The different visuals of malicious actors on the darkweb

It is through the prism of the visuals of the darkweb actors that we will see the different graphic identities that make up the cybercriminal groups nebula.
To be known and recognized, it is often necessary to have a unique style. Inspired by the world of advertising, these different criminal entities want to be seen, identified and recognized on different platforms, media, and social networks. How to establish a particular identity without leaving any identifying elements? It seems almost impossible as the very essence of advertising is to identify a brand to differentiate it from another.
Therefore, borrowing a graphic charter of one’s own, gives us minimal indications on the origin of these groups. In spite of their will to remain anonymous, these different digital prints can be analyzed.
It’s a simple fact that we often hear in the media the names of large ransomware groups that have hit a company, a government entity or a hospital, etc. However, little attention is paid to what kind of message these groups wanted to convey through their sites.
Among the multitude of criminal groups out there, Pyza Ransomware has published a list of over 250 identified victims on its darkweb blog. The site has been active since early April 2020. This extremely prolific group has the distinction of having a recognizable visual that sets it apart from the rest.
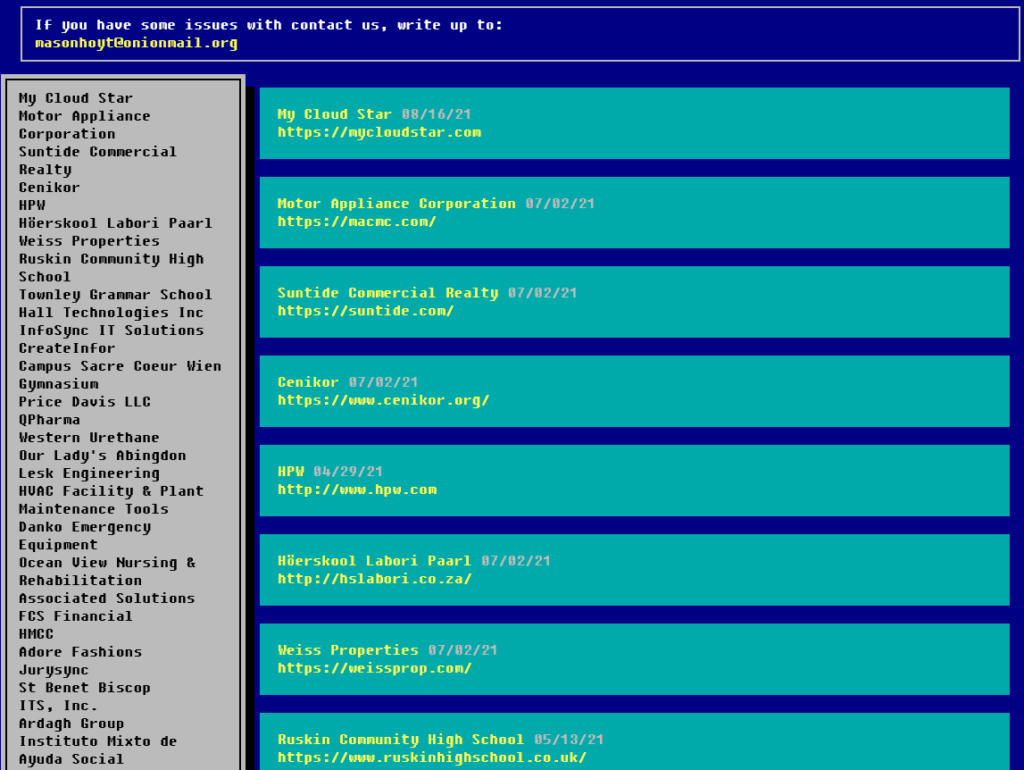
[TOR network site belonging to Pyza ransomware]
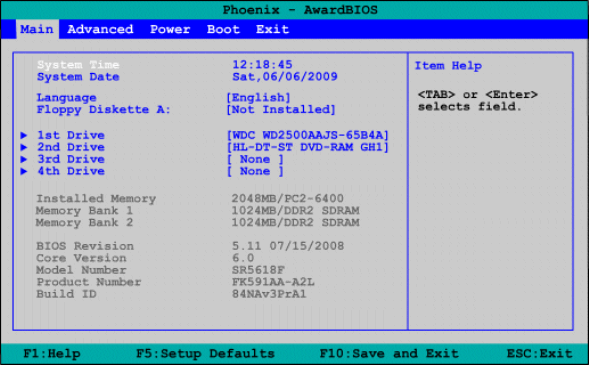
[Image from Phoenix Bios]
The site is very simple and the choice of colors is quite surprising, as they are no longer used today. The victims are placed in a simplistic listing. The design is comparable with a BIOS that existed under Windows 95-98. When we know that criminal groups related to ransomware usually attack AD (Active Directory) and compromise huge computer parks, we can easily imagine what this “BIOS” template symbolizes. It’s a way to assert the “old school hacker” side.
The BIOS is a program that starts up when your computer starts. Taking this element as a guideline is probably meant to indicate that their software remains despite the reboot of a computer. It also refers to a specific type of malware, rootkits, which are software designed to remain hidden on your computer, while allowing remote access and control of it.
These are all elements that can be interesting to keep in mind, when an attack has already been committed on your computer system and it is now time to fix it.
Another group that draws our attention is CONTI, which uses ransomware to charge victim companies. Since July 2020, more than 400 victims have been publicly listed on their site. The latter presents the data of their attacks as boxes. We get the name of the victim company, the date of the attack, the number of views and sometimes samples of stolen documents. All this is done in order to apply a psychological constraint on the companies.
The number of views implies the scope of the information propagation, and can reflect a disastrous image of the company. It is obviously possible to modify this number of views when controlling the infrastructure of the web site. These data should be taken with caution. Obviously the goal of such a group is that the information spreads as much as possible to constrain future companies caught in the stranglehold of negotiations.
Nevertheless, it is also in their best interest to limit the automated collection of their leaks for three reasons: direct exploitation makes companies want to hire cybersecurity companies to deal with the problem quickly. Automated collection of leaks makes their site vulnerable to DDOS attacks (denial of service attacks) and makes them consume resources, and finally cyber security companies could continuously collect this information, to establish a typical portrait of attackers and highlight trends, i.e. to do Cyber Threat Intelligence (CTI) and react faster to attacks from these groups.
This business model of Ransomware-as-a-Service (RaaS), consists in providing encryption software (ransomware) to hackers willing to commit computer attacks (affiliates).
CONTI’s Ransomware Blog is the criminal group’s showcase and we have to read it in two ways. Not only is it meant to constrain, but it is also meant to make a name for itself in the cybercriminal world. What could be better than a group of criminals with many victims?
It is through this type of site and advertising that the many affiliates are attracted to the various groups and can be recruited. Without this ability to show off and scare people, there would be less damage to computer networks.
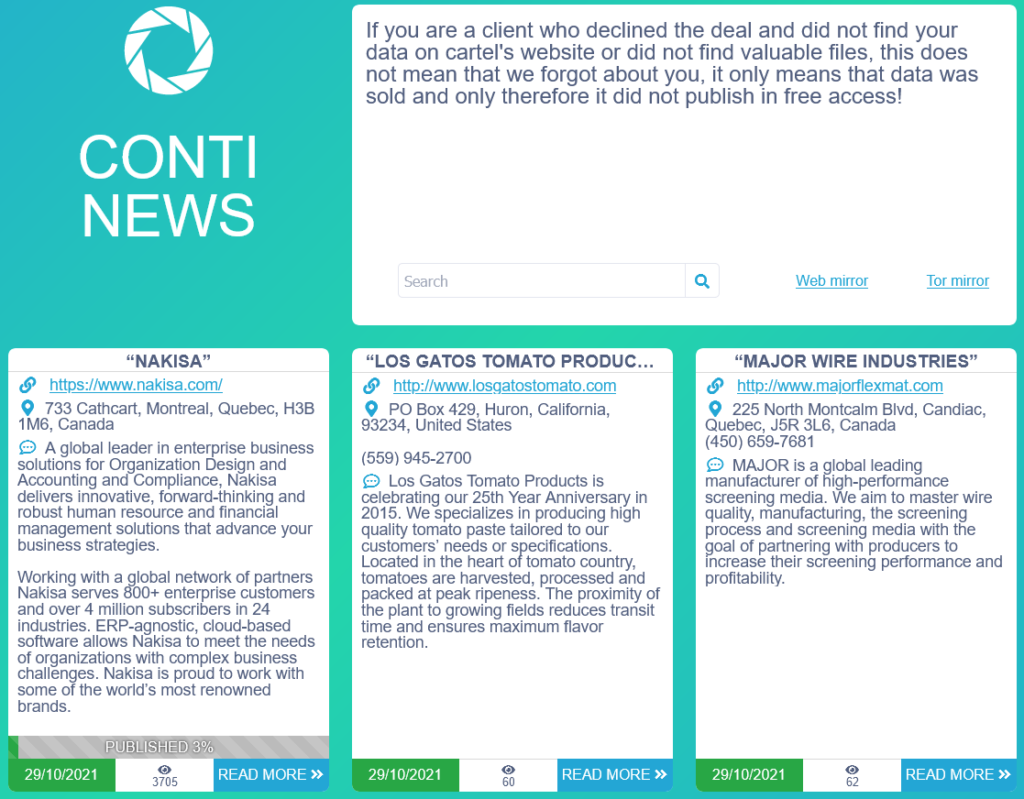
[Image from the darkweb blog of the CONTI group]
We notice the logo of Conti News. This one was borrowed from the Portal video game series, released in 2007. It is the logo of the fictional company Aperture Science, which is a research center in the Half-Life universe. Let us specify that the portal game consists in solving puzzles by using portals between different rooms. We notice the idea of passage or intrusion in different environments. It is likely that the authors could have played the game in 2007. This is an indication of the generation they belong to.

[Logo of the fictitious company Aperture]
In open source, it is possible to find an application available on the Windows Store called: “DSLR Remote Capture for Canon EOS” with a similar logo. It is an application that allows remote control of the camera’s shooting parameters using the phone via a WI-FI connection. We can notice the will of the authors to associate themselves with a logo, propagating the image of a remote control of computer systems.
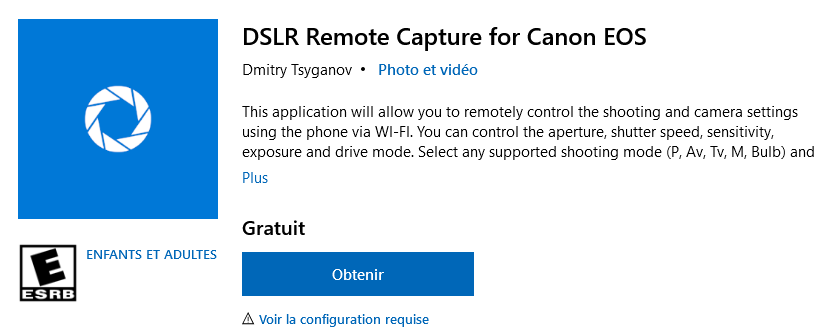
[Application from Windows Store]
The choice of colors reminds of old colored clips from the 80s. There are several templates of this site in open source. In particular :https://www.cumed.org/strategic-analysis-report-template/20-swot-analysis-templates-examples-best-practices-inside-strategic-analysis-report-template/
All this aspect of image control does not prevent internal dissonance. Let’s remember that in August 2021 an ex-affiliate of the criminal group CONTI, communicated numerous internal documents on the methodology of their attacks following an internal dispute. These documents offer a more informed view of the group for many cyber researchers.
On February 27, 2022, new leaks were published on the structure and internal discussions of the group, as well as documents extremely valuable for the structural analysis of this group. These were posted by the twitter account : @ContiLeaks.
Below is the first tweet posted by the account mentioned:
conti jabber leaks https://t.co/0FzXiXhI2d
— conti leaks (@ContiLeaks) February 27, 2022
When not dealing with ransomware actors, we can also look at marketplaces. These are sites on the TOR network, where several sellers offer illegal services. The design is inspired by more well-known sites, such as “leboncoin.fr”.
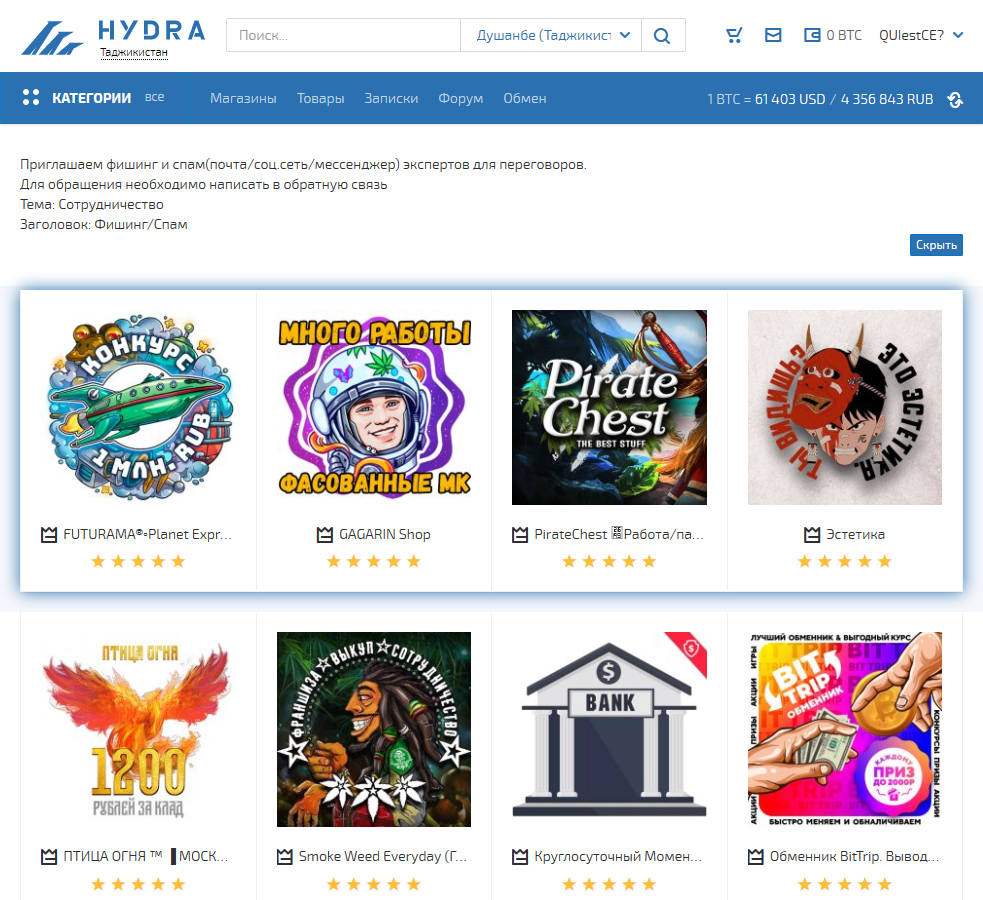
[Copy of HydraMarket website; Russian-speaking marketplace]
We note the colorful vignettes, almost infantilizing. All this is done to attract customers. There are drug sales, illegal services, VPNs, etc. Moreover, the marketing qualities of Russian illegal marketplaces, as well as drug sellers in Morbihan, for example, use the same commercial tricks.
Traces of Hydra Market’s existence exist around 2015. However, its real creation could be earlier than this date. Let’s remember that the creation of SilkRoad, the first marketplace of the dark web, dates from 2011.
On these numerous sites of sales of illegal products, there is a system of escrow, a kind of guarantor who receives the funds and waits until everything is validated to transfer the funds. A neutral party that organizes the exchanges as well as possible. As with any business, there are always dissatisfied customers, failed exchanges and unexpected events that mean that nothing goes according to plan.
As a result, there are many comments from satisfied and unsatisfied customers. So many digital traces that it is interesting to exploit.
Thus, even the most insignificant images can have a precise meaning and a purpose. The messages conveyed are as many indications on the origin of the digital traces of the dark web actors. Analyzing them one by one is a difficult task with often little results.
Very recently, on April 05, 2022 this criminal marketplace was seized by the German authorities and is currently being operated.
No lead should be neglected. All these possible sources of visual information are incriminating elements in OSINT research. It is quite possible to exploit all the digital traces left by one or several individuals, in order to reinforce the investigations.
Article written by @Daftrock
