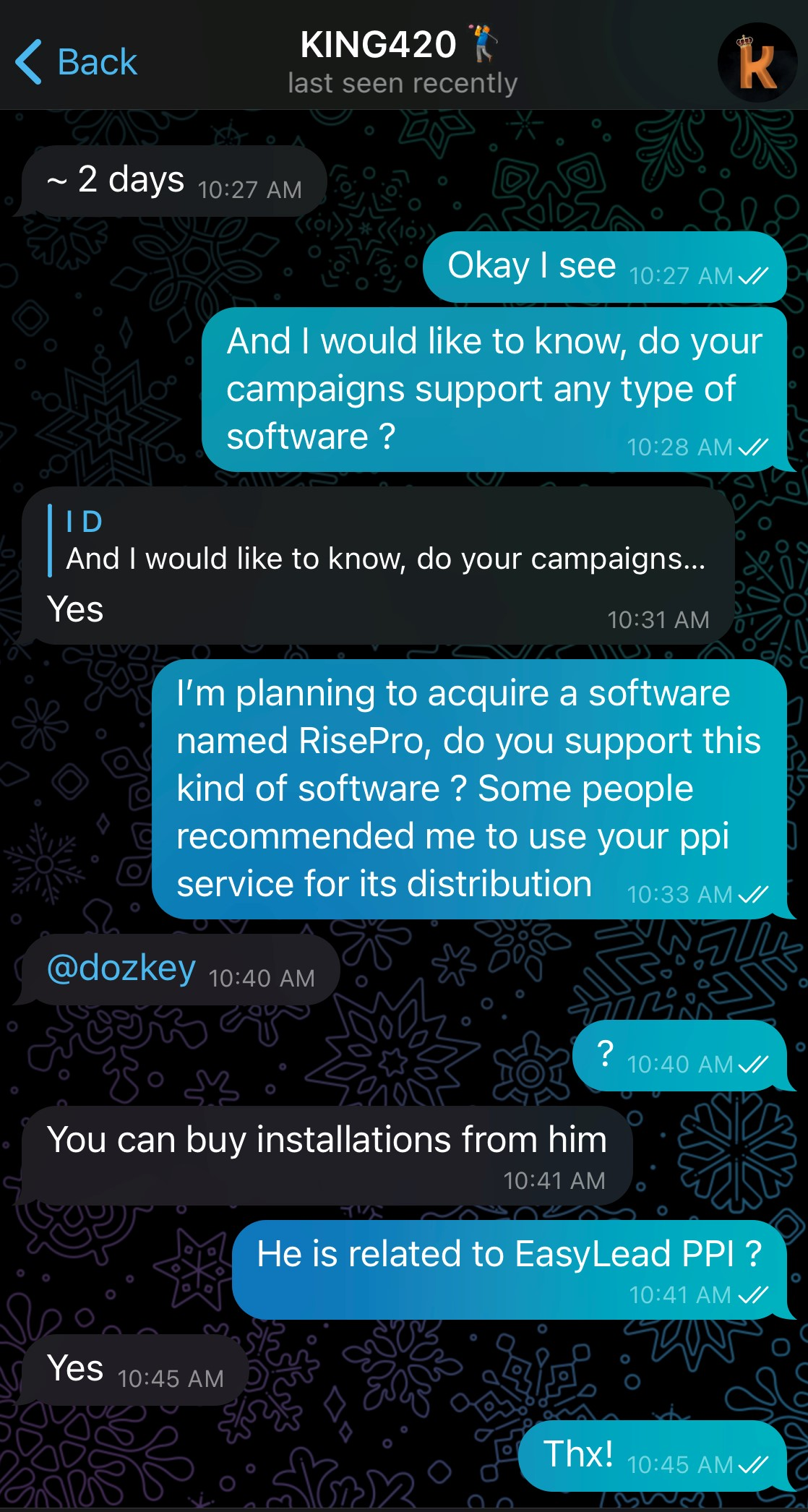
Next, I sought to determine if RisePro had any partnerships, additional services recommended by the operator to facilitate malware distribution. I mentioned PrivateLoader, as having heard about it on forums, to see if there were any suggestions. He started asking specific questions about needs, like targeted regions or server types, but interrupted, asking me to focus first on buying the infostealer.
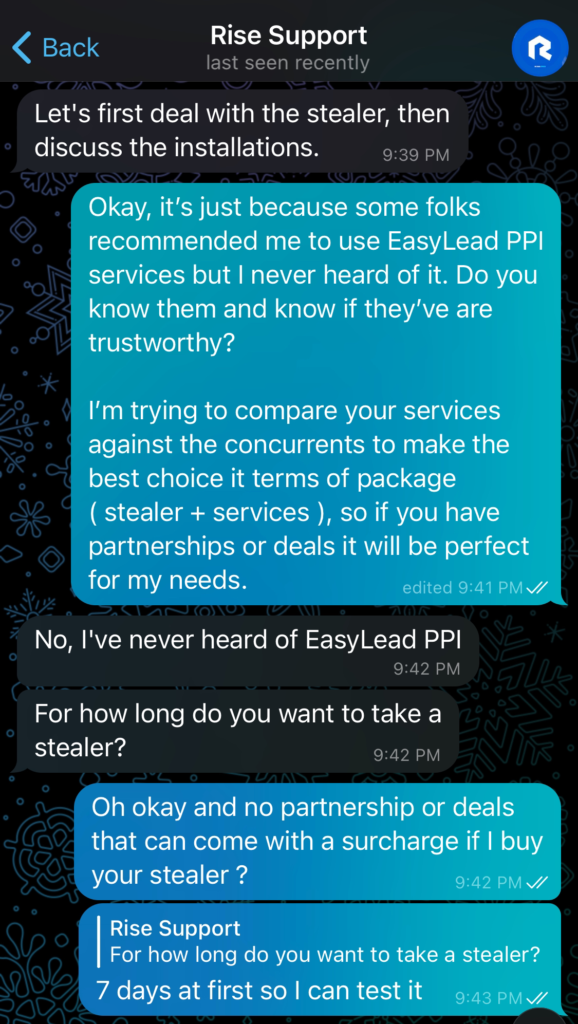
I responded affirmatively but pressed for information about EasyLead. I mentioned that some people had recommended EasyLead for malware distribution and asked for his opinion on their reliability. I explained that I was comparing different infostealers to make the best choice and that ancillary services would influence my decision. He replied that he had never heard of EasyLead, then asked which subscription I planned to take for his infostealer.
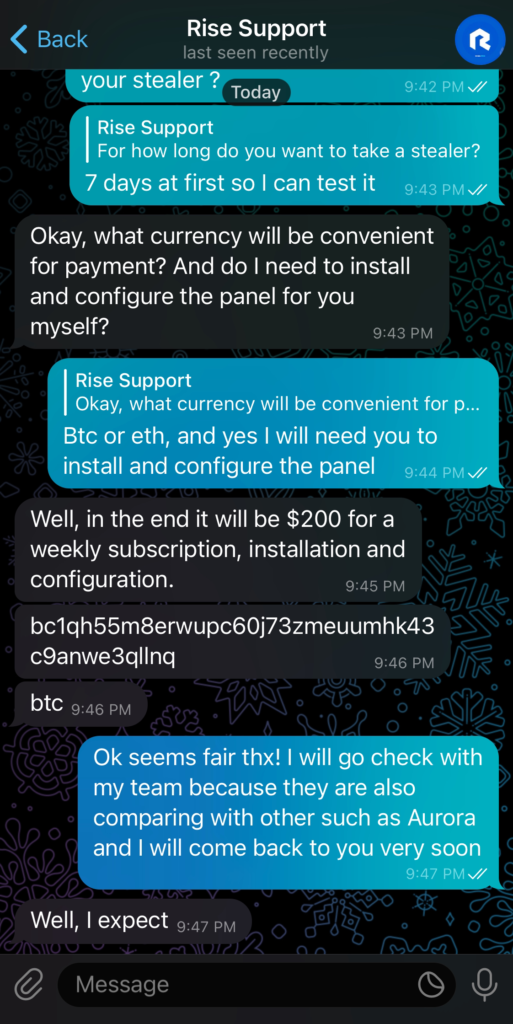
To keep up the façade as a potential client, I mentioned that I intended to subscribe for 7 days to test the infostealer. He then asked me which currency I planned to use for payment, and I replied that BTC or ETH would work for me. He also inquired whether I intended to take the additional option for him to install the C2 on my behalf. I willingly agreed, and he informed me that the total would be $200 for 1 week, inclusive of installation and configuration.
So, we now know that for the 7-day subscription, RisePro charges an additional $70 to set up the C2 on our behalf. This price likely offers more advantages with longer subscriptions to the infostealer.
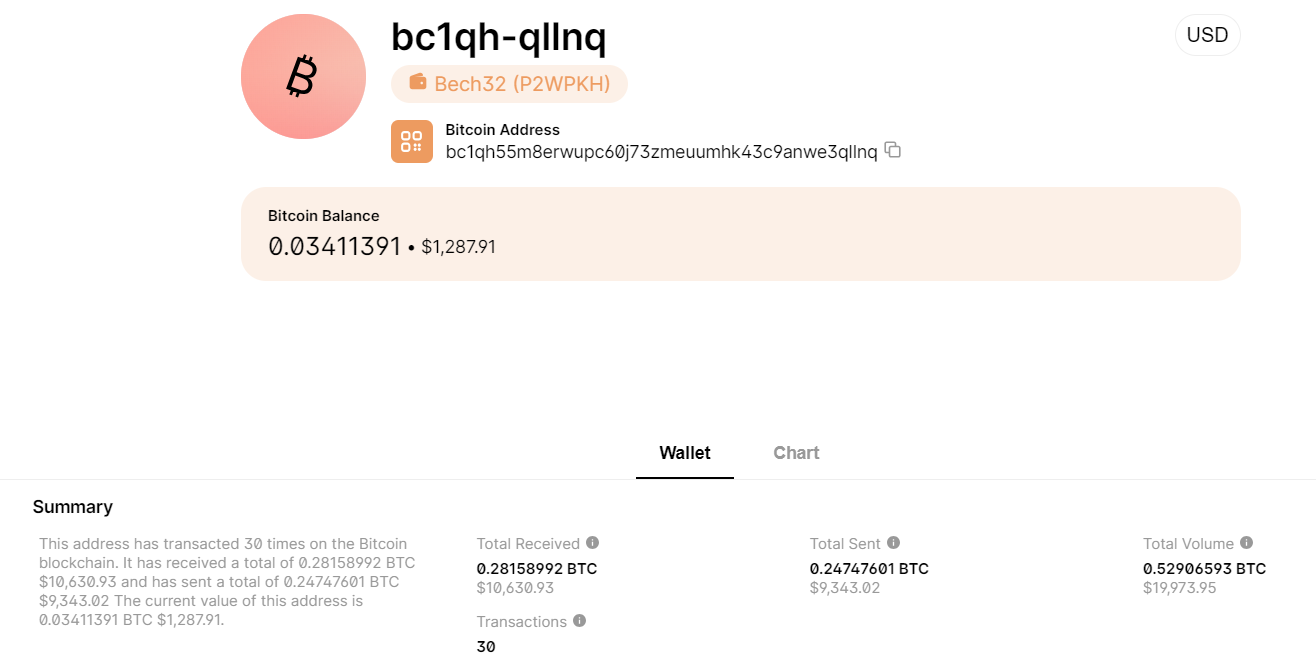
He then asks to be paid to a BTC address: “bc1qh55m8erwupc60j73zmeuumhk43c9anwe3qllnq »
Thanks to this wallet address, we discover that RisePro has generated a minimum of $10,000. There are over 17 incoming transactions associated with this address.
Contact with King420
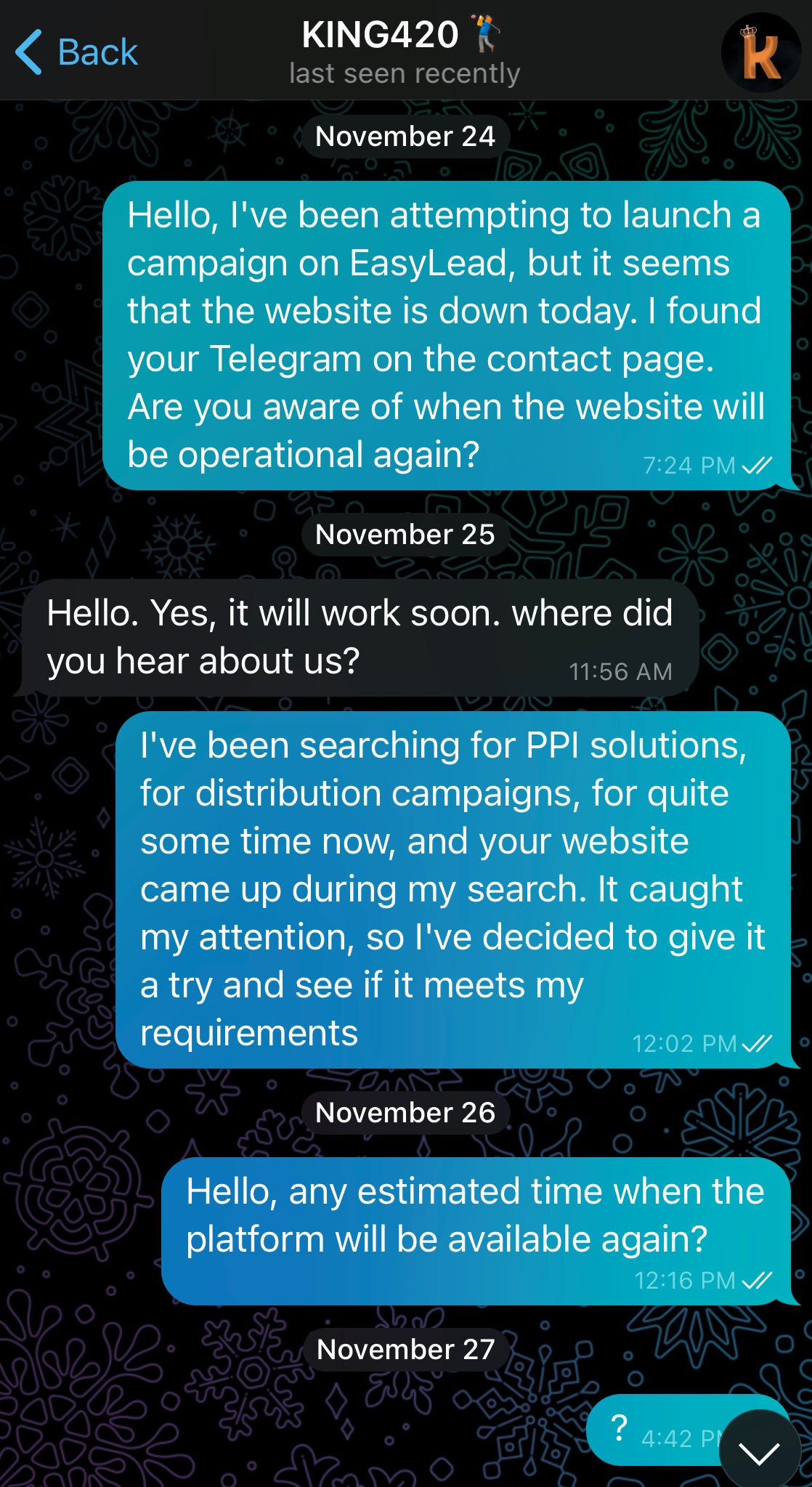
An attempt was made to contact EasyLead’s King420 with a view to exploring the links between this PPI service and RisePro. During this interaction, I adopted the role of a user of the site seeking information about its reactivation for distribution activities. At the time, the ezlead[.]pro site had been unavailable for a few days.
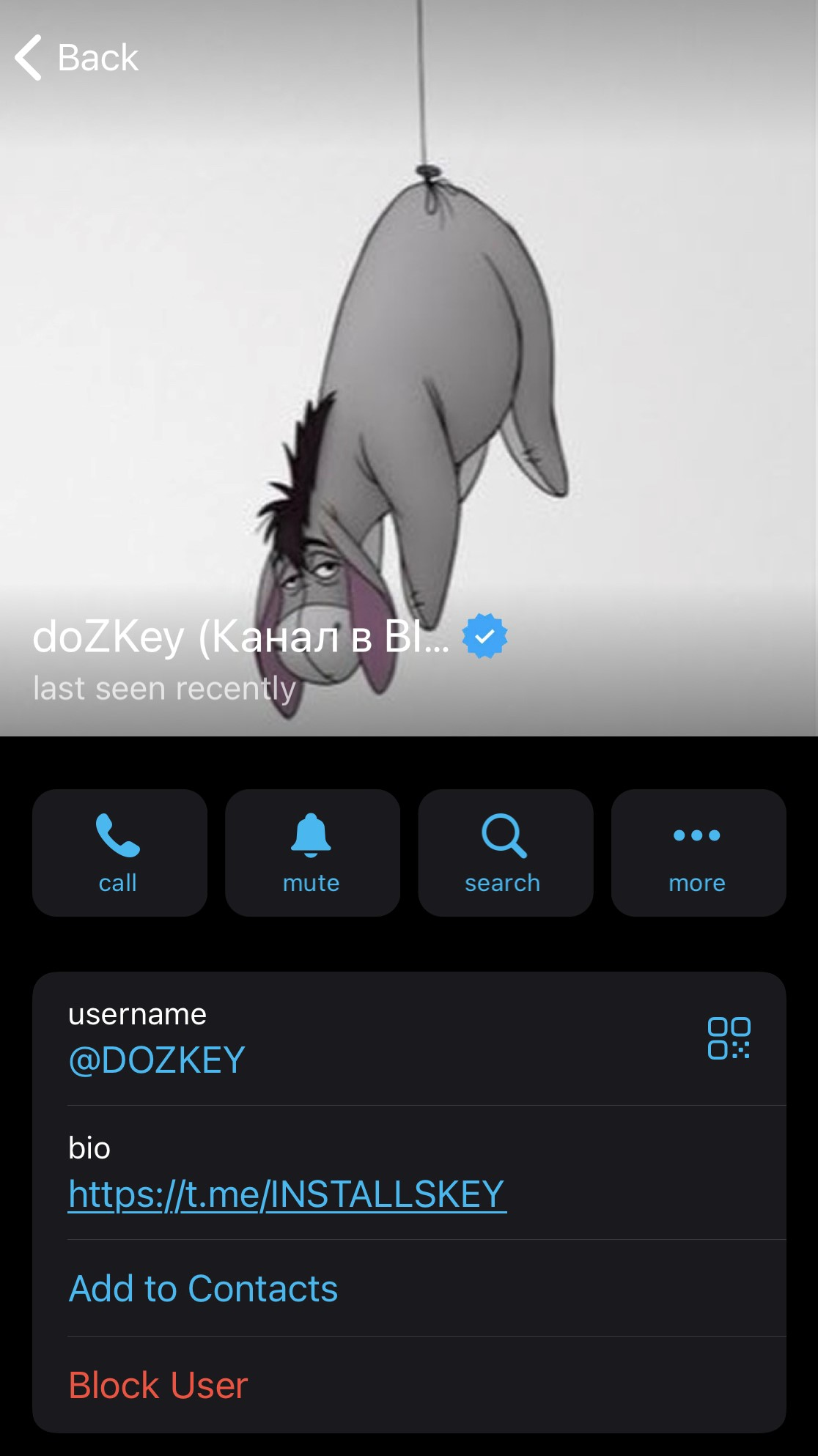
King420 took a lot of time to reply throughout our exchange. From his first reply, he seemed surprised by my knowledge of the platform. I tried to restart the conversation to obtain a date for resuming site activities. After a few days without a reply, he gave me an estimate of 2 days. It was at this point that I realized I needed to be more direct to get information. I asked him if EasyLead supported all types of software, to which he replied positively. Then I mentioned my intention to acquire RisePro and asked him if their service supported this type of “software”, pointing out that some people had recommended their services to me. He replied using another person’s pseudonym, then confirmed that this person, Dozkey, was indeed linked to EasyLead.
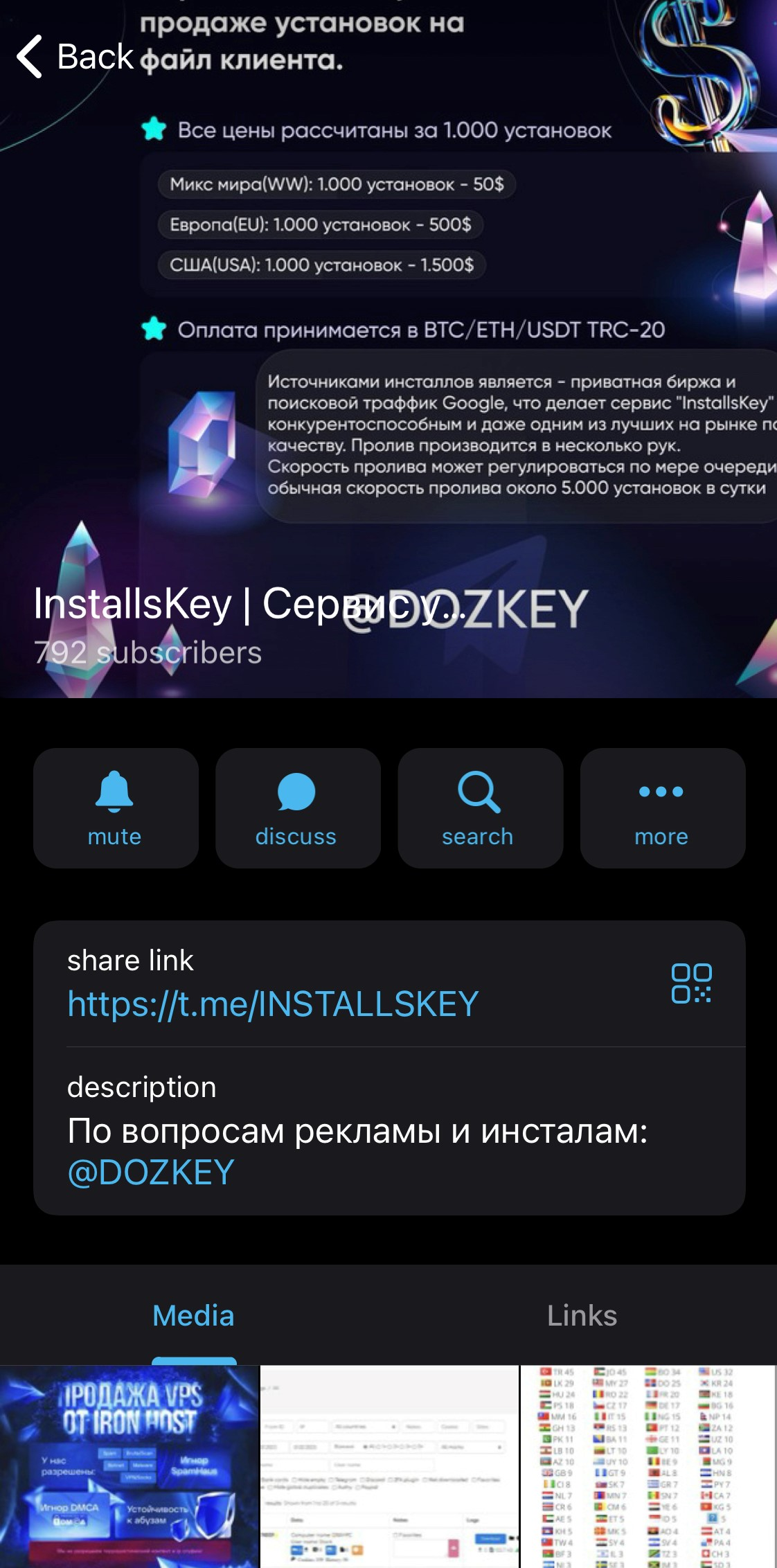
On the Dozkey account, a link to a Telegram channel named “InstallsKey” (https://t[.]me/INSTALLKEY) is visible. This Telegram channel acts as a point of sale for installations on machines around the world.
For example, on Black Friday, prices are $0.55 per install for large volumes, such as 100,000 installs for $5500 to $6000, while for small volumes, such as 10,000 installs, it’s $650 to $700.
According to a tweet from June 2023, Crep1x, CTI analyst at SEKOIA.IO, claims that PrivateLoader is employed by the Pay-Per-Install service “InstallsKey”, which is probably a redesign of the PPI service “Ruzki/zhigalsz”.
As a reminder, we believe that #PrivateLoader is the malware used by the prevalent Pay-Per-Install service "InstallsKey", which is certainly a rebranding of "Ruzki"/"zhigalsz" PPI https://t.co/eOYyZrqSqm
— crep1x (@crep1x) June 29, 2023
We could therefore assume that EasyLead is just a front for the PPI InstallsKey service, itself probably a rebranding of the PPI service Ruzki/zhigalsz.
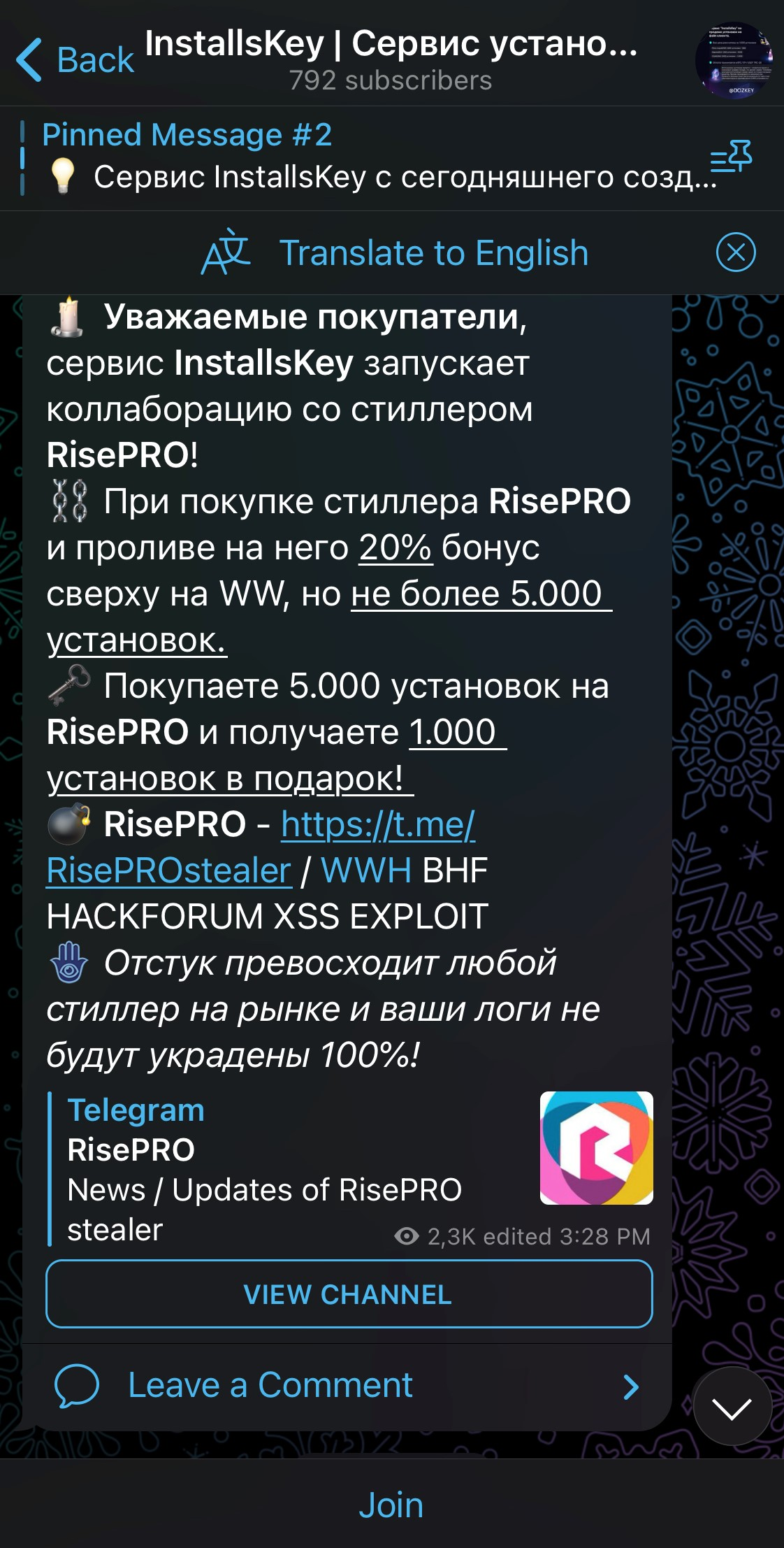
Exploring InstallsKey’s Telegram channel, a collaboration announcement with RisePro dated July 18, 2023 was spotted. The announcement states that with every purchase of RisePro, cybercriminals will receive a bonus of 20% free installations for any purchase exceeding 5000 installations.
Conclusion
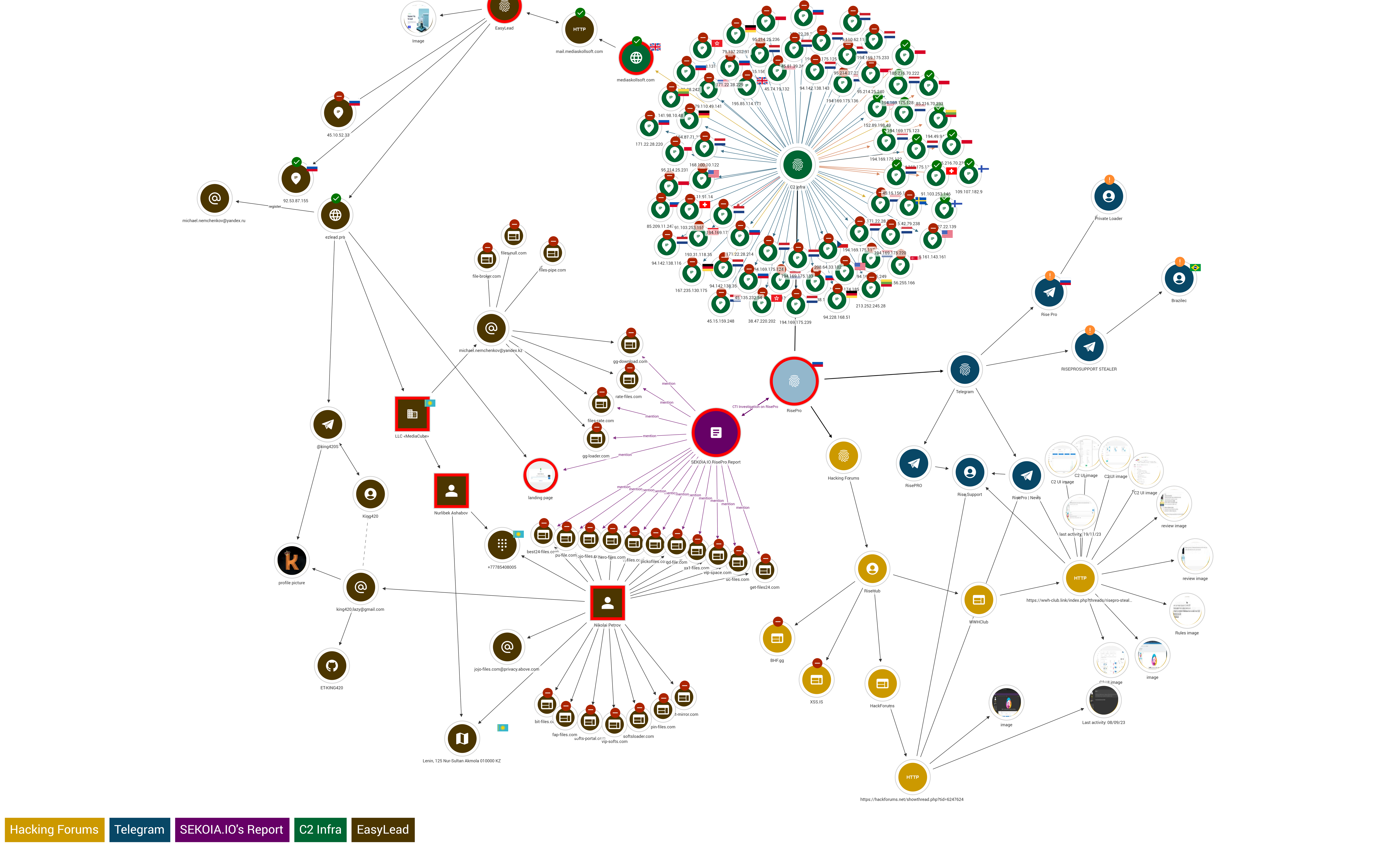
RisePro and its operator are still active, and this infostealer continues to evolve with the regular addition of new features with each update. What’s more, RiseHub remains active on various forums, and its infostealer seems to be attracting more and more new users.
In their December 2022 report, SEKOIA.IO analysts speculated that PrivateLoader had simply evolved, and that another unidentified PPI provider would offer RisePro installation via PrivateLoader. By examining the links presented in this article, it is possible to hypothesize that this “unidentified PPI provider” could be EasyLead, which is probably a front for the InstallsKey PPI service. The correlation between the domain names associated with RisePro distribution and EasyLead, as well as the design of the home pages linked to EasyLead distribution campaigns corresponding to that of PrivateLoader distribution pages, reinforces this hypothesis. What’s more, the various pieces of evidence obtained when King420 was contacted show an irrefutable link between the two cybercriminal organizations.
Despite the established links, some grey areas remain, notably concerning the precise links between the EasyLead and RisePro operators. However, we can be sure that the various CTI analysts in the sector will continue to monitor this threat to gain further knowledge, and will not hesitate to provide new information about these threat actors.
– Alb310
IoCs
RisePro C2
Active at time of investigation
- 37.27.22.139
- 45.15.156.137
- 91.103.253.146
- 109.107.182.9
- 185.216.70.222
- 185.216.70.233
- 185.216.70.238
- 194.49.94.41
- 194.169.175.113
- 194.169.175.122
- 194.169.175.123
- 194.169.175.128
- mediaskollsoft[.]com
Non-active at time of investigation
- 5.42.79.238
- 5.161.143.161
- 38.47.220.202
- 43.128.18.131
- 45.11.91.14
- 45.15.156.175
- 45.15.159.248
- 45.74.19.132
- 45.81.39.247
- 45.135.232.54
- 79.110.49.141
- 79.110.62.11
- 79.137.202.91
- 85.209.11.247
- 91.103.253.151
- 94.142.138.35
- 94.142.138.44
- 94.142.138.116
- 94.142.138.143
- 94.228.168.51
- 95.214.25.231
- 95.214.25.235
- 95.214.25.236
- 95.214.25.240
- 141.98.10.48
- 152.89.198.49
- 167.235.130.175
- 168.100.10.122
- 171.22.28.214
- 171.22.28.220
- 171.22.28.224
- 171.22.28.229
- 171.22.28.242
- 171.22.28.243
- 185.173.38.198
- 193.31.118.35
- 193.56.255.166
- 194.87.71.215
- 194.169.175.117
- 194.169.175.124
- 194.169.175.125
- 194.169.175.133
- 194.169.175.136
- 194.169.175.144
- 194.169.175.220
- 194.169.175.233
- 194.169.175.239
- 194.169.175.249
- 198.23.174.185
- 208.64.33.102
- 213.252.245.28
- 37.27.22.139
- 5.42.79.238
EasyLead
- 45.10.52.33
- 92.53.87.155
- ezlead[.]pro
- mail.mediaskollsoft[.]com
Shared domains related to Nurlibek Ashabov
- file-broker[.]com
- files-null[.]com
- files-pipe[.]com
- files-rate[.]com
- gg-download[.]com
- gg-loader[.]com
- rate-files[.]com
Shared domains related to Nikolai Petrov
- best24-files[.]com
- bit-files[.]com
- fap-files[.]com
- first-mirror[.]com
- get-files24[.]com
- hero-files[.]com
- jojo-files[.]com
- pickofiles[.]com
- pin-files[.]com
- pu-file[.]com
- qd-file[.]com
- softs-portal[.]com
- softsloader[.]com
- uc-files[.]com
- vi-files[.]com
- vip-softs[.]com
- vip-space[.]com
- xx1-files[.]com
E-mail addresses
- michael.nemchenkov[@]yandex.kz
- michael.nemchenkov[@]yandex.ru
- king420.lazy[@]gmail.com
- jojo-files.com[@]privacy.above.com
Bitcoin wallets
- bc1qh55m8erwupc60j73zmeuumhk43c9anwe3qllnq